
Unlocking the intricacies of a technological marvel requires a journey into the heart of innovation, where microcircuitry reigns supreme. Delving into the blueprint of this modern wonder unveils a labyrinth of pathways, each carrying the promise of enhanced connectivity and efficiency.
Within the realm of digital architecture lies a hidden gem, a microcosm of functionality meticulously crafted to redefine the boundaries of possibility. Here, we embark on a voyage to dissect the essence of a revolutionary component, where every node and pathway converges to orchestrate a symphony of data transmission.
Unveiling the anatomy of this technological enigma unveils a tapestry of innovation, where intricate designs meld with cutting-edge functionality. Beyond the veil of complexity lies a realm of potential, where the fusion of science and engineering births a new era of connectivity.
Understanding the Bcm43013 Documentation: Core Elements and Characteristics
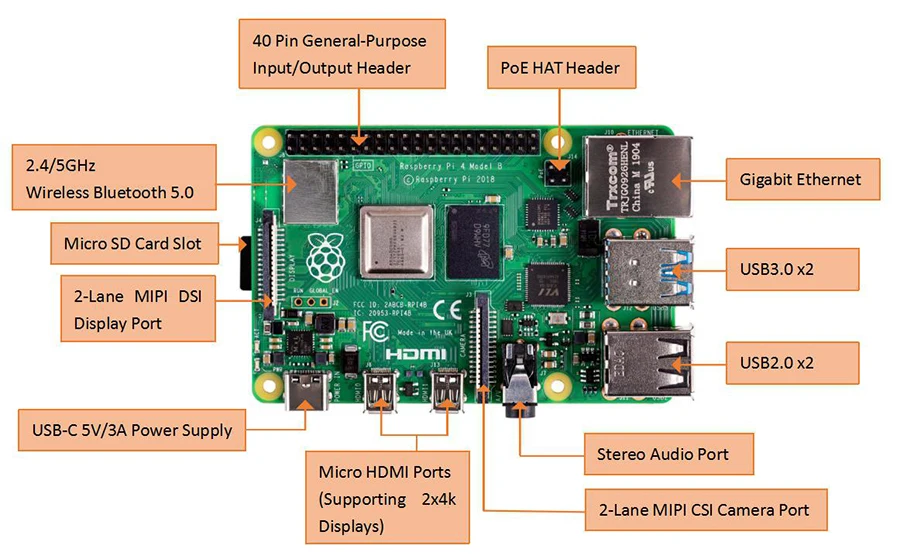
In exploring the intricacies of the Bcm43013 documentation, we delve into the foundational aspects and distinguishing features of this technological marvel. Through comprehensive analysis, we unveil the essential components and functionalities encapsulated within this resource.
Core Components
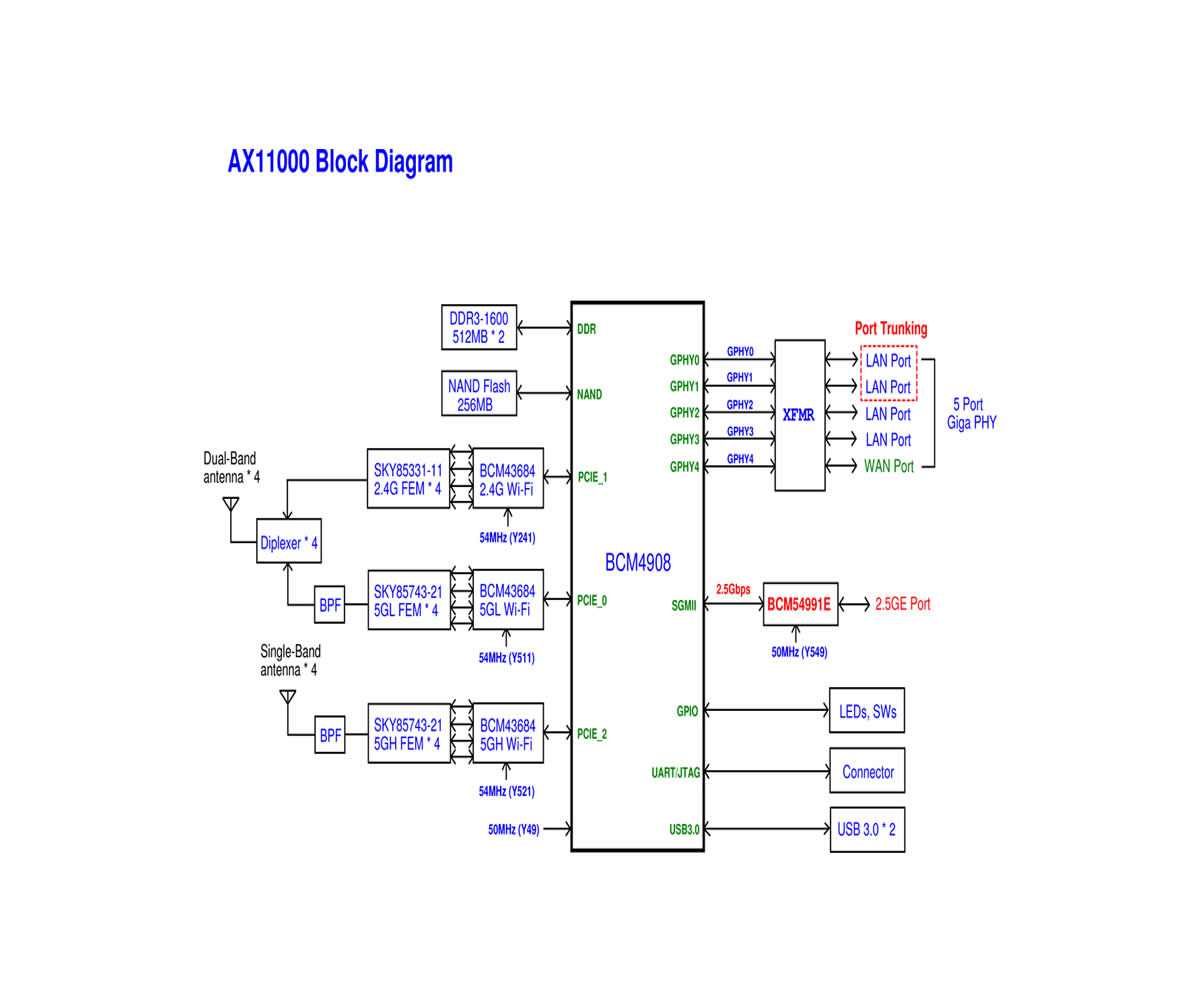
The documentation elucidates the fundamental building blocks that form the backbone of the Bcm43013 system. It delineates the intricacies of its architecture, highlighting the pivotal elements that facilitate seamless operation.
Key Features
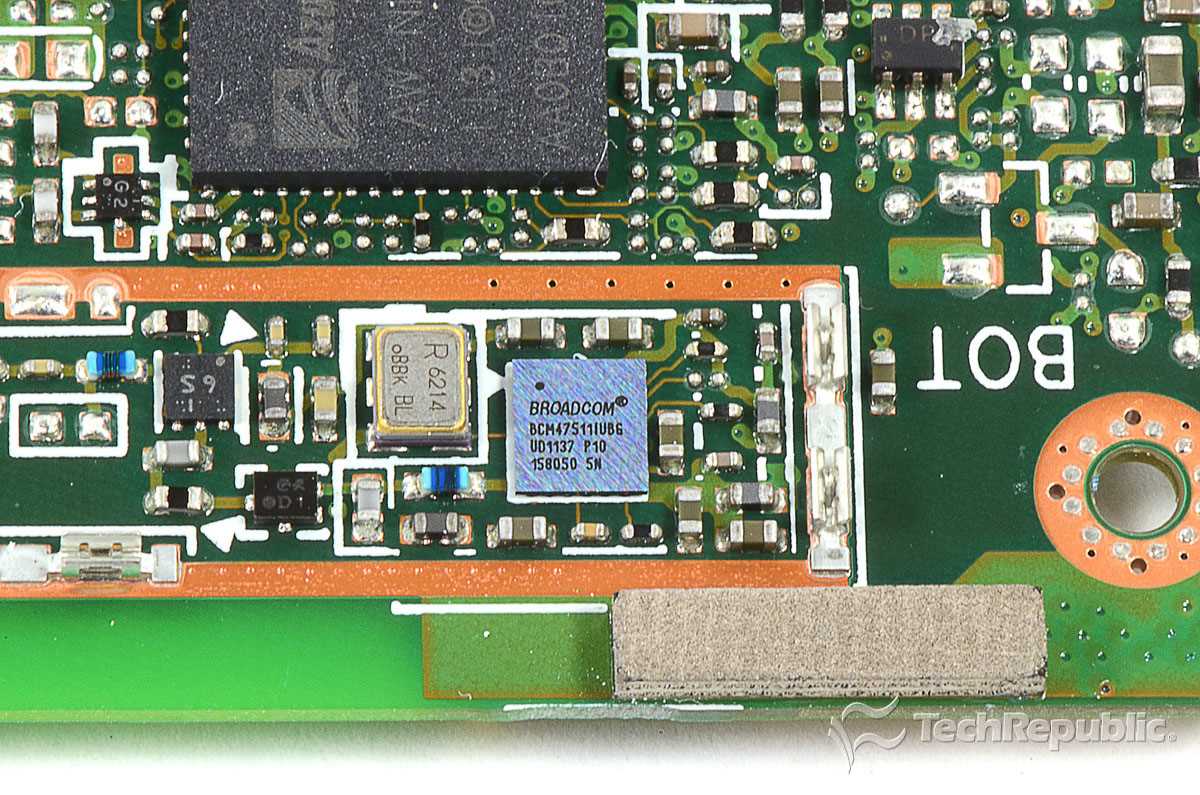
Embedded within the documentation are the distinguishing features that set the Bcm43013 apart in the realm of technology. From advanced functionalities to innovative solutions, these features define the essence of this cutting-edge device.
| Aspect | Description |
|---|---|
| Functionality | Explores the operational capabilities and performance metrics of the Bcm43013. |
| Compatibility | Examines the adaptability and interoperability of the Bcm43013 with diverse systems and platforms. |
| Connectivity | Illustrates the seamless integration and connectivity options provided by the Bcm43013. |
| Security | Addresses the robust security features implemented within the Bcm43013 framework. |
Exploring the Hardware Specifications and Connectivity Options

In this section, we delve into the intricate details of the hardware specifications and various connectivity options offered by the device in question. By dissecting its physical components and examining its potential for connectivity, we aim to provide a comprehensive overview of its capabilities and functionalities.
Hardware Specifications: Unveiling the inner workings of the device, we scrutinize its hardware specifications, including but not limited to its processing power, memory capacity, and peripheral support. Through a meticulous examination of its architecture and components, we shed light on the underlying mechanisms that drive its performance.
Connectivity Options: Beyond its internal specifications, we explore the diverse connectivity options available to users. From traditional wired connections to cutting-edge wireless technologies, we uncover the array of methods through which the device can interact with external systems and networks. Whether it’s through Ethernet, Wi-Fi, Bluetooth, or other protocols, we analyze the versatility and adaptability of its connectivity features.
Exploring Integration: Furthermore, we consider how the device’s hardware specifications intersect with its connectivity options to facilitate seamless integration into various environments. By examining compatibility with different platforms and ecosystems, we assess the device’s ability to communicate and collaborate within diverse technological landscapes.
Optimizing Performance: Finally, we discuss strategies for optimizing performance by harnessing the full potential of the device’s hardware capabilities and connectivity options. Through fine-tuning settings, utilizing advanced protocols, and leveraging synergies between components, we explore avenues for maximizing efficiency and efficacy in real-world applications.
Exploring the Programming Interface and Firmware Integration
In this section, we delve into the intricate mechanisms governing the interaction between software and hardware components within the framework of the innovative BCM43013 module. Our focus lies on elucidating the pathways through which firmware seamlessly integrates with the programming interface, fostering optimal functionality and performance.
Understanding the Programming Interface

The programming interface serves as the conduit through which commands are conveyed and executed, facilitating the intricate interplay between the underlying firmware and external software entities. Through meticulous analysis, we uncover the underlying protocols and communication channels that underpin this interface, shedding light on its pivotal role in orchestrating the module’s operations.
Firmware Integration: Bridging the Divide
At the heart of the BCM43013 module lies its firmware, a sophisticated amalgamation of code and data structures meticulously crafted to optimize performance and functionality. Within this realm, we explore the seamless integration of firmware with the broader ecosystem, traversing the intricacies of initialization routines, event handling mechanisms, and data processing pipelines. Through this exploration, we illuminate the symbiotic relationship between firmware and software, elucidating how they collaboratively navigate the digital landscape to deliver unparalleled functionality.
| Key Concepts | Highlights |
|---|---|
| Programming Interface | – Protocol analysis – Command execution |
| Firmware Integration | – Initialization routines – Event handling mechanisms – Data processing pipelines |
Optimizing Performance Through Software Configuration

In the pursuit of enhancing operational efficiency and maximizing system potential, the strategic manipulation of software configurations emerges as a pivotal avenue. By delving into the intricacies of software settings and parameters, significant strides can be made towards augmenting overall performance and functionality.
Within the realm of software optimization, a nuanced understanding of system dynamics is paramount. Through meticulous calibration and fine-tuning of software components, synergistic enhancements can be achieved, bolstering the system’s capacity for seamless operation and heightened responsiveness.
Furthermore, the strategic alignment of software configurations with specific operational requirements serves as a catalyst for unlocking latent potential and realizing optimal performance thresholds. By tailoring configurations to suit diverse usage scenarios, the versatility and adaptability of the system are magnified, enabling it to adeptly navigate varying demands and challenges.
Moreover, the iterative refinement of software configurations engenders a culture of continuous improvement, wherein each adjustment represents an opportunity to refine and optimize system behavior. Through empirical observation and data-driven analysis, the efficacy of software configurations can be systematically evaluated and refined, culminating in a harmonized ecosystem characterized by peak efficiency and reliability.
In essence, the art of optimizing performance through software configuration transcends mere manipulation of settings; it embodies a holistic approach to system enhancement, grounded in a synthesis of technical acumen, strategic foresight, and a relentless commitment to excellence.
Security Features and Compliance Overview
In this section, we delve into the robust security measures and regulatory adherence embodied within the specifications of the Bcm43013. By exploring its security provisions and compliance standards, we navigate through a landscape of safeguarding mechanisms and regulatory frameworks ensuring the integrity and confidentiality of data transmission and reception.
The Bcm43013 intricately integrates a spectrum of security features designed to fortify its operational ecosystem against potential vulnerabilities and breaches. Emphasizing confidentiality, integrity, and availability, these features encapsulate a comprehensive shield against unauthorized access, malicious exploits, and data manipulation.
Moreover, compliance with industry standards and regulatory mandates forms the cornerstone of the Bcm43013’s governance framework. Adhering to stringent protocols and certifications, it ensures alignment with prevailing regulations, fostering trust and confidence among stakeholders while mitigating legal and reputational risks.
Through a synthesis of advanced encryption protocols, access control mechanisms, and regulatory compliance, the Bcm43013 epitomizes a paradigm of security by design. It embodies a commitment to safeguarding sensitive information and upholding regulatory imperatives, thereby instilling resilience and trust within its operational domain.