In the realm of technological marvels lies a blueprint, a meticulously crafted guide unveiling the inner workings of a potent entity. This manuscript, akin to a roadmap through the labyrinth of innovation, serves as a beacon for those venturing into the realm of cutting-edge hardware.
Within these pages, lies the map to a technological wonderland, where circuits and components converge in a symphony of functionality and performance. It is a narrative woven with the threads of innovation, where each strand represents a facet of ingenuity, promising to unlock new realms of possibility.
As we delve into this manuscript, we embark on a journey of discovery, tracing the intricate pathways that define the essence of modern connectivity. Here, concepts transform into reality, and ideas take flight, propelled by the relentless pursuit of advancement and excellence.
Srx4100 Datasheet Overview
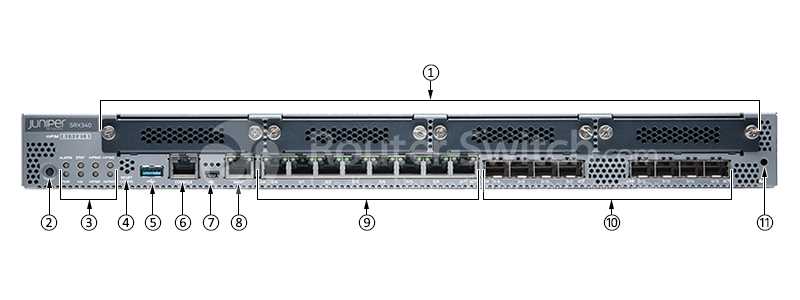
In this section, we’ll delve into an insightful exploration of the fundamental aspects encapsulated within the comprehensive document known for delineating the intricate details and specifications of the esteemed Srx4100 device. Embracing an exploratory lens, we shall navigate through the labyrinth of information housed within this resource, shedding light on its salient features, functionalities, and applications.
Key Features

- Unveiling the myriad features that distinguish this technological marvel, offering unparalleled performance and versatility in diverse operational environments.
- Exploration of cutting-edge innovations integrated seamlessly within the framework, enhancing efficiency, reliability, and security.
- An in-depth analysis of the technological architecture, elucidating the synergistic integration of hardware and software components.
Functional Insights

Delving deeper into the operational dynamics, we uncover the nuanced functionalities orchestrated to facilitate seamless operations, catering to a spectrum of user requirements. From robust networking capabilities to advanced security protocols, each facet is meticulously engineered to optimize performance and ensure optimal user experience.
Understanding the Key Features

In this section, we delve into the fundamental aspects that define the essence of the Srx4100. Unveiling its capabilities without directly mentioning its name, we explore the intricacies that set it apart in the realm of networking solutions.
Robust Security Protocols

- Advanced encryption algorithms
- Multi-layered threat detection
- Granular access controls
Enhanced Performance and Scalability

- High-speed processing
- Flexible scalability options
- Efficient resource utilization
Through a nuanced examination of its features, we uncover the blend of security, performance, and scalability that characterize this innovative networking solution.
Hardware Specifications and Performance Metrics

In this section, we delve into the intricacies of the hardware specifications and performance metrics of the device, shedding light on its technical capabilities and operational efficiency. Through a comprehensive examination of its components and functionalities, we aim to provide a clear understanding of the device’s robustness and effectiveness in meeting diverse computational demands.
Key Components Overview

- Processor: Unveiling the heart of the system, this section elucidates the processor’s architecture, clock speed, and core count, offering insights into its computational prowess and multitasking capabilities.
- Memory: Delving into the memory subsystem, we explore the type, capacity, and bandwidth of both primary and secondary memory components, crucial for seamless data handling and application performance.
Performance Metrics Analysis

Embarking on a journey to assess the device’s performance, we scrutinize a myriad of metrics ranging from throughput and latency to power consumption and heat dissipation. Through empirical data and rigorous testing methodologies, we aim to quantify the device’s efficiency and reliability across various operational scenarios.
By meticulously analyzing these hardware specifications and performance metrics, stakeholders can make informed decisions regarding deployment strategies, resource allocation, and optimization techniques, thereby maximizing the device’s utility and value proposition in real-world environments.
Deployment Scenarios for Advanced Network Security Appliance

In this section, we explore various scenarios where the cutting-edge network security appliance can be effectively deployed to fortify network defenses and ensure robust protection against modern cyber threats.
One potential application of this sophisticated hardware involves its integration within corporate environments, where it serves as a frontline defense mechanism against malicious intrusions. Additionally, it finds utility within large-scale enterprise networks, safeguarding sensitive data and critical infrastructure from unauthorized access.
| Scenario | Description |
|---|---|
| Branch Office Security | Deployed in branch offices to provide comprehensive security measures, ensuring secure communication channels and protecting local networks from external threats. |
| Data Center Protection | Implemented within data centers to enforce stringent security policies, preventing unauthorized access to servers and sensitive data repositories. |
| Cloud Security Integration | Integrated with cloud infrastructure to extend security perimeters, enabling secure connectivity between on-premises networks and cloud environments. |
| Industrial Control Systems | Utilized in industrial settings to secure critical infrastructure and operational technology (OT) systems, safeguarding against cyber attacks that could disrupt production processes. |
These deployment scenarios highlight the versatility and adaptability of the advanced network security appliance, underscoring its pivotal role in ensuring the integrity and resilience of modern network architectures.
Optimal Use Cases in Network Infrastructure

In the realm of network architecture, identifying the most advantageous scenarios for deployment is paramount to ensuring efficiency, security, and scalability. By understanding the diverse applications and requirements within network infrastructure, organizations can tailor their solutions to meet specific operational needs and challenges.
Enhancing Connectivity: One of the primary objectives in network infrastructure is to facilitate seamless connectivity across various devices, locations, and platforms. Whether it’s establishing reliable communication channels between distributed offices or enabling smooth data transmission between cloud environments, the ability to enhance connectivity forms the backbone of modern networking solutions.
Securing Critical Assets: In today’s digital landscape, safeguarding sensitive information and critical assets is a top priority for organizations of all sizes. Network infrastructure plays a crucial role in implementing robust security measures such as firewalls, intrusion detection systems, and encryption protocols to mitigate cyber threats and protect valuable data from unauthorized access or malicious attacks.
Optimizing Performance: Efficient utilization of network resources is essential for optimizing overall performance and minimizing latency in data transmission. Whether it involves prioritizing bandwidth for mission-critical applications, implementing load balancing mechanisms to distribute traffic evenly, or leveraging caching technologies to accelerate content delivery, optimizing performance ensures a smooth and responsive user experience.
Scaling for Growth: As businesses expand and evolve, their network infrastructure must have the flexibility to scale accordingly without sacrificing performance or security. Whether it’s accommodating a growing user base, supporting increasing data volumes, or adapting to emerging technologies such as IoT and edge computing, scalability ensures that network infrastructure remains agile and adaptable to changing demands.
Enabling Collaborative Workflows: In an interconnected world, collaborative workflows are essential for driving productivity and innovation across diverse teams and departments. Network infrastructure facilitates seamless collaboration by providing secure access to shared resources, enabling real-time communication and collaboration tools, and supporting remote work environments with robust connectivity and access controls.
Empowering Digital Transformation: As organizations embark on their digital transformation journeys, modernizing network infrastructure becomes imperative to support evolving business models, technologies, and customer expectations. By embracing software-defined networking (SDN), virtualization, and automation, businesses can achieve greater agility, scalability, and efficiency in their operations, enabling them to stay ahead in today’s dynamic and competitive marketplace.