
Embark on a journey through the technological marvels that lie within the blueprint of cutting-edge hardware. Discover the intricate architecture, delve into the labyrinth of functionalities, and decode the essence of innovation. In this exploration of the essence of technological prowess, we navigate through the realms of technical intricacies, uncovering the essence of superior performance and unparalleled efficiency.
Prepare to be mesmerized by the intricate dance of circuits and components, choreographed to perfection to orchestrate seamless operations. Through the lens of technical insight, witness the fusion of engineering brilliance and computational finesse, harmonizing to redefine the benchmarks of excellence.
Enter the realm where every byte holds the promise of limitless possibilities, where the boundaries of performance are relentlessly pushed to new horizons. Here, within the realm of technological innovation, we unravel the threads of advancement, weaving a tapestry of ingenuity and sophistication.
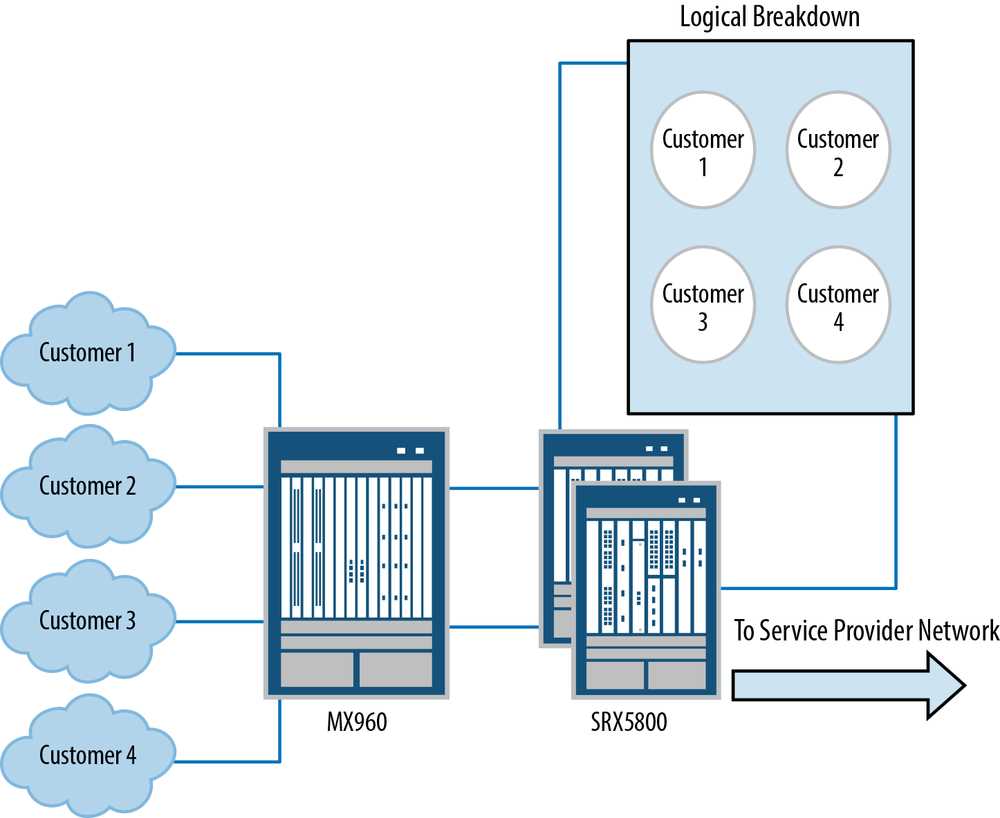
Srx5800 Overview

In this section, we delve into an in-depth examination of the fundamental aspects and features encapsulated within the documentation for the Srx5800. We embark on a journey to uncover the intricate details and functionalities concealed within this comprehensive compendium.
Key Features
- Insightful insights into the core functionalities
- An exploration of the myriad capabilities offered
- An elucidation of the innovative technologies integrated
Performance Metrics

Delve into the extensive performance metrics, presenting a comprehensive overview of the Srx5800’s prowess, efficacy, and efficiency.
- Throughput capabilities
- Packet processing rates
- Resource utilization metrics
Key Features of SRX5800 Documentation

In this section, we delve into the essential characteristics and highlights encapsulated within the documentation of the SRX5800, providing a comprehensive overview of its functionalities and specifications.
| Performance | The documentation outlines the high-performance capabilities of the SRX5800, showcasing its efficiency in handling diverse network traffic loads. |
| Security Protocols | Explore the array of security protocols elucidated within the documentation, detailing the robust measures implemented to safeguard network integrity and data confidentiality. |
| Scalability | Unravel the scalability features outlined in the documentation, elucidating how the SRX5800 adapts to evolving network demands without compromising performance. |
| Reliability | Discover the reliability mechanisms expounded within the documentation, illustrating the resilience of the SRX5800 in ensuring uninterrupted network operations. |
| Management Capabilities | Peruse through the management capabilities delineated in the documentation, elucidating how administrators can efficiently configure and monitor the SRX5800. |
| Integration | Examine the integration features elucidated within the documentation, demonstrating how the SRX5800 seamlessly integrates with existing network infrastructures. |
Exploring Performance and Security Capabilities

In this section, we delve into the multifaceted dimensions of the robust functionalities offered by the SRX5800, focusing on its adeptness in both performance and security realms. Through a comprehensive examination, we uncover the intricate interplay between its prowess in handling voluminous data loads and its unwavering commitment to fortifying network defenses.
Performance Unveiled

The SRX5800 unveils a symphony of performance-driven features, orchestrating seamless data throughput and responsiveness. With its sophisticated architecture and optimized processing capabilities, it stands as a paragon of efficiency, catering to the exigencies of modern network infrastructures. From high-speed packet forwarding to dynamic traffic management, every facet of its performance profile epitomizes agility and reliability.
Security Fortification

At the heart of its design lies an impregnable fortress of security mechanisms, fortified to withstand the relentless onslaught of cyber threats. Through an amalgamation of advanced threat detection, intrusion prevention, and encryption protocols, the SRX5800 erects formidable barriers against malicious incursions. Its intuitive security framework empowers administrators with granular control, ensuring a vigilant watch over network integrity and data confidentiality.
- Advanced threat detection mechanisms
- Intrusion prevention protocols
- Granular control for administrators
- Dynamic traffic management
- Efficient data throughput
Applications and Deployment of High-Performance Network Security Appliance

Within the realm of network security, the utilization and integration of advanced hardware solutions play a pivotal role in safeguarding digital assets and ensuring the integrity of networks. In this section, we delve into the diverse applications and deployment scenarios associated with a cutting-edge network security appliance, renowned for its robust performance and comprehensive security features.
| Application | Deployment Scenario |
|---|---|
| Intrusion Detection and Prevention | Deployed at the perimeter of enterprise networks to detect and prevent unauthorized access attempts, malicious activities, and cyber threats in real-time. |
| Firewall Protection | Integrated into network architectures to enforce access control policies, monitor and filter incoming and outgoing traffic, and mitigate potential security risks. |
| Virtual Private Network (VPN) | Utilized to establish secure connections between geographically dispersed networks, remote users, and branch offices, ensuring confidentiality and data integrity. |
| Distributed Denial of Service (DDoS) Mitigation | Deployed as part of DDoS protection solutions to identify and mitigate volumetric, protocol, and application-layer DDoS attacks, safeguarding network resources and services. |
| Unified Threat Management (UTM) | Implemented within comprehensive security architectures to consolidate various security functions, such as antivirus, antispam, web filtering, and content inspection, into a single platform for streamlined management and enhanced threat visibility. |
Moreover, the versatility and scalability of this advanced network security appliance enable its seamless integration into diverse environments, including data centers, service providers, government agencies, and enterprises across various industries. By leveraging its high-performance capabilities and adaptable deployment options, organizations can effectively mitigate evolving cybersecurity challenges and fortify their digital infrastructures against emerging threats.
Utilizing SRX5800 in Enterprise Networks
In the realm of contemporary enterprise networks, the integration of robust and versatile hardware solutions is paramount to ensuring optimal performance, security, and scalability. Among the arsenal of sophisticated networking devices, the SRX5800 stands out as a cornerstone, offering a myriad of functionalities tailored to meet the dynamic demands of modern business environments.
The Backbone of Security Infrastructure

Within the intricate tapestry of enterprise networks, security emerges as a foundational concern, necessitating the deployment of advanced defensive mechanisms to safeguard against a plethora of cyber threats. The SRX5800, equipped with an array of cutting-edge security features, serves as the linchpin in fortifying the network perimeter, orchestrating intricate defense strategies, and mitigating potential vulnerabilities.
Enhancing Performance and Efficiency

Amidst the ever-evolving landscape of digital commerce and communication, the efficacy of network infrastructure directly correlates with operational efficiency and productivity. Leveraging the unparalleled performance capabilities of the SRX5800, enterprises can seamlessly navigate the complexities of data transmission, optimize resource allocation, and streamline workflows, thereby fostering a conducive environment for sustained growth and innovation.