
Enhancing the security of sensitive information within modern organizations has become paramount in the digital age. As businesses strive to safeguard their proprietary data from unauthorized access and breaches, the demand for robust confidentiality management solutions continues to escalate.
Discovering effective methods to protect confidential information throughout its lifecycle is imperative for maintaining trust among stakeholders and complying with regulatory standards. In this context, exploring comprehensive privacy protection frameworks emerges as a crucial endeavor for enterprises across diverse sectors.
Unveiling innovative approaches to ensure data privacy and integrity is essential for mitigating risks associated with data leakage and unauthorized disclosure. By adopting advanced security protocols and leveraging cutting-edge technologies, organizations can fortify their defenses against evolving cyber threats.
The Power of Data Loss Prevention: Ensuring Information Security

In today’s digital landscape, the preservation of sensitive information stands as a paramount concern for organizations across industries. Data loss can result in severe repercussions, including financial loss, reputational damage, and legal ramifications. Hence, robust measures must be in place to safeguard data from unauthorized access, leakage, or theft.
Comprehensive Protection

Effective data loss prevention (DLP) solutions serve as the frontline defense against data breaches and leakage. By implementing advanced algorithms and sophisticated monitoring mechanisms, DLP technologies analyze data traffic, identify sensitive information, and enforce policies to prevent unauthorized dissemination.
Proactive Risk Mitigation
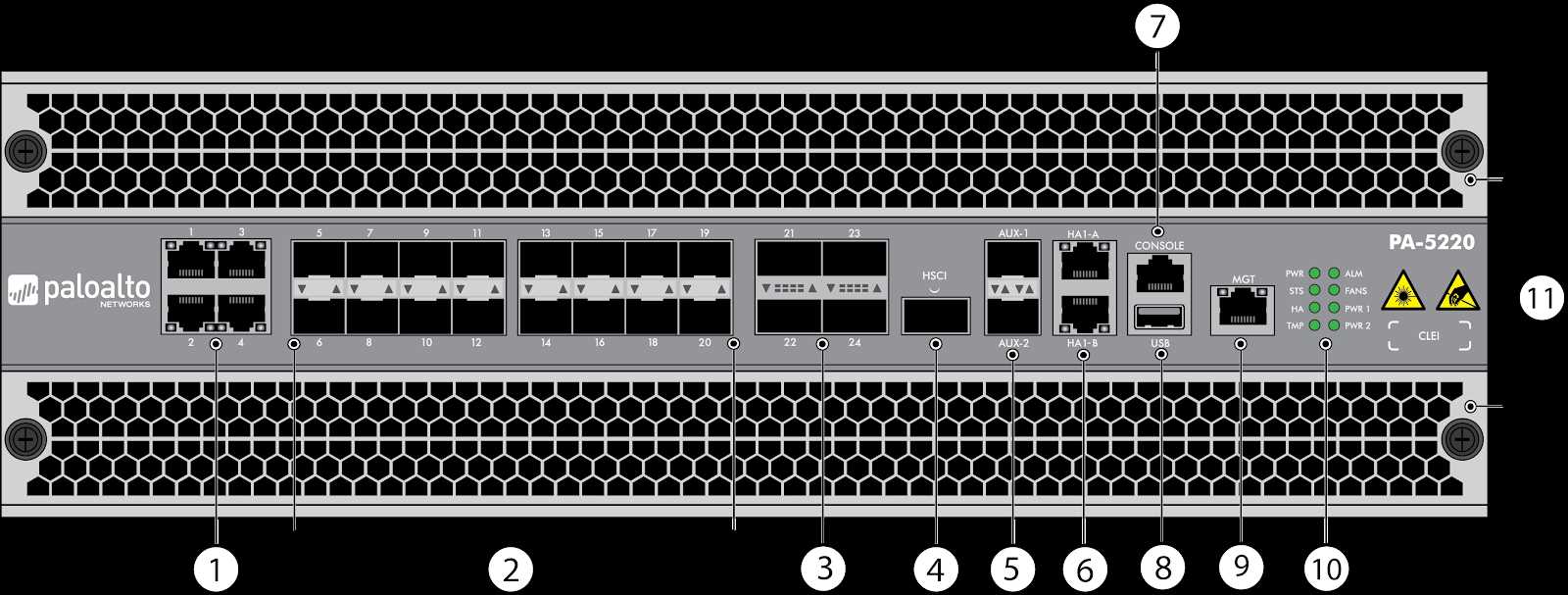
Moreover, Palo Alto’s DLP solution goes beyond reactive measures by proactively identifying potential vulnerabilities and enforcing preemptive actions. Through continuous monitoring and real-time alerts, organizations can swiftly respond to emerging threats, thereby minimizing the likelihood of data compromise.
- Real-time monitoring and analysis
- Policy enforcement and compliance management
- Integration with existing security infrastructure
- Customizable risk assessment and prioritization
By harnessing the power of Palo Alto’s DLP capabilities, organizations can fortify their data protection strategies, uphold regulatory compliance, and preserve trust among stakeholders.
Understanding Data Loss Prevention
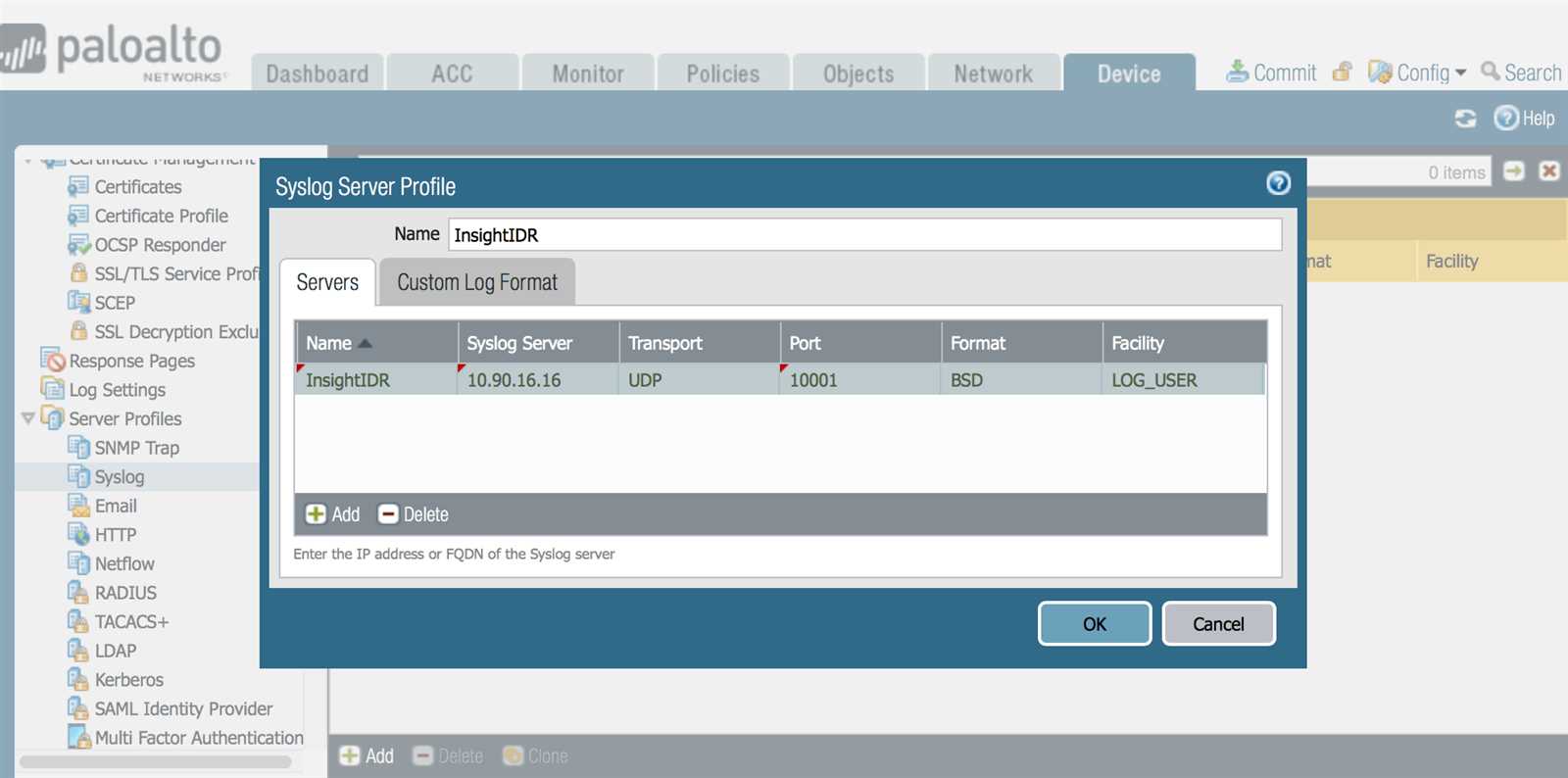
In the realm of safeguarding sensitive information, the practice of preventing inadvertent or malicious leakage of data emerges as a paramount concern. This discipline, often referred to as data loss prevention (DLP), encompasses a multifaceted approach to mitigate the risks associated with unauthorized data disclosure. Delving into the intricacies of DLP entails an exploration of techniques, strategies, and technologies aimed at fortifying the confidentiality and integrity of valuable data assets.
- Data Protection Strategies: Within the landscape of DLP, various strategies are employed to erect barriers against potential data breaches. These encompass a spectrum of proactive measures designed to thwart unauthorized access, transmission, or dissemination of sensitive data.
- Risk Mitigation Techniques: Effectively combating data loss necessitates the implementation of tailored techniques to identify, assess, and address vulnerabilities within an organization’s data ecosystem. By proactively identifying potential points of weakness, preemptive measures can be instituted to minimize the likelihood of data leakage.
- Compliance Imperatives: Compliance frameworks serve as a cornerstone in shaping DLP protocols, mandating adherence to industry-specific regulations and standards. Achieving regulatory compliance not only augments an organization’s resilience against data breaches but also fosters trust and transparency with stakeholders.
- Behavioral Analytics: A nuanced understanding of user behavior lies at the crux of effective DLP implementations. By leveraging advanced analytics and machine learning algorithms, organizations can discern anomalous patterns indicative of potential data exfiltration attempts, thereby enabling proactive intervention.
- Technological Enablers: The efficacy of DLP initiatives is bolstered by an arsenal of technological enablers spanning encryption protocols, access controls, and intrusion detection systems. Harnessing these tools in concert empowers organizations to fortify their defense mechanisms against evolving threats.
Embarking on a journey to comprehend the nuances of data loss prevention unveils a multifaceted discipline underscored by the fusion of strategic foresight, technological innovation, and regulatory compliance. By embracing a holistic approach to safeguarding sensitive data, organizations can navigate the intricate terrain of cybersecurity with confidence and resilience.
Key Features of Data Leakage Prevention Solution
In this section, we delve into the essential aspects of the Data Leakage Prevention (DLP) solution provided by Palo Alto Networks. Understanding the pivotal features of this robust system is crucial for businesses aiming to safeguard their sensitive data from unauthorized access, breaches, and inadvertent leaks.
Advanced Content Detection
Robust Content Analysis: The DLP solution employs advanced algorithms to meticulously scrutinize data in various formats, including text documents, images, and multimedia files. By utilizing sophisticated pattern recognition techniques, it identifies sensitive information such as personally identifiable information (PII), intellectual property, and financial data.
Contextual Understanding: Beyond mere keyword matching, the system comprehends the contextual nuances of data, enabling it to distinguish between legitimate usage and potential threats. Through semantic analysis and natural language processing (NLP), it accurately discerns the meaning and intent behind content, enhancing the efficacy of data protection measures.
Granular Policy Enforcement

Customizable Policies: Administrators can define tailored policies based on organizational requirements, regulatory compliance standards, and industry-specific mandates. This granular approach allows precise control over data handling, dictating permissible actions such as access, sharing, and storage across diverse user groups and network environments.
Dynamic Remediation: In response to policy violations or suspicious activities, the DLP solution initiates real-time remediation actions to mitigate risks and prevent data exfiltration. Depending on the severity of the incident, it may enforce automatic encryption, quarantine, or blocking measures, ensuring swift and decisive responses to potential threats.
Implementing Data Loss Prevention Solutions: Key Strategies
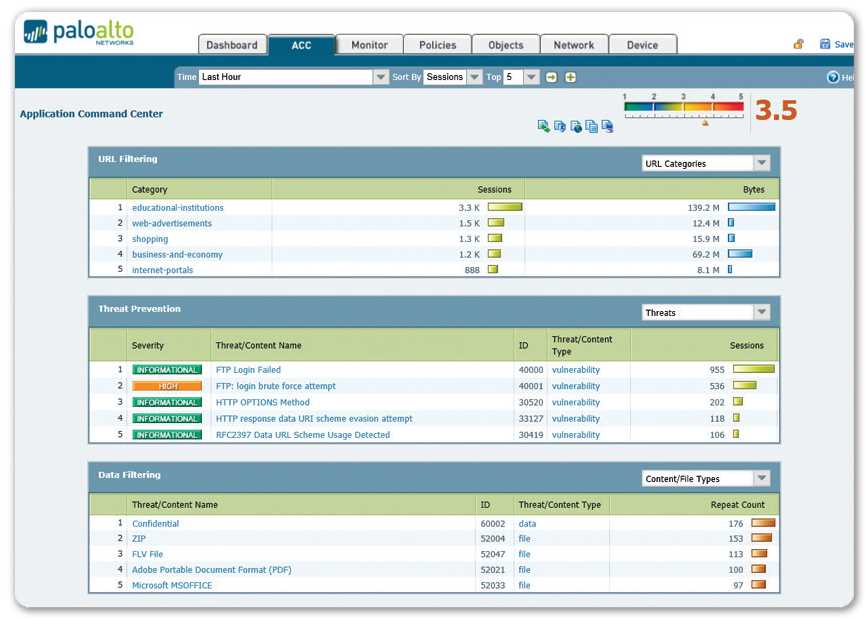
In this section, we delve into the essential approaches for deploying effective data loss prevention (DLP) measures. Understanding the intricacies of safeguarding sensitive information requires a comprehensive strategy that encompasses various facets of security protocols.
1. Policy Framework Development
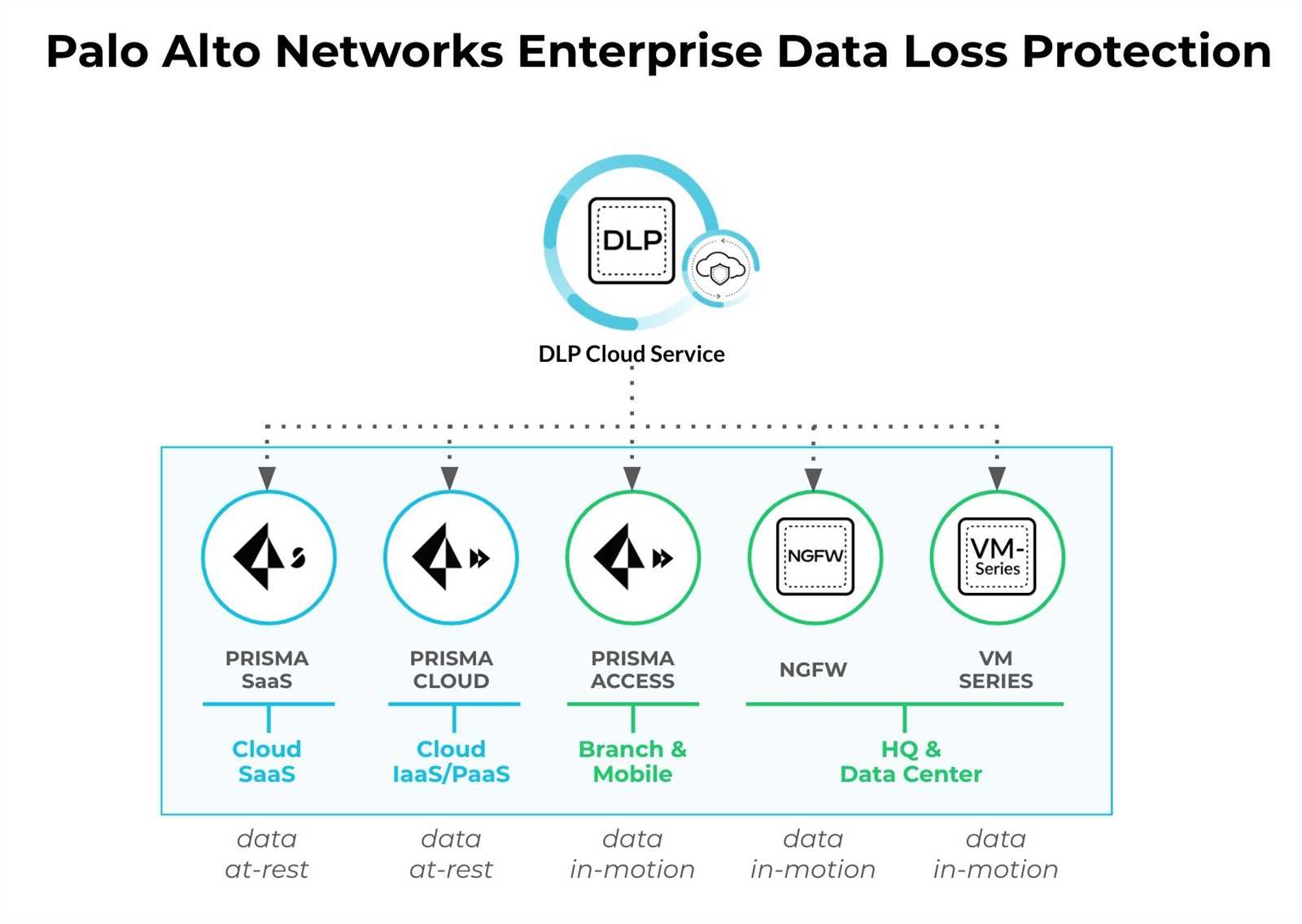
One cornerstone of successful DLP implementation lies in crafting a robust policy framework. This framework serves as the blueprint for delineating permissible data usage, defining sensitive information categories, and outlining protocols for data handling and transmission.
2. Employee Awareness and Training
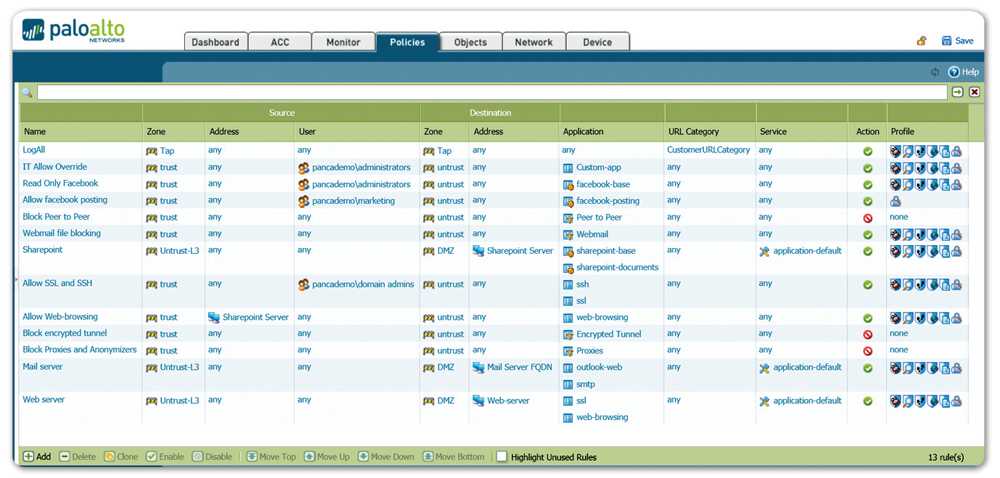
No DLP strategy is complete without a strong emphasis on employee education and awareness. Training programs should equip staff with the knowledge to recognize potential data breach risks, understand the importance of compliance with security policies, and grasp the implications of mishandling sensitive data.
| Best Practices | Implementation Strategies |
|---|---|
| Data Classification | Employ automated classification tools to categorize data based on its sensitivity level, facilitating targeted DLP measures. |
| Encryption | Implement robust encryption protocols to safeguard data both in transit and at rest, mitigating the risk of unauthorized access. |
| Monitoring and Reporting | Deploy real-time monitoring solutions coupled with comprehensive reporting mechanisms to promptly identify and address security incidents. |
By adhering to these best practices and tailoring them to suit organizational needs, enterprises can fortify their defenses against data breaches and uphold the integrity of their sensitive information.