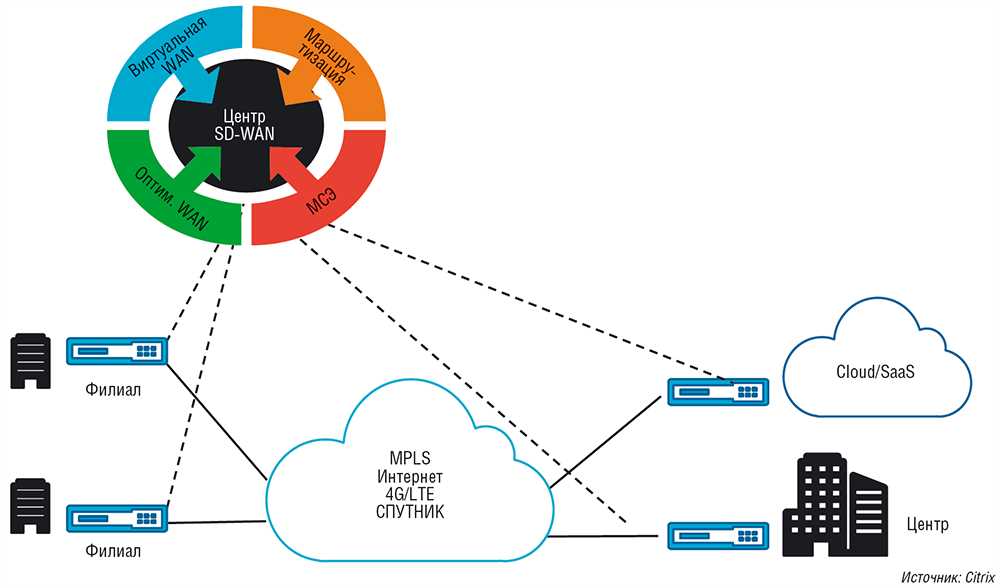
Revolutionizing modern network architecture, the technology landscape brims with innovative solutions, each promising to redefine the realms of connectivity. Amidst this dynamic evolution, a remarkable contender emerges, poised to transcend conventional boundaries and usher in a new era of network empowerment. Delve into the intricate fabric of advanced networking with a comprehensive exploration of a groundbreaking document, offering insights into a formidable entity that promises to reshape connectivity paradigms.
Embark on a journey through the labyrinth of technological prowess, as this document unveils the intricacies of a transformative force, destined to propel organizations towards unprecedented efficiency and resilience. Cast aside conventional notions as we delve into the multifaceted capabilities of a solution set to redefine the very essence of connectivity.
Prepare to be enthralled by a tapestry woven with innovation, as we decipher the nuances of a game-changing entity poised to revolutionize network dynamics. Through meticulous analysis and insightful revelations, witness the emergence of a solution that promises not just connectivity, but a gateway to unparalleled agility and performance.
Unlocking the Potential: Exploring the Features of Cutting-Edge Network Innovation
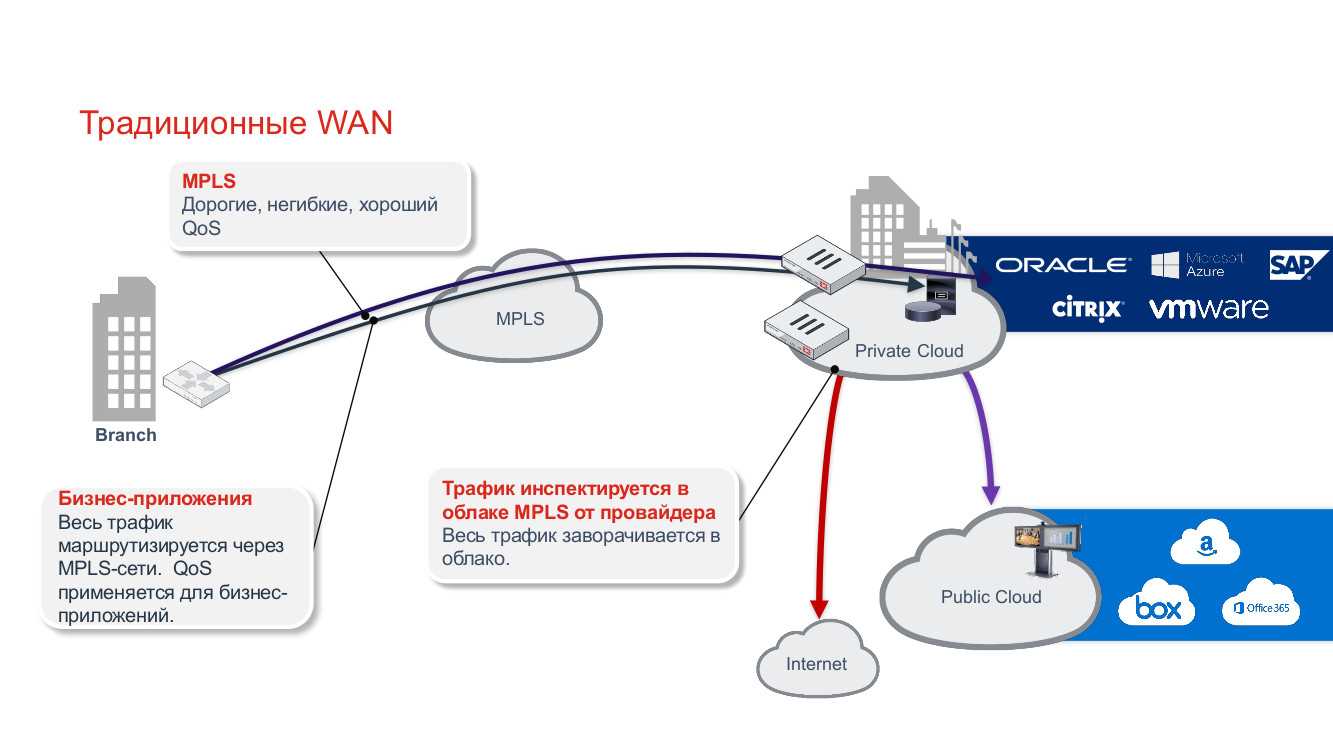
In this segment, we delve into the myriad capabilities of the latest breakthrough in network technology, delving into its diverse functionalities and dynamic attributes. Discover how this advanced solution revolutionizes connectivity, elevating network performance to unparalleled levels of efficiency and reliability.
| Enhanced Connectivity: | Experience seamless and robust connections, ensuring uninterrupted access to critical resources across diverse network environments. |
| Optimized Performance: | Maximize operational efficiency with intelligent traffic management, prioritizing mission-critical applications for optimal performance. |
| Dynamic Traffic Steering: | Empower your network with adaptive routing capabilities, dynamically adjusting traffic pathways to mitigate congestion and latency. |
| Advanced Security: | Elevate your defenses with robust encryption protocols and comprehensive threat mitigation measures, safeguarding sensitive data against evolving cyber threats. |
| Centralized Management: | Streamline network administration through centralized control and orchestration, simplifying configuration and monitoring processes for enhanced operational agility. |
Understanding the Core Architecture and Performance Metrics
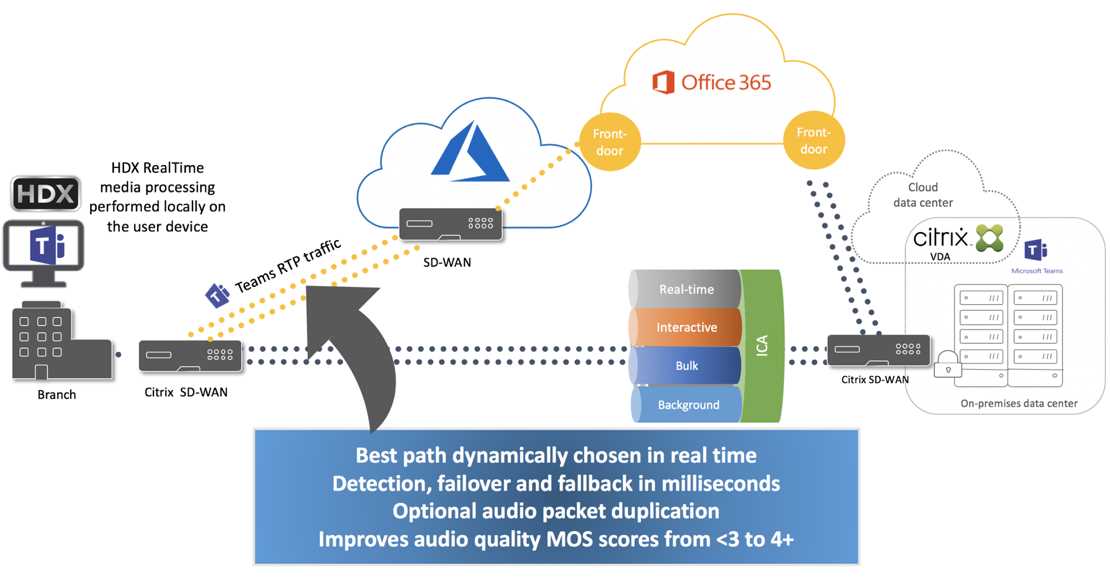
In this section, we delve into the fundamental framework and key performance indicators of the SD-WAN 2100, shedding light on its underlying structure and the metrics that gauge its efficacy.
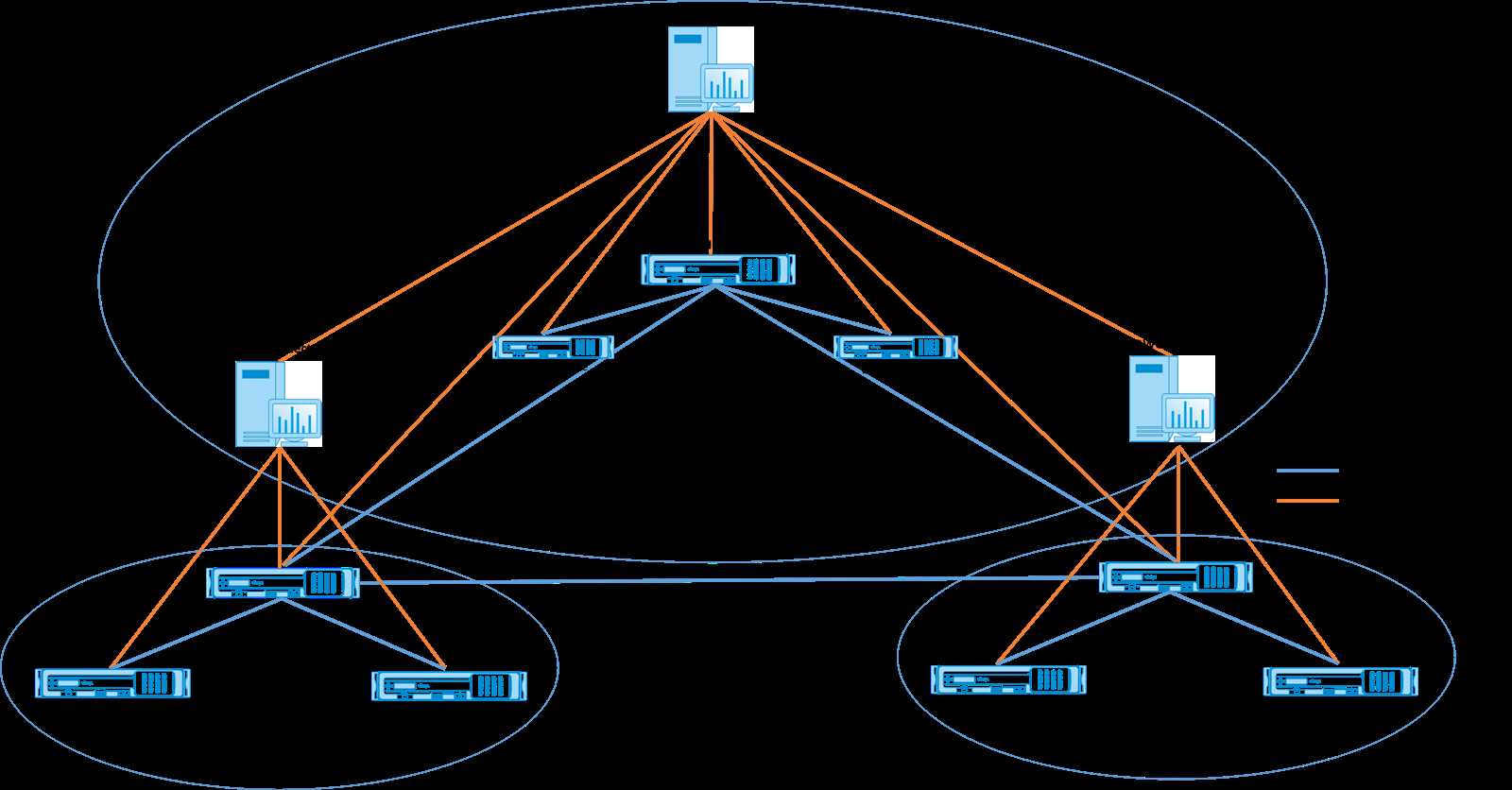
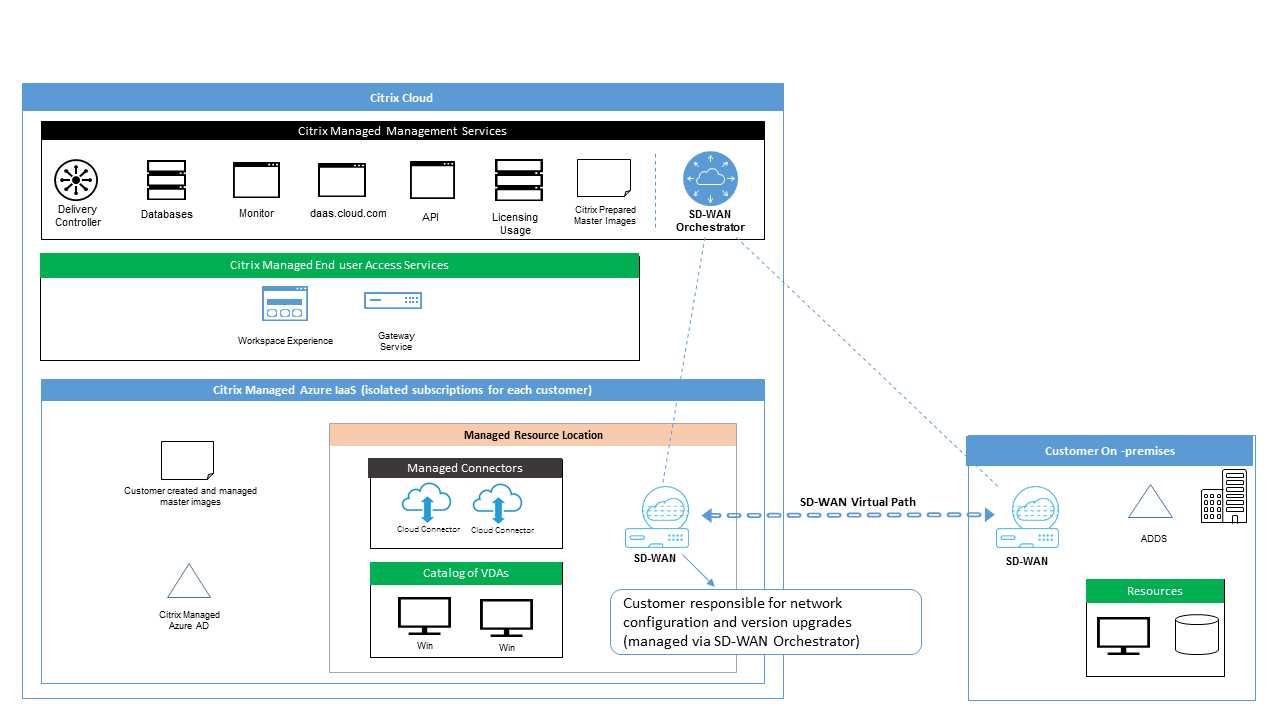
- Architectural Overview: Explore the foundational design elements that constitute the SD-WAN 2100, discerning its core components and their interplay.
- Performance Evaluation: Delve into the various metrics employed to assess the efficiency and functionality of the SD-WAN 2100, including throughput, latency, and packet loss.
- Scalability and Flexibility: Examine the adaptability and scalability of the architecture, considering its ability to accommodate diverse network environments and evolving demands.
- Resilience and Redundancy: Assess the resilience mechanisms integrated into the architecture to ensure seamless operation and mitigate potential disruptions.
- Quality of Service (QoS): Investigate the mechanisms employed to prioritize and optimize network traffic, enhancing user experience and application performance.
This exploration aims to provide a comprehensive understanding of the structural underpinnings and performance benchmarks of the SD-WAN 2100, illuminating its role in modern networking landscapes.
Enhancing Security Measures: Integrating Advanced Threat Protection
In the realm of digital defense fortification, bolstering security measures represents a paramount endeavor. Amidst the ever-evolving landscape of cyber threats, the integration of advanced threat protection stands as a pivotal strategy. This section delves into the imperative task of fortifying digital perimeters against a myriad of sophisticated hazards, leveraging cutting-edge mechanisms to safeguard sensitive assets and ensure operational integrity.
1. Holistic Defense Mechanisms: Embracing a comprehensive approach to security entails weaving together a tapestry of defenses. From proactive threat detection to responsive mitigation strategies, a multifaceted arsenal is indispensable. Advanced threat protection embodies this holistic ethos, encompassing not only conventional safeguards but also proactive measures designed to preempt emerging threats before they materialize.
2. Dynamic Threat Landscape: The contemporary threat landscape is characterized by its dynamism and complexity, where adversaries constantly innovate to circumvent traditional security protocols. Advanced threat protection confronts this reality head-on, employing adaptive algorithms and behavioral analysis to identify anomalous patterns indicative of malicious intent. By remaining vigilant and agile, organizations can effectively mitigate risks posed by both known and unknown threats.
3. Intelligent Response Mechanisms: In the face of escalating cyber threats, timely and intelligent response mechanisms are indispensable. Advanced threat protection leverages machine learning algorithms and artificial intelligence to autonomously discern genuine threats from benign anomalies, facilitating rapid response and containment. This proactive stance not only minimizes potential damage but also augments incident response capabilities, empowering organizations to swiftly neutralize emerging threats.
4. Collaborative Defense Ecosystems: Recognizing the collective nature of cyber defense, advanced threat protection fosters collaboration across disparate domains and stakeholders. Through information sharing and collaborative analysis, organizations can collectively fortify their defenses and amplify their resilience against sophisticated adversaries. By harnessing the collective intelligence of a global network, advanced threat protection enables organizations to stay one step ahead in an increasingly perilous digital landscape.
5. Continuous Evolution: The efficacy of advanced threat protection hinges upon its capacity for continuous evolution and adaptation. In an environment characterized by incessant innovation and mutation, static defenses are inherently inadequate. Advanced threat protection embraces a philosophy of perpetual evolution, wherein algorithms and methodologies are continuously refined and enhanced to counter emerging threats effectively. By remaining agile and responsive, organizations can fortify their defenses and safeguard their digital assets against evolving threats.
As organizations navigate the intricate labyrinth of cyber threats, the integration of advanced threat protection emerges as a linchpin of their defensive strategy. By embracing a holistic approach to security, leveraging cutting-edge technologies, and fostering collaborative ecosystems, organizations can fortify their defenses and navigate the digital terrain with confidence.
Optimizing User Experience: Harnessing Application Intelligence and Quality of Service Management
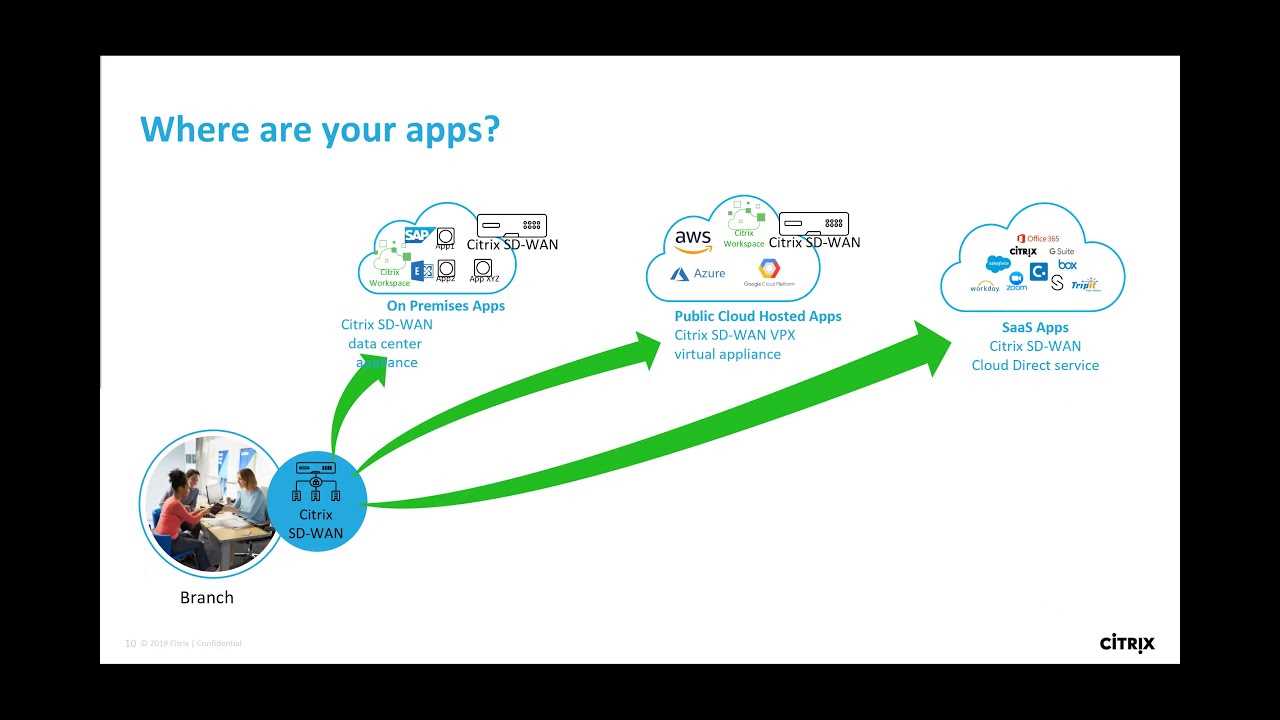
In the realm of network infrastructure enhancement, the focal point resides in refining the end-user journey through adept application understanding and meticulous management of Quality of Service (QoS) parameters. This segment delves into the pivotal strategies and methodologies for cultivating an environment where user experience is paramount, achieved through the utilization of application intelligence and judicious QoS controls.
The Power of Application Intelligence
At the heart of optimizing user experience lies the ability to comprehend and cater to the diverse array of applications traversing the network. Application intelligence empowers administrators to discern the unique characteristics of each application, including its bandwidth requirements, latency sensitivity, and traffic patterns. By wielding this insight, organizations can prioritize mission-critical applications, mitigate congestion, and allocate resources judiciously, thereby fostering a seamless and responsive user experience.
Mastering Quality of Service Controls
Quality of Service (QoS) controls serve as the bedrock for orchestrating network resources in alignment with business objectives and user expectations. Through the implementation of QoS policies, administrators can establish hierarchical traffic prioritization schemes, enforce bandwidth allocation thresholds, and enforce latency constraints. By sculpting the network landscape with precision, organizations can ensure that critical applications receive the requisite bandwidth and latency guarantees, while non-essential traffic is gracefully managed, safeguarding optimal performance for all users.
- Unveiling the intricacies of application behavior
- Strategically prioritizing mission-critical applications
- Allocating resources judiciously to mitigate congestion
- Establishing hierarchical traffic prioritization schemes
- Enforcing bandwidth allocation thresholds
- Implementing latency constraints for optimal performance