
Embark on a journey to explore the dynamic spectrum of a cutting-edge network fortress. This article serves as a guide through the intricate labyrinth of technological prowess, shedding light on the formidable capabilities and versatile functionalities encapsulated within.
Discover the unyielding strength of an architectural marvel designed to navigate the ever-evolving landscape of digital security. Delve into its arsenal of features crafted to fortify networks against the relentless onslaught of modern cyber threats.
From robust defenses to agile response mechanisms, each facet unveils a facet of resilience, empowering enterprises to traverse the digital realm with confidence and certainty. Join us as we decipher the blueprint of innovation, illuminating pathways to a safer, more secure tomorrow.
Understanding the Specifications of Fortigate 600E

Delving into the intricacies of Fortigate 600E documentation unveils a comprehensive framework for grasping the capabilities and functionalities of this advanced security appliance. This section aims to dissect and elucidate the key aspects of the Fortigate 600E specifications, shedding light on its performance metrics, feature set, and deployment scenarios.
Performance Metrics
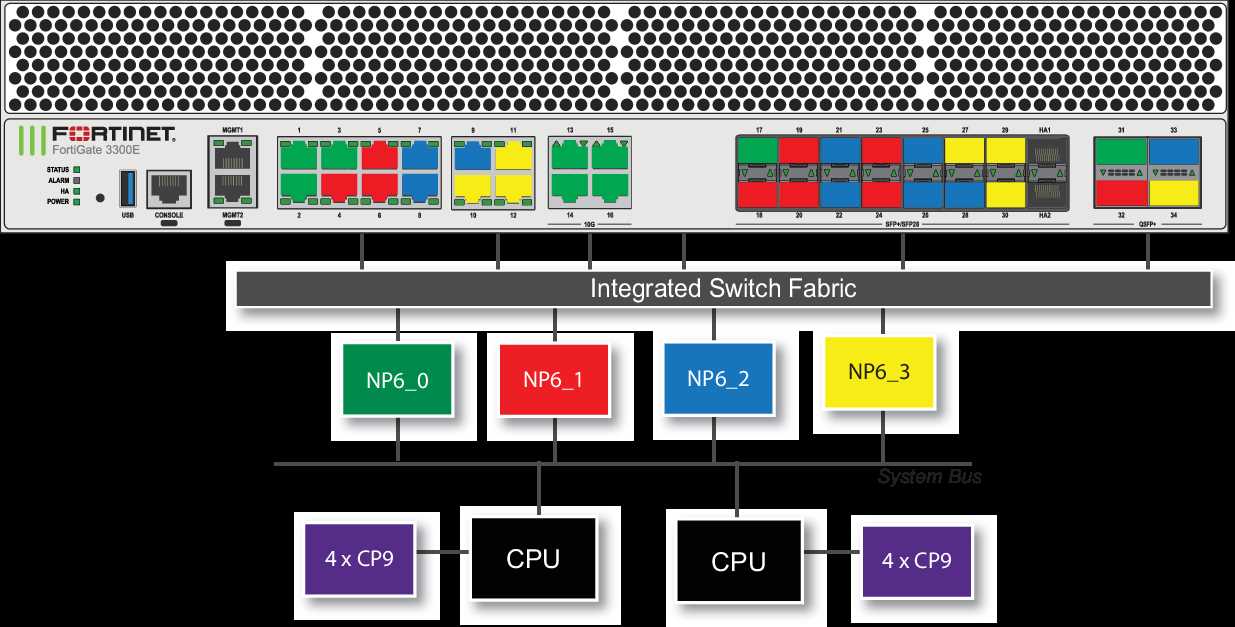
- Throughput: Explore the throughput benchmarks, encompassing both firewall and VPN performance, to gauge the device’s capacity in handling network traffic.
- Connection Limits: Investigate the maximum concurrent sessions and connections per second to discern the scalability of the appliance in various network environments.
- Security Services: Evaluate the efficacy of integrated security services, such as intrusion prevention, antivirus, and application control, in safeguarding network assets.
Feature Set
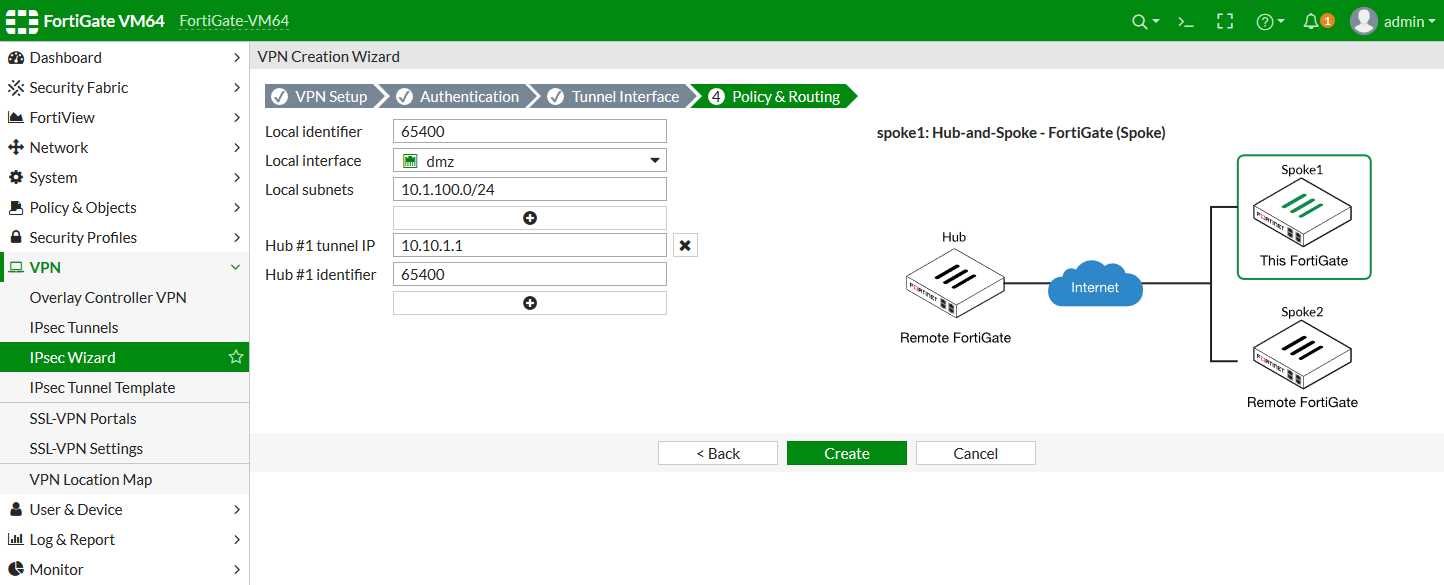
- Networking Capabilities: Examine the networking features, including routing protocols, VLAN support, and WAN optimization functionalities, to understand the device’s role in network infrastructure.
- Management and Visibility: Delve into management interfaces, logging capabilities, and reporting tools to grasp the ease of administration and visibility offered by the appliance.
- Integration Options: Explore integration possibilities with third-party systems and platforms, assessing interoperability and extensibility for seamless integration into existing infrastructures.
By dissecting the specifications of Fortigate 600E with a keen eye for detail, stakeholders can make informed decisions regarding its deployment, ensuring optimal performance and security posture within their networks.
Key Features and Specifications
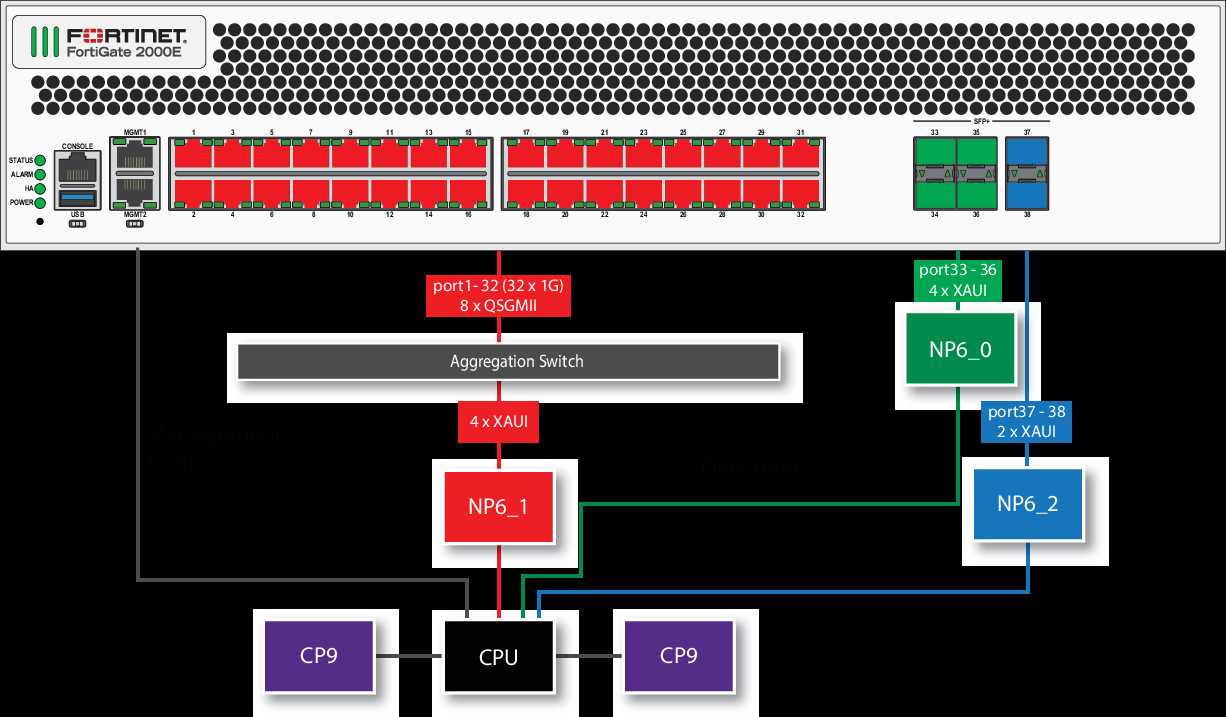
In this section, we delve into the distinguishing characteristics and technical details of the system, providing insights into its functionality and performance. Discover the essential attributes and metrics that define the capabilities of this robust solution.
Advanced Functionality
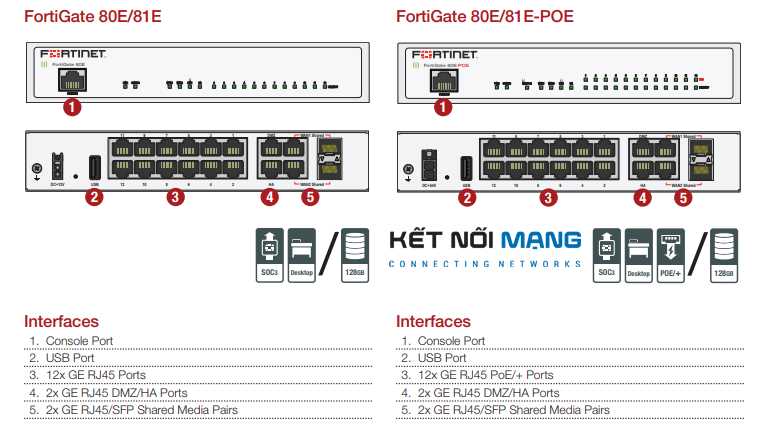
Explore the array of advanced features engineered to enhance security, streamline operations, and optimize network performance. From dynamic threat intelligence to comprehensive monitoring capabilities, uncover the tools designed to fortify your digital infrastructure.
Technical Specifications
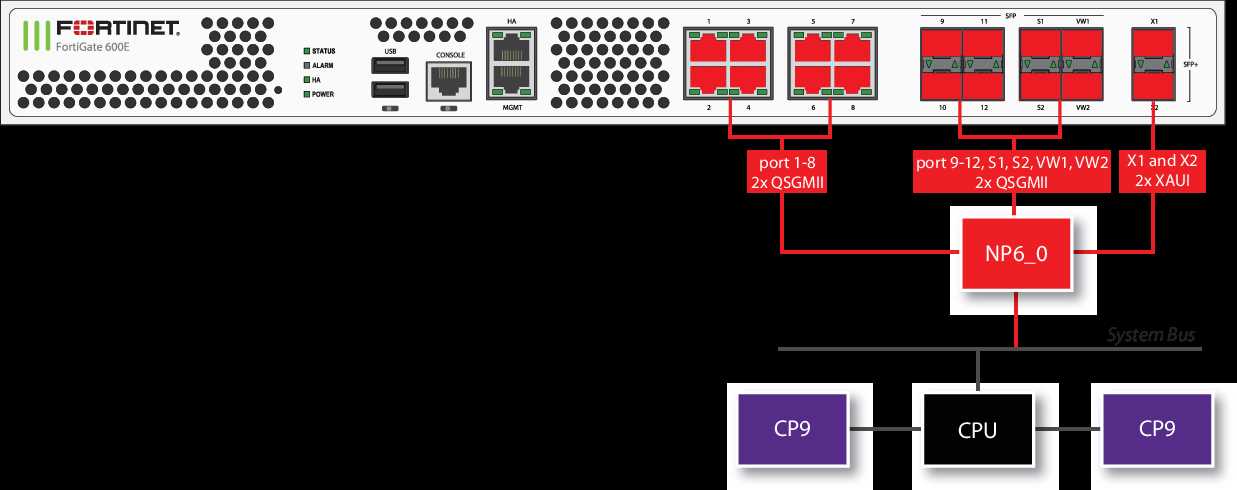
Delve into the technical specifications outlining the hardware and software components, along with their respective configurations and capabilities. Gain a deeper understanding of the system’s architecture, performance metrics, and compatibility requirements through detailed specifications and performance benchmarks.
| Feature | Description |
|---|---|
| Security Protocols | Implemented protocols ensuring data integrity and confidentiality. |
| Throughput | Maximum data transfer rate supported by the system. |
| Scalability | The system’s capacity for expansion and accommodating growing network demands. |
| Management Interface | User-friendly interface for configuring and monitoring system settings. |
| Hardware Specifications | Details regarding the system’s physical components and specifications. |
| Software Features | Overview of software functionalities and capabilities. |
Deployment Scenarios and Use Cases

Exploring the versatile landscapes where our solution thrives, this section delves into various scenarios and practical applications, showcasing the adaptability and efficacy of our cutting-edge technology. By examining real-world contexts and potential use cases, we illuminate the breadth of possibilities for leveraging this innovative system.
Network Security Enhancements

Within the intricate tapestry of network architecture, our solution emerges as a stalwart guardian, fortifying digital perimeters against a myriad of threats. Whether safeguarding sensitive data in enterprise environments or bolstering the resilience of critical infrastructure, the system stands poised to confront evolving cyber challenges with unwavering resolve. From thwarting malware intrusions to orchestrating sophisticated access controls, it embodies a paradigm shift in proactive defense mechanisms.
Optimized Performance and Scalability
Amidst the dynamic demands of modern connectivity, our solution shines as a beacon of reliability and scalability. Tailored to accommodate diverse infrastructural frameworks, it seamlessly integrates into existing ecosystems, empowering organizations to optimize performance without compromising on security. From small-scale deployments requiring streamlined efficiency to expansive networks necessitating robust scalability, the system offers a bespoke solution to every deployment scenario, ensuring seamless operations across the digital landscape.
Performance Metrics and Benchmarks

In this section, we delve into the intricate details of the operational prowess and evaluation criteria of the robust device under scrutiny. We embark on a journey to unravel the performance metrics and benchmarks that serve as the litmus test for its efficacy and efficiency.
Within the realm of operational assessment, a comprehensive exploration awaits, encompassing the velocity at which data traverses through the system, the agility exhibited in processing diverse protocols, and the resilience demonstrated under varying loads.
- Throughput: Unveiling the swiftness with which information navigates across the architecture, illustrating its capacity to handle voluminous data streams.
- Latency: Delving into the temporal intervals incurred during data transmission and reception, elucidating the responsiveness inherent within the framework.
- Packet Loss: Scrutinizing the fidelity of data delivery, delineating the proficiency in preserving packet integrity amidst the tumult of network dynamics.
Moreover, the benchmarks set forth provide a comparative landscape, elucidating the device’s performance against industry standards and peer contenders. This comparative analysis offers insights into its standing within the competitive arena and delineates avenues for further enhancement.
Embarking on this analytical expedition, we navigate through a labyrinth of metrics and benchmarks, unraveling the essence of operational excellence encapsulated within the device’s core functionalities.