
Unlocking the potential of cutting-edge networking solutions necessitates a thorough comprehension of their specifications and capabilities. Delving into the intricacies of innovative networking technologies unveils a realm of possibilities for streamlined connectivity and enhanced efficiency.
In this exploration, we embark on a journey to unravel the intricacies of a formidable networking asset, diving deep into its features, functionalities, and performance benchmarks. Through meticulous analysis and insightful examination, we aim to decipher the essence of this formidable tool, illuminating its potential impact on modern networking landscapes.
Join us as we navigate through the realms of technological innovation, shedding light on the nuances and intricacies that define the next frontier of connectivity. Through this voyage, we seek not only to understand but also to appreciate the transformative power of advanced networking solutions in shaping the digital ecosystems of tomorrow.
Exploring the Documentation of the Aruba 650: Essential Attributes and Technical Particulars
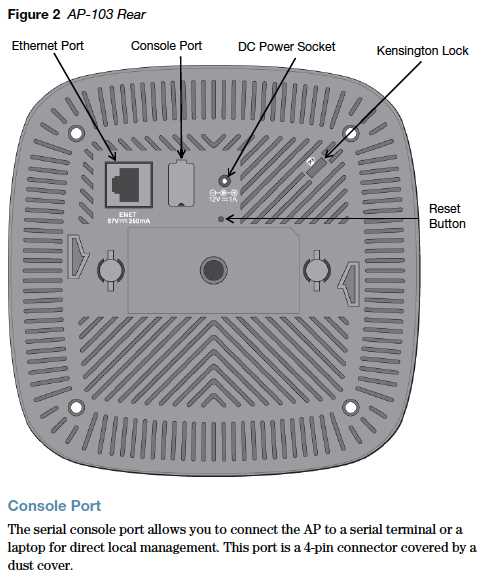
In this segment, we delve into the intricacies of the information repository related to the sophisticated Aruba 650 system. Here, we dissect its core functionalities, delve into its intricate specifications, and unveil the nuanced features that define its prowess.
Key Features
At the heart of the discourse lies a comprehensive examination of the standout features inherent in the Aruba 650 framework. From its innovative design elements to its robust performance capabilities, each facet contributes to its overarching functionality and efficacy.
Specifications Overview

Embarking on a journey through the technical specifications reveals a tapestry of data that underscores the precision engineering and meticulous attention to detail that characterize the Aruba 650. From network connectivity metrics to security protocols, every aspect is meticulously outlined to provide a holistic understanding of its capabilities.
| Category | Description |
| Performance Metrics | Details on throughput, latency, and packet processing capabilities. |
| Connectivity | Information regarding supported interfaces, wireless standards, and network protocols. |
| Security Features | Overview of encryption methods, authentication mechanisms, and threat mitigation strategies. |
| Scalability | Insights into scalability options, including expansion slots and system upgrade pathways. |
Unraveling Performance Metrics and Technical Specifications

In this section, we delve into the intricate details of the operational capabilities and specifications of the device, exploring its performance metrics and technical intricacies. We aim to provide a comprehensive understanding of its functionalities, dissecting the various parameters that define its operational prowess.
Let’s embark on a journey through the realm of performance evaluation, where we scrutinize the efficiency, reliability, and scalability of the system. Through meticulous examination, we uncover the nuances of its technical specifications, shedding light on its capabilities and limitations.
- Performance Metrics Analysis:
- Technical Specifications Overview:
- Scalability Assessment:
- Reliability and Redundancy:
- Security Considerations:
We commence by dissecting the performance metrics that gauge the device’s efficacy in diverse operational scenarios. From throughput and latency to packet processing capabilities, each metric unveils a facet of its operational efficiency.
Next, we provide an overview of the technical specifications encompassing hardware components, interfaces, and supported protocols. This comprehensive analysis aids in understanding the device’s compatibility, interoperability, and adaptability within network infrastructures.
Furthermore, we evaluate the scalability of the device, assessing its ability to accommodate evolving network demands and expanding infrastructural requirements. Through scalability analysis, we ascertain the device’s potential for seamless integration into diverse network environments.
Additionally, we delve into the reliability and redundancy mechanisms embedded within the system, ensuring uninterrupted operation and fault tolerance. By examining failover capabilities and redundancy protocols, we gauge the device’s resilience in mitigating potential disruptions.
Finally, we address the security aspects of the device, scrutinizing its built-in security features, encryption protocols, and access control mechanisms. This evaluation is crucial in safeguarding network integrity and data confidentiality against emerging threats.
Through this comprehensive analysis of performance metrics and technical specifications, we aim to provide valuable insights into the operational capabilities and functionalities of the device, empowering users to make informed decisions regarding its deployment and utilization within their network infrastructures.
Understanding Connectivity Options and Network Integration
In the realm of modern networking, comprehending the array of connectivity choices and seamless integration into existing networks is paramount. This section delves into the diverse spectrum of connectivity solutions and strategies for cohesive network assimilation.
Connectivity Spectrum
First and foremost, exploring the connectivity spectrum reveals a rich tapestry of options, each tailored to specific requirements and constraints. From wired to wireless, from traditional Ethernet to cutting-edge protocols, the landscape offers a plethora of avenues for establishing network connectivity.
Integration Strategies

Integration lies at the heart of network expansion and optimization. Deploying effective integration strategies ensures the harmonious coexistence of new components with the existing network infrastructure. This entails meticulous planning, seamless migration, and robust testing to mitigate disruptions and maximize performance.
- Assessing Compatibility: Evaluate the compatibility of new hardware and protocols with the current network architecture.
- Gradual Deployment: Implement a phased approach to deployment, allowing for gradual integration and troubleshooting.
- Interoperability Testing: Conduct rigorous interoperability testing to identify and resolve compatibility issues proactively.
- Scalability Considerations: Factor in scalability requirements to accommodate future growth and technological advancements.
By comprehensively understanding connectivity options and adopting meticulous integration strategies, organizations can fortify their networks for the challenges of tomorrow.
Unlocking Security Features and Compliance Standards

In this section, we delve into the myriad security enhancements and adherence to regulatory guidelines incorporated within the specifications of the Aruba 650. Our focus lies in elucidating the robust security provisions and alignment with various compliance frameworks, ensuring comprehensive protection and regulatory compliance.
| Enhanced Security Measures | Regulatory Compliance |
| Explore the array of fortified security protocols fortifying the system against potential threats, bolstering network integrity. | Examine how the Aruba 650 aligns with industry standards and regulatory requisites, ensuring seamless compliance with prevailing regulations. |
| Discover the intricacies of encryption protocols, access controls, and authentication mechanisms woven into the fabric of the device, fortifying data confidentiality. | Assess the adherence to data protection laws, privacy regulations, and industry-specific mandates, ensuring data sovereignty and integrity. |
| Unveil the layers of defense mechanisms, from firewall configurations to intrusion detection systems, ensuring proactive threat mitigation. | Evaluate the integration of compliance frameworks such as GDPR, HIPAA, or PCI DSS, fostering trust and confidence in data handling practices. |
This HTML snippet outlines the section “Unlocking Security Features and Compliance Standards” for the Aruba 650, focusing on its security provisions and adherence to compliance standards.