Dive into the realm of this groundbreaking document as we embark on a journey to uncover the essence and capabilities of the Panorama Palo Alto Datasheet. Brace yourself for an informational voyage that will leave you with an unparalleled understanding of this innovation.
Within these pages, a treasure trove of knowledge awaits, enabling you to explore the intricacies and nuances of this cutting-edge solution. As you delve deeper, you will discover a wealth of information that will empower you to make informed decisions and grasp the full potential of this robust platform.
Prepare to feast your eyes on an array of features intricately woven together, seamlessly enhancing your understanding of this dynamic document. Immerse yourself in a world of technical prowess, where every line and word holds significance, providing the building blocks for your path to success.
With its articulate prose and impeccably curated content, this datasheet exudes confidence, leaving no stone unturned as it pulls back the curtain on the intricacies of the Panorama Palo Alto Datasheet. From the moment you embark on this journey, you will be captivated by the sheer depth and breadth of information presented, solidifying its position as an indispensable tool in your arsenal.
Enhance Your Network Security with Panorama Palo Alto
Are you looking to strengthen the security of your network and protect sensitive data from cyber threats? Look no further than Panorama Palo Alto, a comprehensive network security solution that offers advanced features and functionalities.
Streamline and Centralize Network Management
With Panorama Palo Alto, you can streamline and centralize the management of your network security infrastructure. Gone are the days of manually configuring and monitoring multiple security devices scattered across your network. Now, you can efficiently manage everything from a single centralized platform.
By consolidating network security management, you gain better visibility into your entire network, allowing you to identify potential vulnerabilities and quickly respond to security incidents. Panorama Palo Alto provides easy-to-use dashboards, real-time monitoring, and proactive threat intelligence, enabling you to take proactive measures to enhance your network security.
Enhanced Threat Detection and Prevention
When it comes to protecting your network from threats, Panorama Palo Alto goes beyond traditional firewall solutions. It employs advanced threat detection and prevention techniques, such as machine learning, behavioral analysis, and threat intelligence, to identify and block both known and unknown threats.
With Panorama Palo Alto, you can create customized security policies that adapt to your organization’s specific needs. It allows you to define granular access controls, detect and block malicious activities in real-time, and automatically update security policies based on the latest threat intelligence.
- Gain comprehensive visibility into network traffic
- Detect and block advanced threats with machine learning
- Create customized security policies based on real-time analysis
- Easily update security policies based on the latest threat intelligence
In conclusion, Panorama Palo Alto is a powerful network security solution that enhances your network security by streamlining management and offering advanced threat detection and prevention capabilities. With Panorama Palo Alto, you can confidently protect your network from a wide range of cyber threats, ensuring the safety and integrity of your data.
Seamless Centralized Management

Effortlessly streamline and oversee your network operations with the innovative Seamless Centralized Management feature. By consolidating and unifying all your network management tasks into a single platform, you can efficiently supervise and control various aspects of your network infrastructure without any hassle.
With this cutting-edge functionality, you can seamlessly coordinate and manage your network resources, ensuring optimal performance and reliability. Whether it’s configuring network devices, monitoring traffic, or implementing security policies, our Seamless Centralized Management empowers you to effortlessly handle these tasks with ease.
Furthermore, the Seamless Centralized Management feature offers a user-friendly interface, enabling intuitive navigation and simplified administration. Through this streamlined approach, you can save significant time and effort, allowing you to focus on critical network management tasks.
Moreover, this centralized management solution fosters enhanced collaboration among your team members. With its seamless integration capabilities, you can easily share information, delegate responsibilities, and coordinate efforts, promoting efficient teamwork and productivity.
In conclusion, the innovative Seamless Centralized Management feature revolutionizes network management, providing a unified platform that simplifies administrative tasks, promotes collaboration, and boosts overall network performance. Unlock the benefits of this advanced functionality and experience a seamless and efficient approach to managing your network infrastructure.
Comprehensive Visibility and Control

In today’s rapidly evolving digital landscape, it is crucial for organizations to have a comprehensive understanding and management of their network security. This entails gaining complete visibility into network traffic, allowing for proactive detection and response to potential threats, and maintaining control over data and access. By ensuring comprehensive visibility and control, businesses can safeguard their critical assets, mitigate risks, and ensure a seamless and secure network environment.
By achieving comprehensive visibility, organizations can gain a holistic view of their network infrastructure, including all endpoints, applications, and user behavior. This visibility enables them to identify and analyze potential vulnerabilities, anomalous activities, and emerging threats that could compromise their security posture. With this knowledge, businesses can effectively prioritize and respond to incidents, reducing their risk exposure and minimizing the impact of potential breaches.
Ensuring comprehensive control over network resources and access is equally important. This involves implementing robust security policies, access controls, and monitoring capabilities to prevent unauthorized access and data breaches. Organizations can establish granular control over user privileges, restrict access to sensitive information, and enforce compliance with regulatory requirements. By maintaining control over network resources and access, companies can proactively mitigate security risks and protect their valuable data.
Comprehensive visibility and control go hand in hand, forming a cohesive security framework that enables organizations to anticipate, detect, and respond to evolving threats. This entails deploying advanced security solutions, such as next-generation firewalls and intrusion detection systems, that provide real-time visibility into network traffic and enable proactive threat identification and mitigation. Combined with robust access controls and monitoring capabilities, businesses can create a secure and resilient network infrastructure that protects their assets and ensures business continuity.
In conclusion, comprehensive visibility and control are crucial elements of effective network security. By gaining a holistic understanding of their network environment and implementing robust access controls and monitoring capabilities, organizations can proactively detect and respond to potential threats, safeguard their critical assets, and ensure a seamless and secure network environment.
Streamlined Security Operations
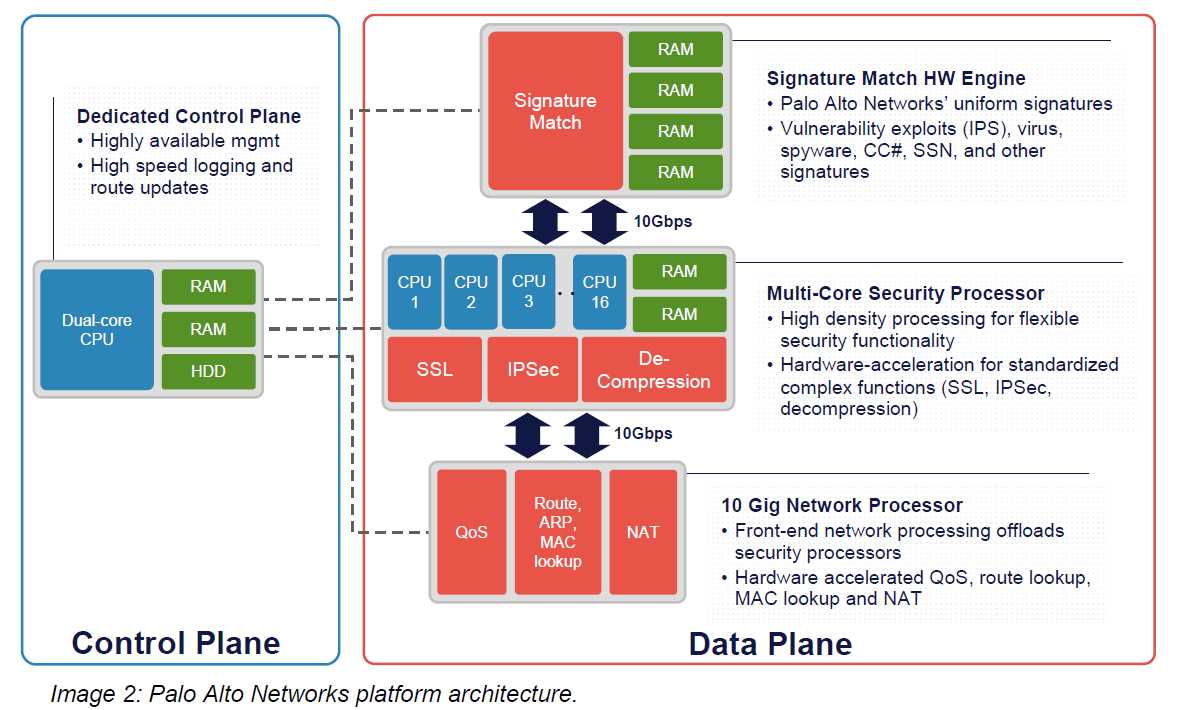
Enhancing the efficiency and effectiveness of security operations is a critical aspect of any modern organization. The ability to efficiently manage and respond to security threats is paramount in maintaining the integrity and confidentiality of sensitive data. In this section, we explore the various strategies and solutions that can streamline security operations, improving overall productivity and reducing response times.
The Power of Automation

One key element in streamlining security operations is the implementation of automation. By automating repetitive and time-consuming tasks, security teams can focus their efforts on more critical and complex issues. Automation can accelerate incident detection and response, minimizing the impact of security breaches and enabling faster resolution. Additionally, automation can improve accuracy in threat analysis and reduce the margin of human error, leading to more reliable and efficient security operations.
Centralized Management and Visibility
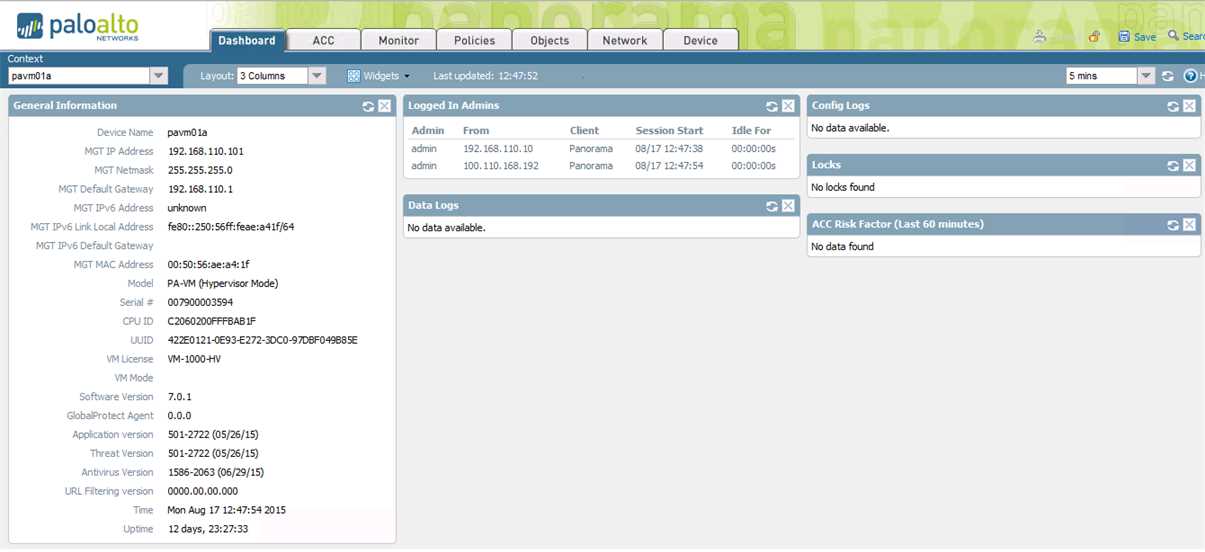
Achieving streamlined security operations requires a centralized management and visibility platform. By consolidating security tools and data into a unified interface, organizations can gain a comprehensive understanding of their security posture. This centralized approach simplifies policy management, enables faster deployment of updates and patches, and provides real-time insights into network activity and threat intelligence. With improved visibility, security teams can proactively identify and address vulnerabilities, ensuring a robust and resilient security infrastructure.
Emerging technologies such as machine learning and artificial intelligence play a pivotal role in streamlining security operations. Leveraging these technologies can enable predictive analysis, allowing organizations to anticipate and mitigate potential threats before they materialize. Intelligent automation and adaptive response mechanisms further enhance security operations by dynamically adjusting security measures in response to evolving threats.
By embracing a streamlined approach to security operations, organizations can optimize their resource utilization, reduce costs, and enhance their overall security posture. Through automation, centralized management, and the incorporation of emerging technologies, security teams can effectively mitigate risks, prevent breaches, and respond swiftly and decisively to incidents.