
Discover the transformative power of modern security solutions as we delve into the groundbreaking capabilities of our cutting-edge technology. In this article, we explore the inner workings of a revolutionary software that enhances your organizational security through a state-of-the-art data protection system.
Delving into the realm of next-generation cybersecurity, we present an in-depth analysis of an innovative product that revolutionizes the way companies safeguard their digital assets. Unleashing the full potential of advanced encryption techniques and intelligent access controls, this information security solution ensures the highest levels of protection for your valuable data.
With a strong focus on empowering businesses with impenetrable defense mechanisms, this comprehensive overview provides a glimpse into the dynamic world of modern security landscapes. By combining unparalleled data protection protocols with intuitive user interfaces, this cutting-edge software streamlines the access management process, ensuring only authorized individuals have permission to enter designated areas of your digital infrastructure.
Embark on a journey that uncovers the intricacies of an all-encompassing security solution, offering seamless integration into your existing infrastructure while mitigating the risk of unauthorized access. Discover how this state-of-the-art system not only safeguards sensitive information but also enhances operational efficiency, enabling your organization to thrive in an increasingly complex digital arena.
Beyondtrust Password Management Overview
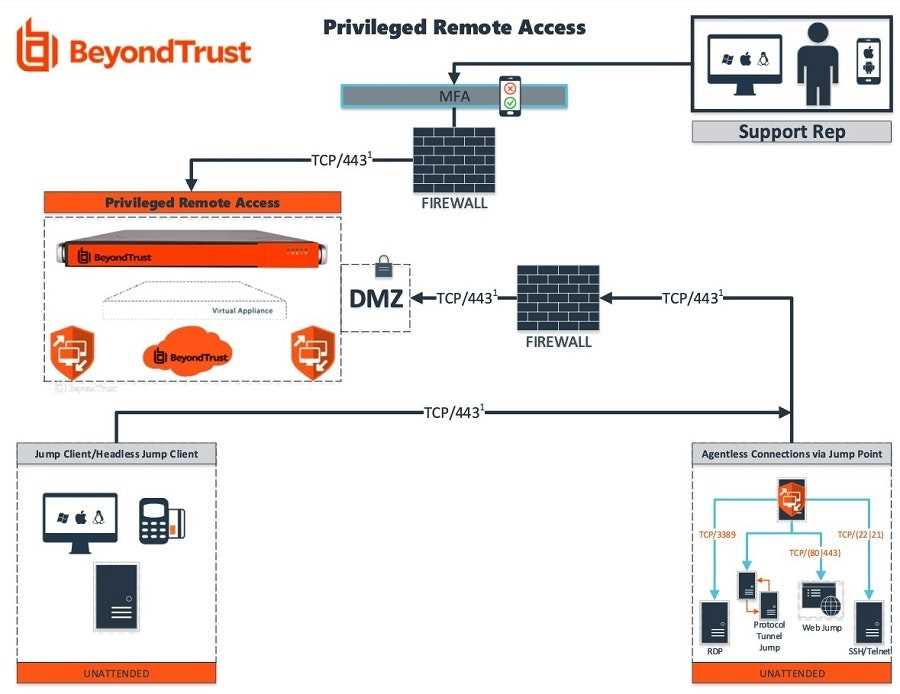
In this section, we will provide an overview of the comprehensive password management solutions offered by Beyondtrust. By utilizing advanced technology and innovative techniques, our password management platform enhances security and simplifies access control processes. Discover how our solution enables organizations to efficiently manage sensitive credentials while strengthening their defense against unauthorized access.
The Power of Secure Credential Management
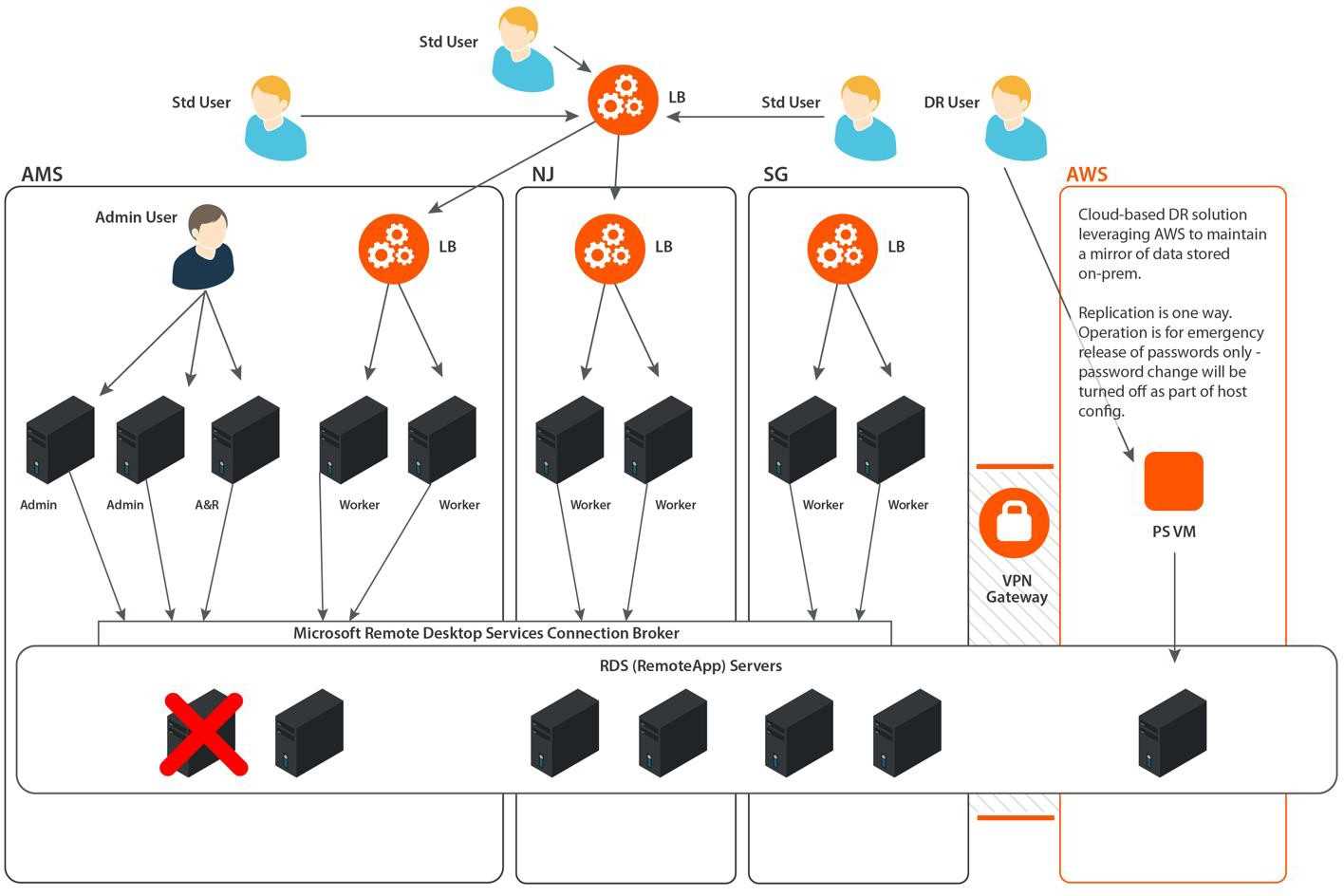
Effective credential management is a critical aspect of modern cybersecurity practices. It entails the secure storage, retrieval, and monitoring of credentials, allowing users to access various systems, applications, and resources with ease. Our password management solution enables organizations to minimize the risks associated with weak or stolen passwords, eliminating the human element from traditional password management approaches. Regain control over access privileges, track user activity, and enhance overall security posture with our robust and scalable credential management solution.
The Benefits of Centralized Access Control
Organizations often struggle with the daunting task of managing multiple user accounts and granting appropriate access privileges across various systems. Beyondtrust’s password management solution offers a centralized platform that streamlines access control processes, reducing administrative overhead and simplifying user provisioning. By providing a single point of control, our solution ensures consistent access policies are enforced across your entire environment, promoting accountability and reducing the risk of unauthorized access. Discover the benefits of centralized access control and enhance your organization’s security posture today.
Experience the power of cutting-edge technology and robust security measures with Beyondtrust’s password management solution. Empower your organization with streamlined credential management and centralized access control capabilities, mitigating the risks associated with weak passwords and unauthorized access. Elevate your security practices to new heights, ensuring the confidentiality, integrity, and availability of critical systems and data.
Secure and Convenient Password Management

In today’s digital landscape, the importance of secure and convenient password management cannot be overstated. As we navigate through countless online platforms, websites, and applications, it becomes increasingly challenging to remember and protect a multitude of passwords. Fortunately, advancements in password management technology offer a solution to this dilemma.
Ensuring the security of our passwords is paramount in safeguarding our sensitive information from unauthorized access. Robust password management systems employ various encryption techniques, multi-factor authentication, and advanced security protocols to protect sensitive data effectively. By securely storing passwords using industry-standard encryption algorithms, such systems guarantee the confidentiality and integrity of our credentials.
Additionally, convenient password management allows us to effortlessly handle the multitude of passwords we encounter daily. With features like auto-fill, password generators, and synchronization across multiple devices, password managers streamline the process of securely accessing various accounts and websites. By reducing the need for manual password input and eliminating the risk of weak or reused passwords, these tools save time, enhance productivity, and exemplify good security practices.
The convenience of password management extends beyond individual users to organizations. Enterprise-level password management solutions offer centralized control and administration, empowering businesses to enforce strong password policies, access controls, and transparent auditing. Moreover, integration with existing infrastructure and directories enables seamless implementation and enterprise-wide password security management.
As we continue to operate in a digital age where user credentials represent keys to our virtual identities, secure and convenient password management is essential. By adopting reliable password management systems, individuals and organizations can fortify their online security, mitigate risks of data breaches, and enjoy the ease of accessing their accounts without compromising password integrity.
Streamlined Access Control and Privileged Account Protection
Enhancing security measures and ensuring efficient access control are critical components for protecting sensitive data and minimizing the risk of unauthorized access or breaches. This section focuses on the importance of implementing streamlined access control and privileged account protection to safeguard valuable assets and maintain business continuity.
Efficiently managing user access rights and privileges is essential to mitigate security risks and prevent unauthorized individuals from accessing confidential information. Streamlined access control provides a comprehensive framework for organizations to establish customized access policies, enforce privileged user authentication, and monitor user activities. By effectively managing user permissions, organizations can minimize the potential vulnerability of privileged accounts, reducing the risk of data breaches and unauthorized system access.
Privileged account protection plays a crucial role in safeguarding critical systems and sensitive information. Privileged accounts, which possess extensive access privileges and control over various aspects of an organization’s infrastructure, present attractive targets for malicious actors seeking to exploit vulnerabilities. Implementing robust privileged account protection measures, such as strong authentication mechanisms, regular password rotations, and session monitoring, is essential to prevent unauthorized access, as well as identify and neutralize any potential security threats proactively.
Furthermore, organizations can benefit from implementing additional security measures like multi-factor authentication, which adds an extra layer of protection to the authentication process. By requiring users to provide multiple forms of verification, such as something they know (a password), something they have (a security token), or something they are (biometric data), organizations can significantly increase the security level and prevent unauthorized access attempts.
In conclusion, streamlined access control combined with privileged account protection is crucial for maintaining data security and preventing unauthorized access. By implementing customized access policies, strong authentication mechanisms, and additional security measures, organizations can effectively reduce the risk of data breaches and safeguard their valuable assets.
Enhanced Compliance and Auditing Capabilities
In this section, we will explore the advanced features of the product that ensure organizations can meet regulatory compliance requirements and maintain a high level of security. We will discuss the robust auditing capabilities and the comprehensive compliance tools that go beyond industry standards.
Auditing for Increased Accountability
The enhanced auditing capabilities of the solution provide organizations with increased accountability and transparency. By capturing detailed activity logs and user interactions, it enables organizations to track and monitor all privileged access activities effectively. These logs can be easily accessed and reviewed, offering valuable insights into user behavior and potential security risks.
Comprehensive Compliance Tools
The product’s comprehensive compliance tools offer organizations a holistic approach to meeting industry regulations. With built-in compliance frameworks and templates, organizations can quickly configure and deploy compliance policies based on specific regulatory requirements. These tools simplify the compliance process by automating tasks such as user access management, password rotation, and privilege elevation, reducing the risk of security breaches due to human error.
Moreover, the solution ensures compliance by providing real-time alerts and notifications when policy violations occur, allowing administrators to take immediate action. It also generates detailed compliance reports, which can be shared with auditors or regulatory bodies to demonstrate adherence to industry standards.
By leveraging these enhanced compliance and auditing capabilities, organizations can strengthen their security posture, mitigate risks, and achieve regulatory compliance effortlessly. The solution’s comprehensive tools and advanced features empower organizations to navigate the complex landscape of regulatory requirements with confidence and ease.