
Unveiling the technical blueprint of the latest addition to the Fortigate family unveils a powerhouse of features tailored to meet contemporary cybersecurity demands. Delving into the intricacies of this cutting-edge device, we dissect its formidable capabilities and robust architecture, shedding light on its prowess in safeguarding digital assets.
Embarking on a journey through the realm of network fortification, we navigate through the intricate landscape of security protocols and throughput benchmarks. Unveiling the essence of its design philosophy and performance metrics, we decipher the language of resilience and efficiency encoded within.
Diving deeper into the labyrinth of specifications, we unearth a treasure trove of functionalities meticulously crafted to fortify digital infrastructure against evolving threats. From dynamic threat intelligence to agile traffic management, each feature epitomizes the synergy between innovation and necessity.
Understanding the FortiGate 600F: An In-depth Exploration
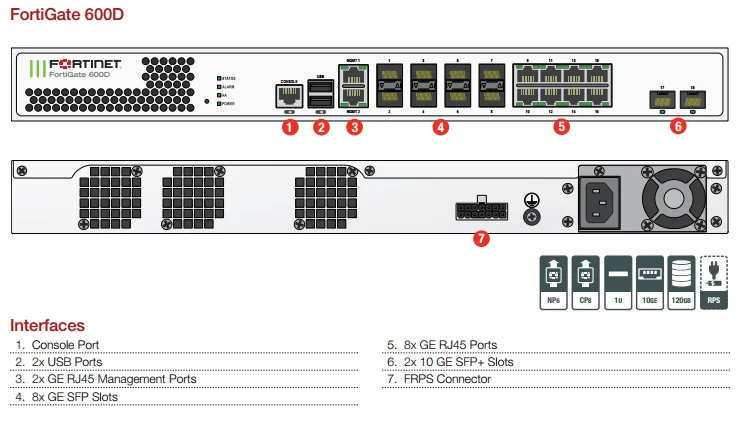
In this segment, we delve into a comprehensive examination of the intricate workings and functionalities of the robust FortiGate 600F. Embark on a journey through its myriad features, dissecting its capabilities, and uncovering the essence of its design.
Key Features and Performance Metrics

In this section, we delve into the distinctive attributes and operational benchmarks of the referenced security infrastructure, highlighting its core functionalities and efficiency indicators. By exploring the intrinsic capabilities and operational prowess, readers gain a comprehensive understanding of the product’s prowess and its efficacy in addressing contemporary security challenges.
Distinctive Attributes
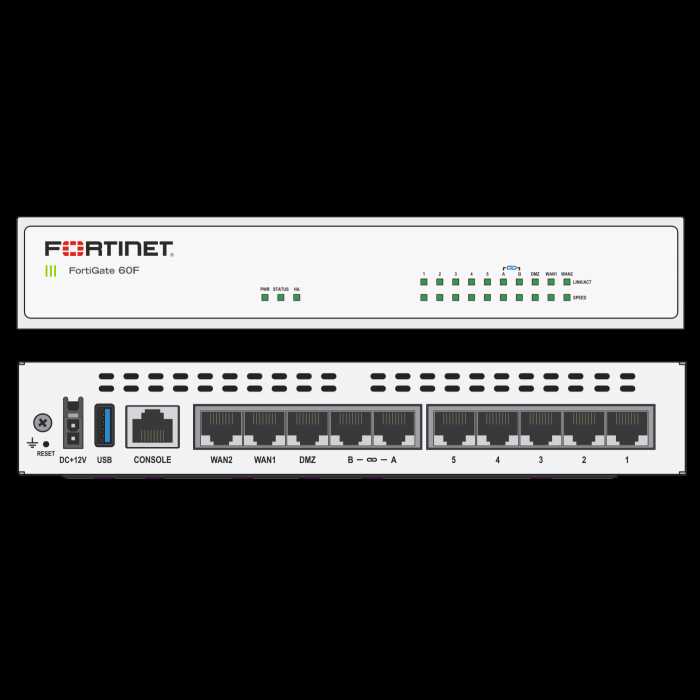
- Advanced Security Capabilities
- Robust Threat Detection Mechanisms
- Enhanced Network Performance Optimization
- Streamlined Traffic Management
- Scalability and Flexibility
Performance Metrics
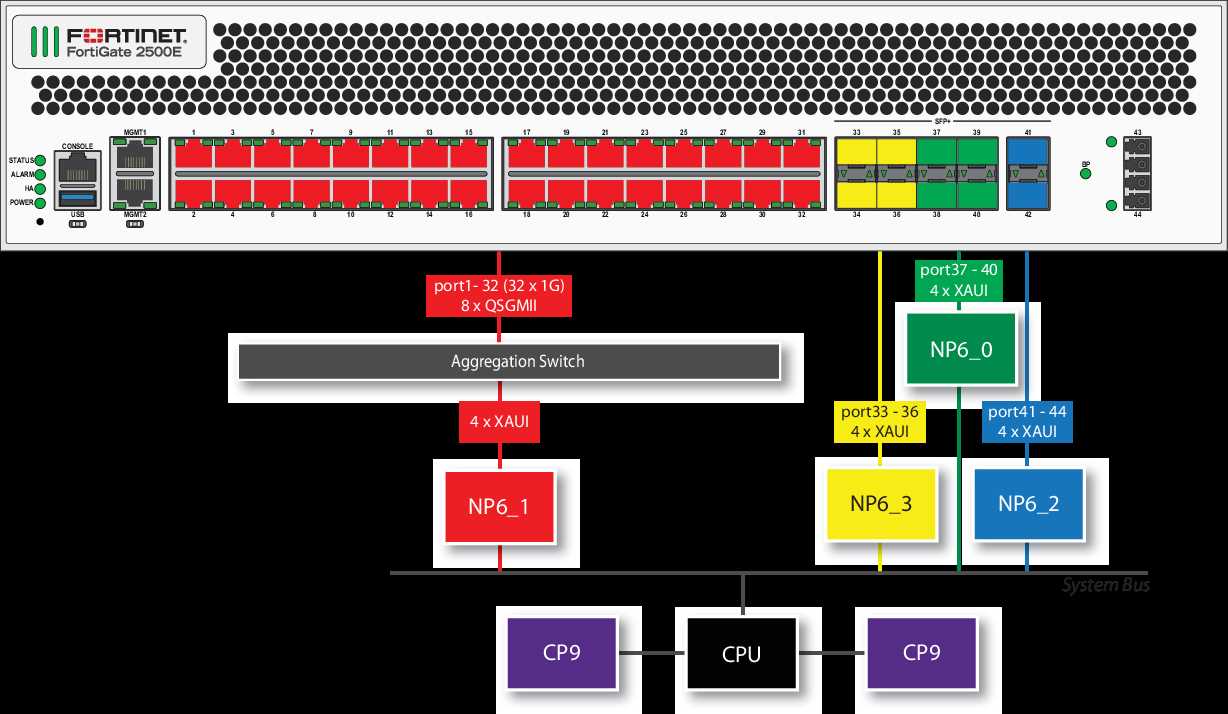
- Throughput Rates for Various Protocols
- Packet Inspection Speed
- Latency Metrics
- Resource Utilization Efficiency
- High Availability and Uptime Statistics
Deployment Scenarios and Utilization Instances
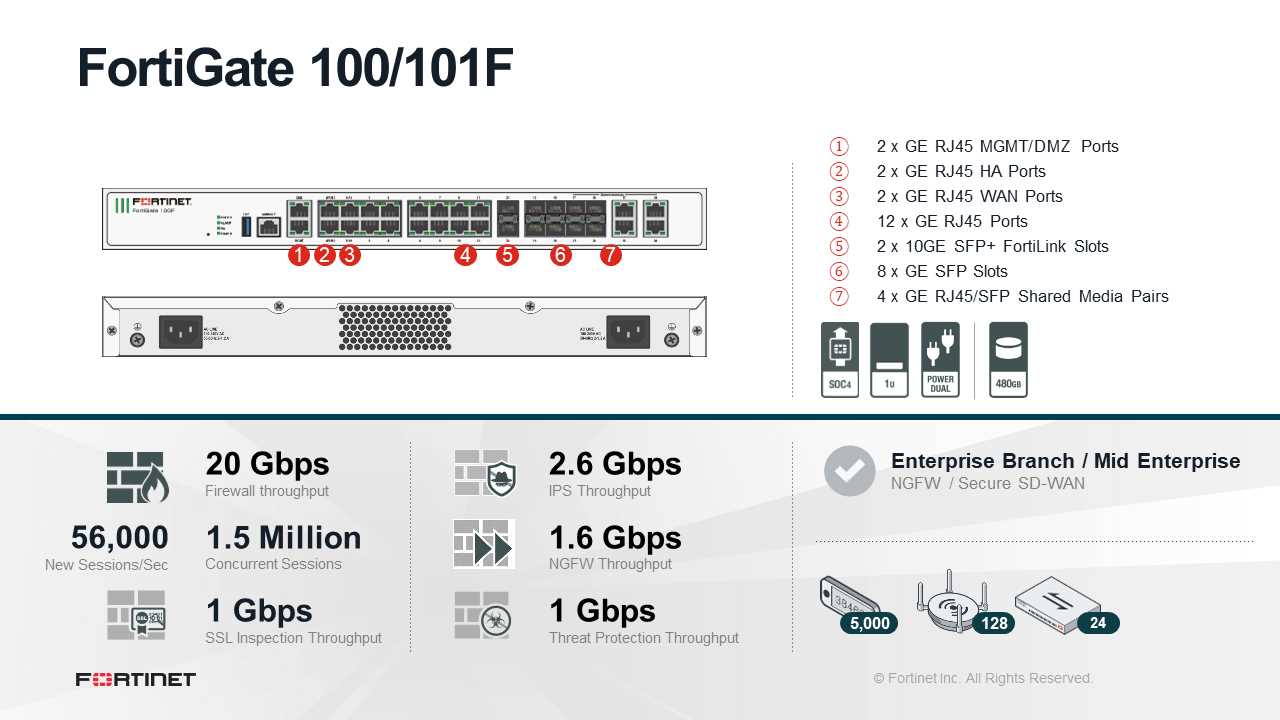
Within the landscape of network security appliances, diverse scenarios and practical applications emerge, showcasing the versatility and efficacy of robust solutions. This section delves into various contexts where such systems find integration and elucidates the manifold ways they address modern cybersecurity challenges.
| Scenario | Use Case |
|---|---|
| Enterprise Network Protection | Guarding expansive corporate networks against evolving threats, ensuring data integrity, and maintaining seamless operations. |
| Remote Access Security | Securing remote access points and enabling secure connections for telecommuters, remote branches, and mobile employees. |
| Cloud Integration | Facilitating secure connections and seamless integration with cloud platforms, ensuring data confidentiality and compliance. |
| Unified Threat Management | Converging multiple security functionalities into a single platform for streamlined management and comprehensive threat defense. |
| Industrial Control Systems | Protecting critical infrastructure, such as power plants and manufacturing facilities, from cyber threats to ensure operational continuity and safety. |
| IoT Security | Safeguarding Internet of Things (IoT) devices and networks from vulnerabilities, ensuring data privacy and preventing unauthorized access. |
These scenarios represent only a fraction of the diverse environments where advanced security solutions play a pivotal role. Each use case demands tailored configurations and vigilant monitoring to uphold the highest standards of protection and resilience.
Comparison with Competing Solutions
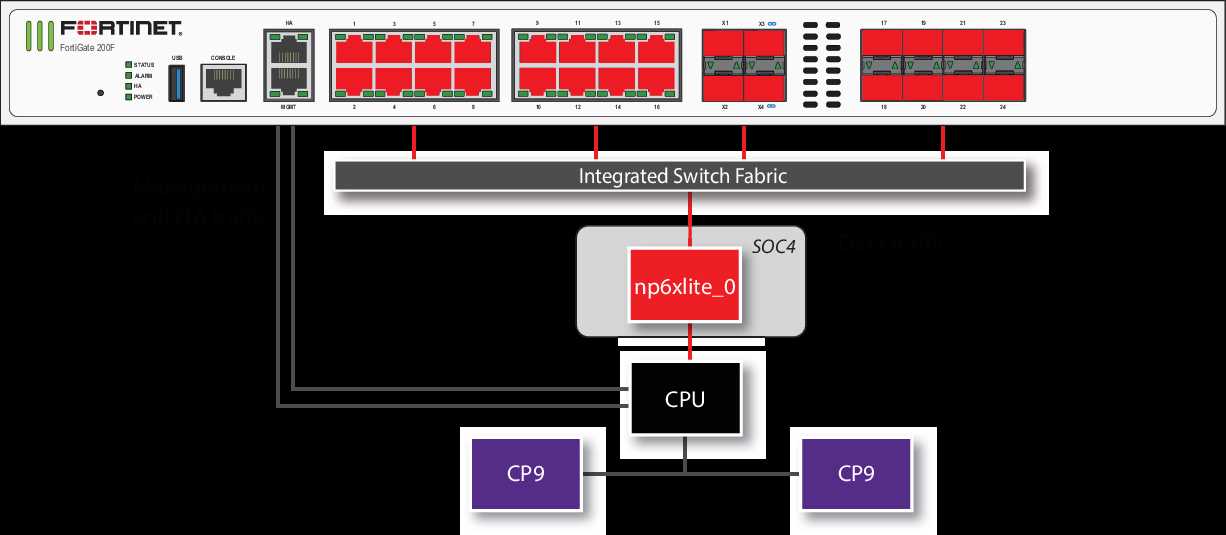
When exploring options within the realm of network security appliances akin to the 600f Fortigate, it becomes imperative to conduct a thorough comparison with analogous offerings available in the market. This section aims to delineate a comprehensive evaluation of alternative solutions without explicit reference to the aforementioned device. By scrutinizing various contenders in this arena, we can discern the nuanced distinctions in functionality, performance, and feature set.
First and foremost, examining the landscape of similar products unveils a spectrum of offerings tailored to meet diverse organizational needs. Each solution boasts unique attributes, ranging from scalability and robustness to versatility in deployment scenarios. Understanding the comparative strengths and weaknesses of these alternatives empowers decision-makers to make informed choices aligned with their specific requirements.
Moreover, juxtaposing competing solutions elucidates the technological prowess and innovation driving the evolution of network security infrastructure. From cutting-edge threat detection algorithms to intuitive user interfaces, each contender strives to carve a niche by offering compelling value propositions. Such a comparative analysis facilitates a holistic understanding of the evolving cybersecurity landscape.
Furthermore, considerations extend beyond mere technical specifications to encompass factors such as cost-effectiveness, vendor support, and ecosystem compatibility. Assessing these facets in conjunction with performance metrics allows stakeholders to gauge the holistic viability of each solution within their organizational framework.
In essence, this section endeavors to provide a comprehensive overview of competing solutions in the domain of network security appliances. By delving into the intricacies of functionality, performance, and ancillary factors, stakeholders can navigate the labyrinth of options with confidence, ensuring the optimal selection aligned with their strategic objectives.