
In this era of constantly-evolving digital landscapes, safeguarding your organization’s critical assets has become more crucial than ever before. The integration of advanced technological solutions has ushered in new paradigms and terminologies that have forever changed the dynamics of enterprise-level protection.
In a world where fortifying your systems against a myriad of threats has become synonymous with survival, it is imperative to explore the realm of ‘atmospheric defense.’ By comprehensively fortifying the various layers of your digital infrastructure, you can establish an impenetrable line of defense against malicious actors constantly seeking to destabilize your operations and compromise your vital data.
Widening the scope of our security protocol, the Compendium of Secure Cyber Boundaries presents a game-changing solution that provides unparalleled endpoint protection. Our cutting-edge technology redefines the limits of conventional security measures, empowering organizations to operate with complete peace of mind while mitigating risks and minimizing potential disruptions.
Within this thought-provoking compendium, we delve into the intricacies of establishing secure boundaries around your organization’s digital ecosystem. Through a comprehensive exploration of effective strategies, best practices, and transformative case studies, we equip decision-makers and security professionals with the knowledge necessary to safeguard their invaluable assets from a plethora of stealthy threats.
What is Cloud One Endpoint Security?
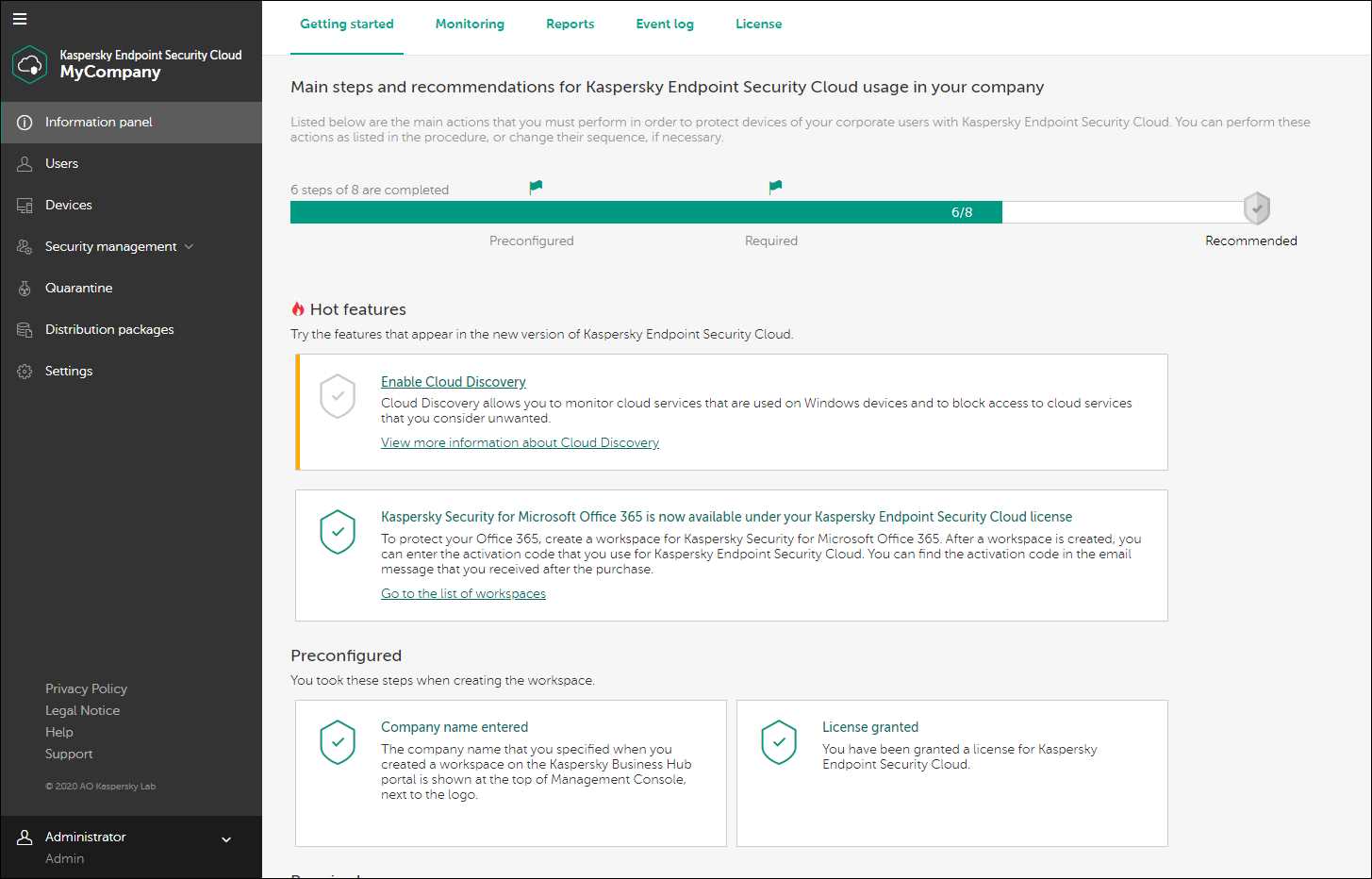
Discover comprehensive protection for your devices and networks with Cloud One Endpoint Security. This cutting-edge solution is designed to safeguard your systems against cyber threats, ensuring the confidentiality, integrity, and availability of your data. By utilizing advanced technologies and intelligent algorithms, Cloud One Endpoint Security offers a powerful defense mechanism that acts as a shield against unauthorized access, malware, and other malicious activities.
Comprehensive Device Protection
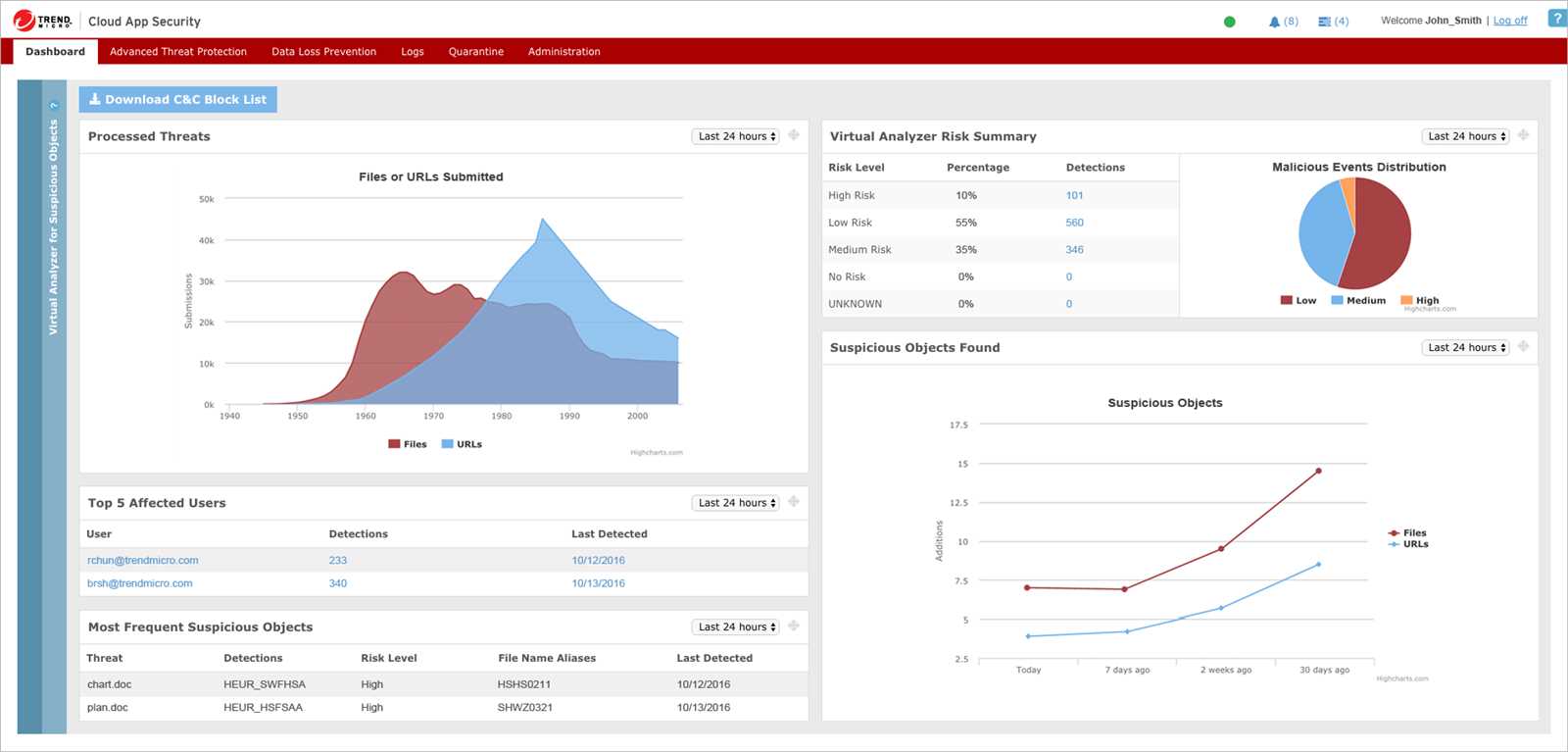
Cloud One Endpoint Security provides a holistic approach to securing your devices, including desktops, laptops, and mobile devices. It utilizes a combination of proactive and reactive measures to identify and mitigate potential threats, ensuring that your devices are protected from both known and unknown risks.
Network Security Integration

Seamlessly integrated with your network infrastructure, Cloud One Endpoint Security not only safeguards individual devices but also strengthens the overall security of your network. By monitoring and analyzing network traffic, it can detect and prevent suspicious activities, helping you maintain a secure and resilient network environment.
With Cloud One Endpoint Security, you can rest assured that your devices and networks remain protected, allowing you to focus on your core business activities without worrying about cyber threats. Experience the peace of mind that comes with robust and sophisticated endpoint security.
Benefits of Cloud One Endpoint Security
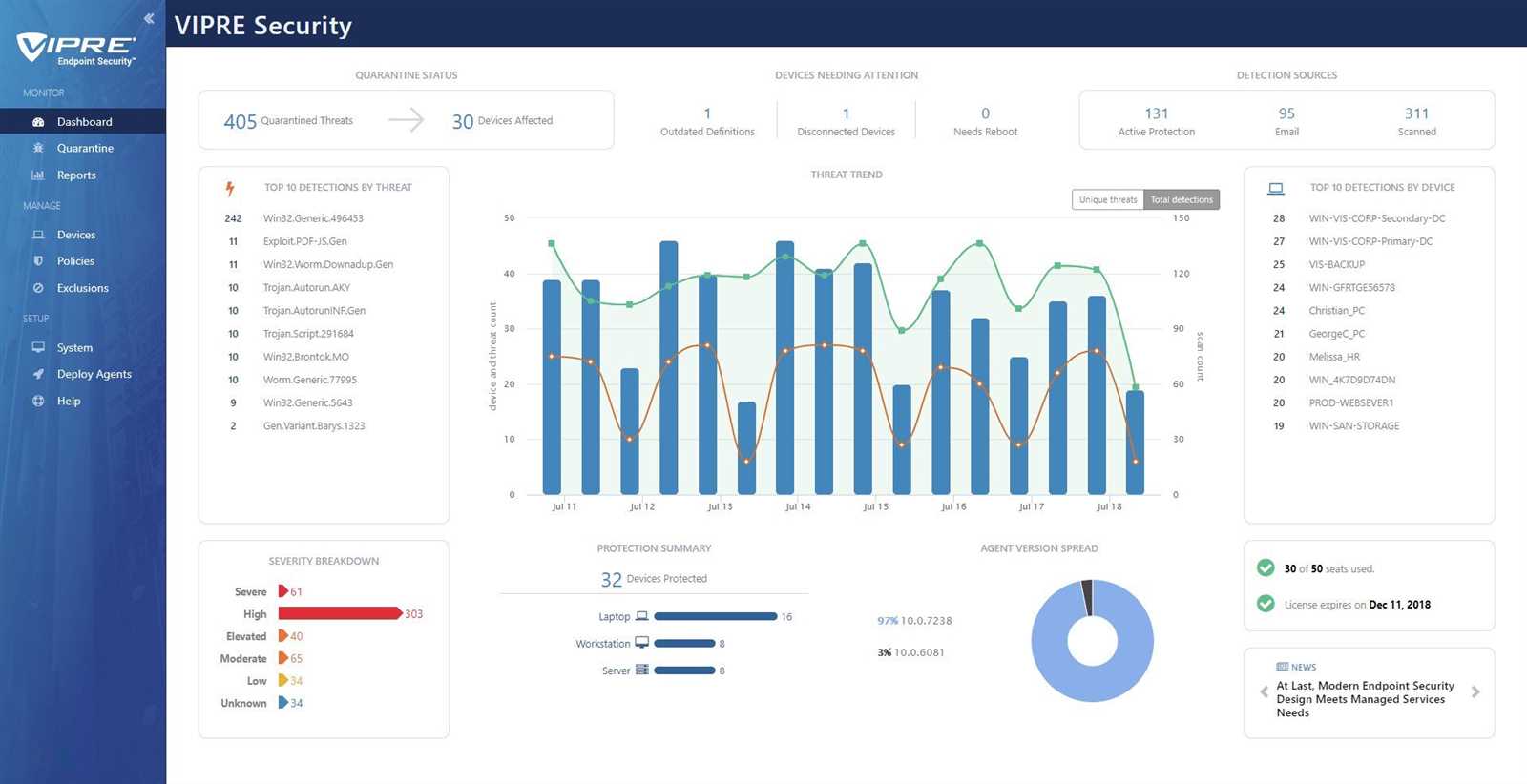
When it comes to ensuring the protection and integrity of your digital assets, having a comprehensive and reliable security solution is essential. Cloud One Endpoint Security offers a range of benefits that help safeguard your endpoints and ensure seamless business operations.
Enhanced Threat Detection
One of the key advantages of Cloud One Endpoint Security is its advanced threat detection capabilities. By utilizing cutting-edge technology and sophisticated algorithms, this solution can identify and mitigate a wide range of security threats. From malware and ransomware to phishing and zero-day exploits, Cloud One Endpoint Security keeps your endpoints secure from both known and emerging threats.
Real-Time Monitoring and Response
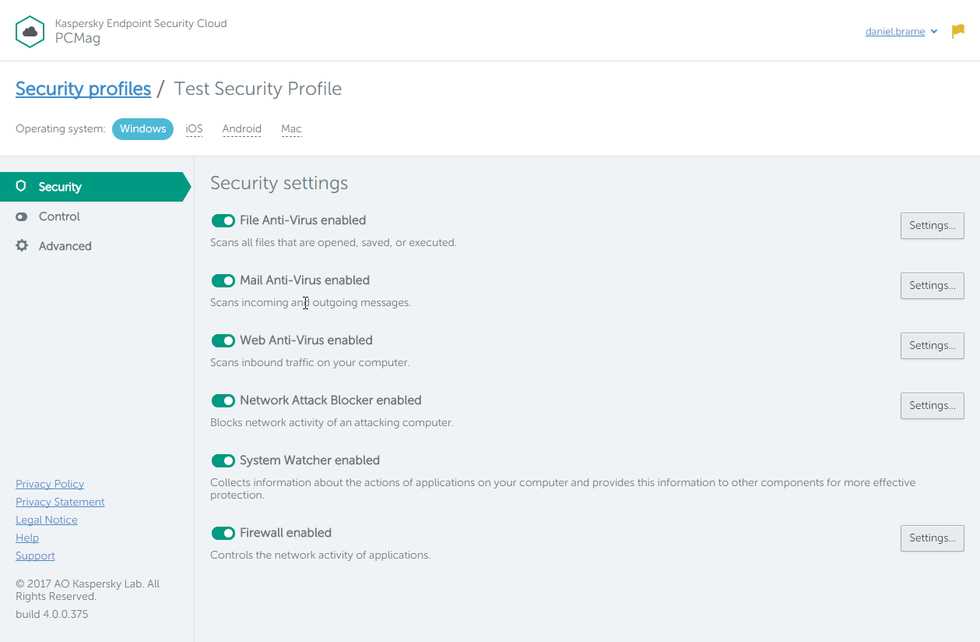
Cloud One Endpoint Security provides real-time monitoring and response, allowing you to stay proactive in the face of potential security incidents. This solution constantly analyzes endpoint activity, detecting any suspicious behavior or signs of compromise. With instant alerts and automated response capabilities, you can swiftly respond to security incidents and minimize the impact on your systems and data.
Furthermore, Cloud One Endpoint Security enables centralized management and streamlines security operations. With a single console, you can easily monitor and configure security policies across all endpoints in your network, ensuring consistent protection and minimizing administrative overhead.
In conclusion, the benefits of Cloud One Endpoint Security encompass enhanced threat detection, real-time monitoring, and response capabilities, as well as centralized management. By leveraging these features, businesses can effectively safeguard their endpoints and maintain a secure digital environment.
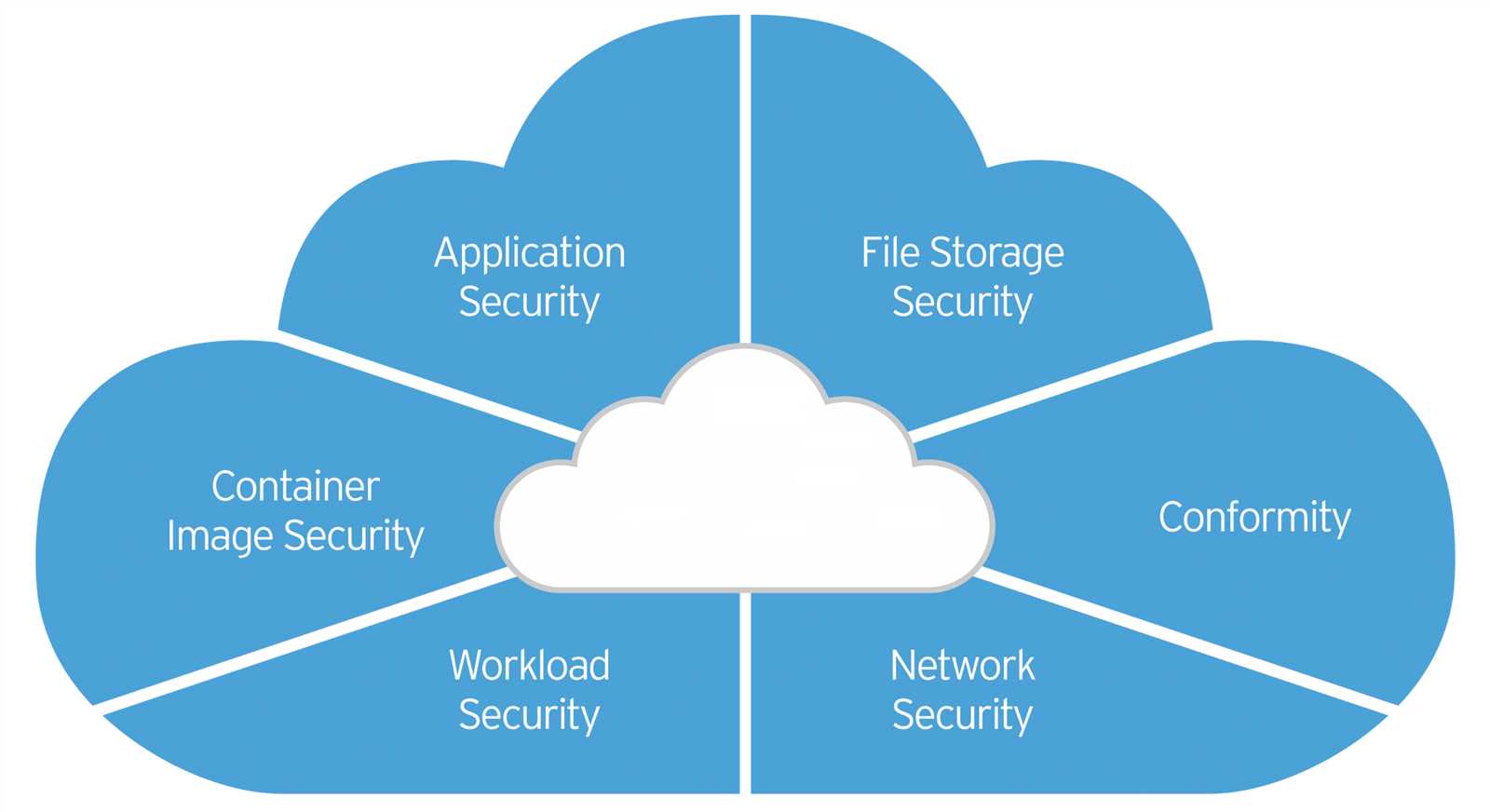
Features of Cloud One Endpoint Security
In this section, we will explore the various capabilities and functionalities offered by the Cloud One Endpoint Security solution. This comprehensive suite of features equips organizations with robust protection against threats and ensures the security of their endpoint devices.
- Advanced Threat Detection: The Cloud One Endpoint Security solution employs cutting-edge algorithms and machine learning techniques to detect and neutralize advanced threats. This includes identifying and blocking malware, ransomware, and other malicious software.
- Real-time Monitoring: With real-time monitoring capabilities, organizations can gain visibility into the security posture of their endpoint devices. This includes monitoring for suspicious activities, unauthorized access attempts, and potential data breaches.
- Centralized Management: The solution offers a centralized management console that allows administrators to efficiently manage and configure security policies for all endpoint devices. This simplifies the deployment and administration of security measures across the organization.
- Web and Email Protection: Cloud One Endpoint Security provides web and email protection features, safeguarding users from phishing attacks, malicious websites, and suspicious email attachments. It also includes content filtering capabilities to enforce web usage policies.
- Device Control: Organizations can implement granular device control policies to manage the use of external devices such as USB drives and external hard disks. This helps prevent unauthorized data transfers and protects against potential data leaks.
- Behavioral Analysis: The solution utilizes behavioral analysis techniques to identify anomalous behavior patterns and detect potential threats. This enables proactive threat hunting and ensures rapid response to emerging security incidents.
- Patch Management: Cloud One Endpoint Security offers automated patch management capabilities, ensuring that endpoint devices are up to date with the latest security patches and software updates. This minimizes vulnerabilities and strengthens overall security.
- Reporting and Analytics: The solution provides comprehensive reporting and analytics functionalities, offering insights into security events, threat trends, and overall system health. This facilitates informed decision-making and enhances incident response capabilities.
With these powerful features, Cloud One Endpoint Security empowers organizations to defend their endpoint devices against evolving cyber threats, mitigate risks, and maintain a secure computing environment.