
Embark on a journey into the intricate realm of integrated circuits, where minuscule components hold vast stores of invaluable information.
Delve into the enigmatic realm of semiconductor storage, where the tiniest alterations can yield monumental consequences.
Explore the labyrinthine pathways etched onto silicon wafers, weaving a tapestry of binary brilliance.
Uncover the blueprints of digital memory architecture, deciphering the cryptic language of electrons and gates.
Join us as we decipher the inner workings of a quintessential cornerstone of electronic memory technology.
Understanding the Basics of 28C16 EEPROM
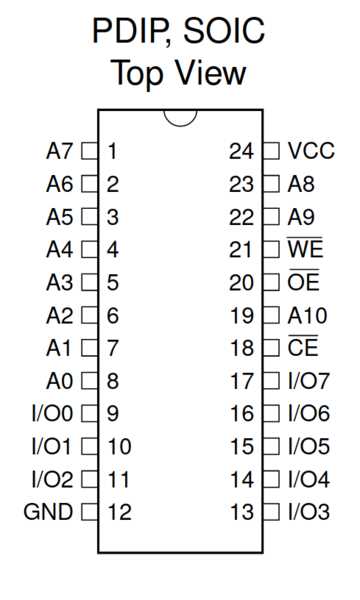
In the realm of digital memory, there exists a fascinating component known for its versatility and reliability. This section delves into the fundamental principles underlying the operation and functionality of a particular type of electrically erasable programmable read-only memory (EEPROM). Exploring its core concepts sheds light on its significance in various electronic systems, offering insights into its inner workings and practical applications.
The Essence of Non-Volatile Memory

At the heart of the 28C16 EEPROM lies the essence of non-volatile memory, a cornerstone in modern computing and electronics. Unlike volatile memory, which requires a continuous power supply to retain data, non-volatile memory preserves information even in the absence of power. This characteristic enables persistent storage of critical data, making it indispensable in scenarios where data integrity and durability are paramount.
Unlocking the Mechanics of Data Storage and Retrieval
Delving deeper, the mechanics of data storage and retrieval within the 28C16 EEPROM unveil a sophisticated interplay of electrical signals and physical structures. Understanding how bits of data are stored, erased, and read back provides crucial insights into the intricacies of memory management and manipulation. By unraveling these mechanics, engineers and enthusiasts alike gain a deeper appreciation for the complexities underlying seemingly simple memory devices.
Exploring Memory Organization and Addressing
In this section, we delve into the intricate structure and addressing mechanisms of memory modules, shedding light on how data is stored, accessed, and managed within these electronic components. Understanding the fundamental principles of memory organization and addressing is paramount for comprehending the functionality and utilization of these crucial elements in electronic systems.
Memory Architecture Overview

Before delving into the specifics of memory organization and addressing, it is imperative to grasp the broader architectural framework within which these processes occur. Memory architecture encompasses the hierarchical arrangement of storage elements, ranging from individual bits to complex data structures. This hierarchical structure forms the foundation upon which memory organization and addressing principles are built.
Addressing Mechanisms and Data Retrieval
Addressing mechanisms dictate how data is accessed and retrieved from memory modules. By employing various addressing techniques, electronic systems can efficiently locate and retrieve data stored within memory cells. Understanding these mechanisms is essential for optimizing memory access times and ensuring efficient utilization of available memory resources.
Examining Programming and Erasing Procedures
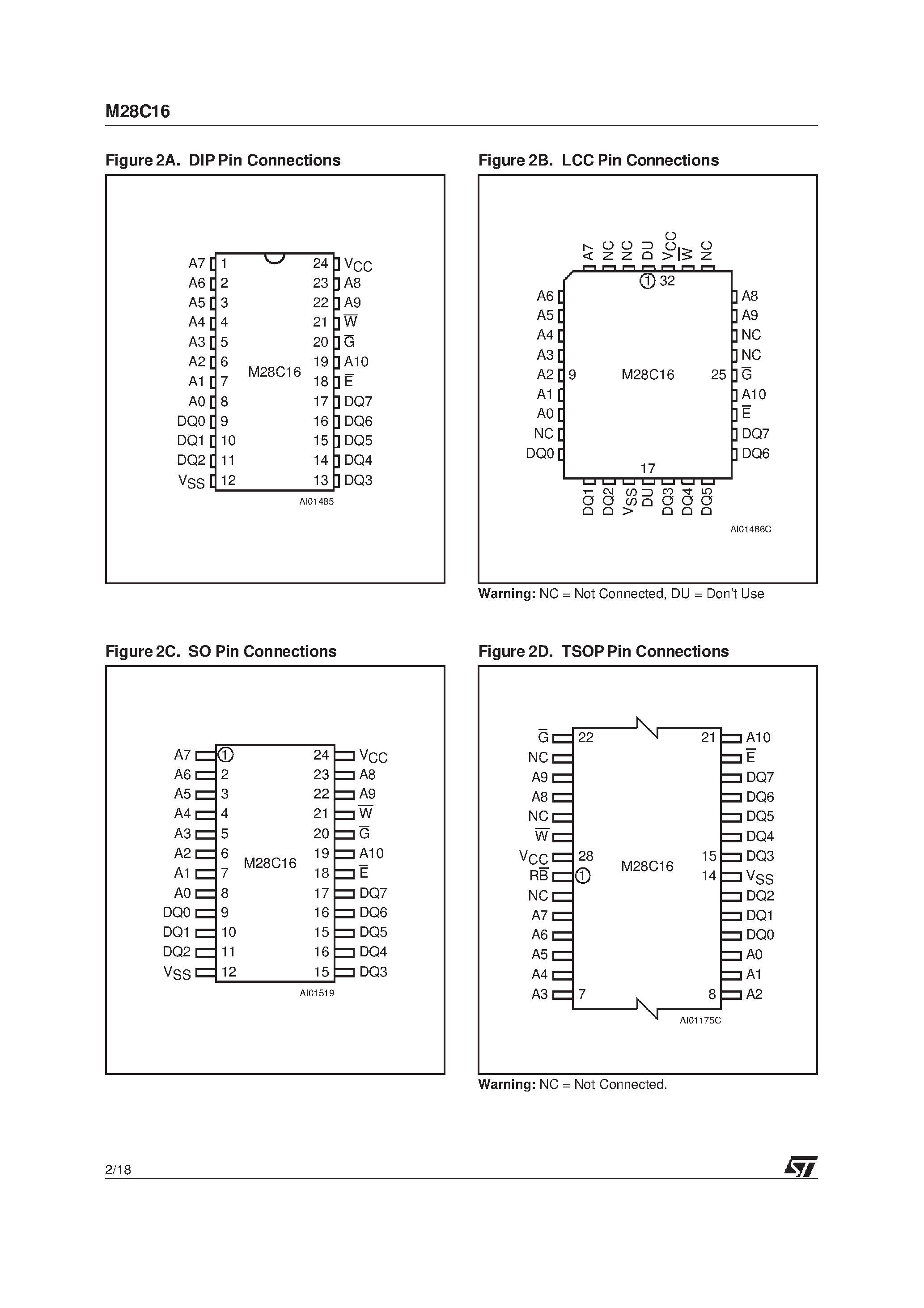
In this section, we delve into the intricate processes involved in altering and resetting the memory content of certain electronic devices. Understanding the methodologies behind these actions is crucial for maintaining the integrity and functionality of the stored data without compromising the device’s performance. Here, we explore the systematic steps required to initiate changes in the stored information and to erase existing data, ensuring a seamless transition between states while upholding the device’s operational efficiency.
| Procedure | Description |
|---|---|
| Programming | During this phase, data modification occurs, wherein new information is meticulously written into the memory cells of the electronic component. This process involves a series of controlled operations to ensure accuracy and reliability, preserving the integrity of the stored content. |
| Erasing | Contrary to programming, erasing involves the removal or resetting of existing data within the memory module. This procedure is executed with precision to clear designated memory sectors, allowing for the subsequent rewriting of fresh data without residual traces of previous information, thus maintaining the device’s efficiency. |
By scrutinizing the intricacies of programming and erasing procedures, one gains insight into the underlying mechanisms governing the manipulation of electronic memory. This comprehension facilitates informed decision-making regarding data management strategies, ensuring optimal performance and longevity of electronic systems.
Utilizing Features for Embedded Systems
Embedded systems thrive on the integration of specialized functionalities to optimize performance and efficiency in diverse applications. This section delves into harnessing the capabilities inherent in integrated circuits to enhance the functionality and versatility of embedded systems.
Maximizing Embedded Capabilities

Embedded systems are adept at leveraging the myriad features embedded within integrated circuits to fulfill specific operational requirements. By intelligently utilizing the inherent functionalities of microcontrollers and peripherals, developers can tailor solutions that are finely tuned to the demands of targeted applications. Through meticulous optimization and strategic configuration, the full potential of embedded systems can be unlocked, leading to enhanced performance, reduced power consumption, and streamlined operations.
Feature Integration Strategies
Efficient utilization of integrated features necessitates a comprehensive understanding of both hardware and software aspects. Developers must employ a systematic approach to identify, assess, and incorporate relevant functionalities into the embedded system design. This involves meticulous analysis of datasheets, exploration of available resources, and strategic planning to seamlessly integrate desired features while mitigating potential conflicts or limitations. By adopting a holistic perspective and employing agile methodologies, developers can effectively harness the capabilities of embedded systems to meet the evolving needs of modern applications.
| Key Strategies | Benefits |
|---|---|
| Feature prioritization | Optimized resource allocation |
| Configurable peripherals | Enhanced versatility |
| Dynamic power management | Reduced energy consumption |