Exploring the intricacies of the latest technological marvels is akin to delving into a labyrinth of innovation and ingenuity. In the realm of digital architecture and hardware prowess, there exists a compendium of knowledge that serves as the guiding beacon for enthusiasts and professionals alike. Within this expansive domain, lies a treasure trove of information meticulously crafted to illuminate the capabilities and functionalities of groundbreaking apparatus.
Embark upon a journey where words transcend mere descriptors and metamorphose into gateways of understanding. This journey, embarked upon by avid seekers of knowledge, is fueled by the desire to unravel the mysteries concealed within the fabric of modernity. Through the lens of technical documentation, we traverse the landscape of technological evolution, decoding the lexicon of innovation and deciphering the blueprints of progress.
Join us as we venture into the depths of insight, where each word resonates with the promise of enlightenment and each phrase unveils a facet of brilliance. Here, amidst the labyrinthine corridors of technical literature, we encounter a beacon of illumination known by many names – a compendium, a manual, a guide. Yet, regardless of nomenclature, its essence remains immutable: to elucidate, to elucidate, to empower.
Exploring the Versatility of Firepower 3105 Documentation
Diving into the myriad functionalities and adaptability of this comprehensive resource unveils a world of possibilities. Within these pages lies a treasure trove of insights, strategies, and technical specifications, each serving as a key to unlock the potential of your endeavors. Delve into the depths of this documentation, and discover a wealth of information poised to elevate your understanding and proficiency.
Unraveling the intricacies and nuances of this multifaceted resource opens pathways to innovation and efficiency. With its rich tapestry of details and configurations, this compendium caters to a diverse audience of professionals and enthusiasts alike, facilitating an expansive array of applications and solutions.
Embark on a journey of exploration and discovery, as you navigate through the labyrinth of insights and possibilities enshrined within these pages. Equip yourself with the knowledge and insights necessary to forge ahead with confidence, empowered by the depth and breadth of this invaluable resource.
Unveiling Performance Metrics and Specifications
In this section, we delve into the intricate details and underlying intricacies of the performance metrics and specifications of the product at hand. Through a comprehensive analysis, we uncover the various dimensions of its operational capabilities and technical specifications, shedding light on its prowess in diverse scenarios.
| Performance Metric | Specification |
|---|---|
| Throughput | The rate at which data is processed and transferred, indicative of the device’s efficiency in handling data-intensive tasks. |
| Latency | The time taken for a data packet to travel from its source to its destination, elucidating the device’s responsiveness in real-time operations. |
| Packet Loss | The percentage of data packets lost during transmission, reflecting the reliability and robustness of the device’s network connectivity. |
| Concurrency | The maximum number of simultaneous connections the device can handle, showcasing its scalability and ability to support high traffic volumes. |
| Security Features | A comprehensive overview of the device’s built-in security measures, including firewall capabilities, intrusion detection, and encryption protocols. |
Through a meticulous examination of these performance metrics and specifications, users can gain a profound understanding of the product’s capabilities and make informed decisions regarding its suitability for their specific requirements.
Integration Guide: Unleashing the Power of Firepower 3105

In this section, we delve into the intricate process of seamlessly integrating and harnessing the full potential of the cutting-edge Firepower 3105. Our aim is to provide a comprehensive roadmap for optimizing the utilization of this formidable technology without solely relying on its technical specifications or the standard datasheet.
Understanding Synergies
Unlocking the true prowess of this innovative solution hinges upon understanding the intricate interplay between its various components and functionalities. By identifying and capitalizing on synergies within the system, organizations can propel their cybersecurity strategies to new heights, fortifying their defenses against evolving threats.
Strategic Implementation Strategies
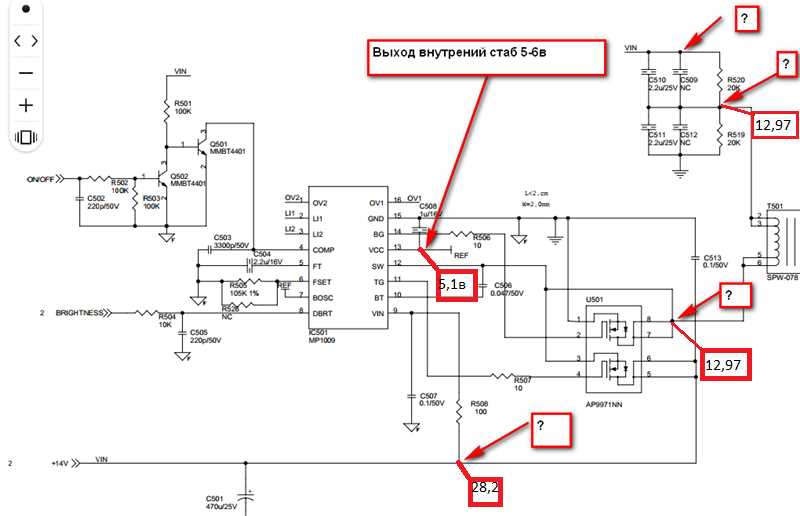
Maximizing the efficacy of the Firepower 3105 necessitates strategic deployment and implementation strategies tailored to the unique needs and challenges of individual environments. Through meticulous planning and execution, organizations can seamlessly integrate this technology into their existing infrastructure, augmenting their security posture while minimizing disruptions.
Security Enhancement Strategies with Firepower 3105 Datasheet

In the realm of fortifying digital defenses, leveraging the potential of the Firepower 3105 datasheet opens avenues for robust security fortification. This segment explores proactive measures and strategic maneuvers aimed at bolstering security resilience without explicit reliance on specific nomenclature.
1. Holistic Risk Mitigation Approach
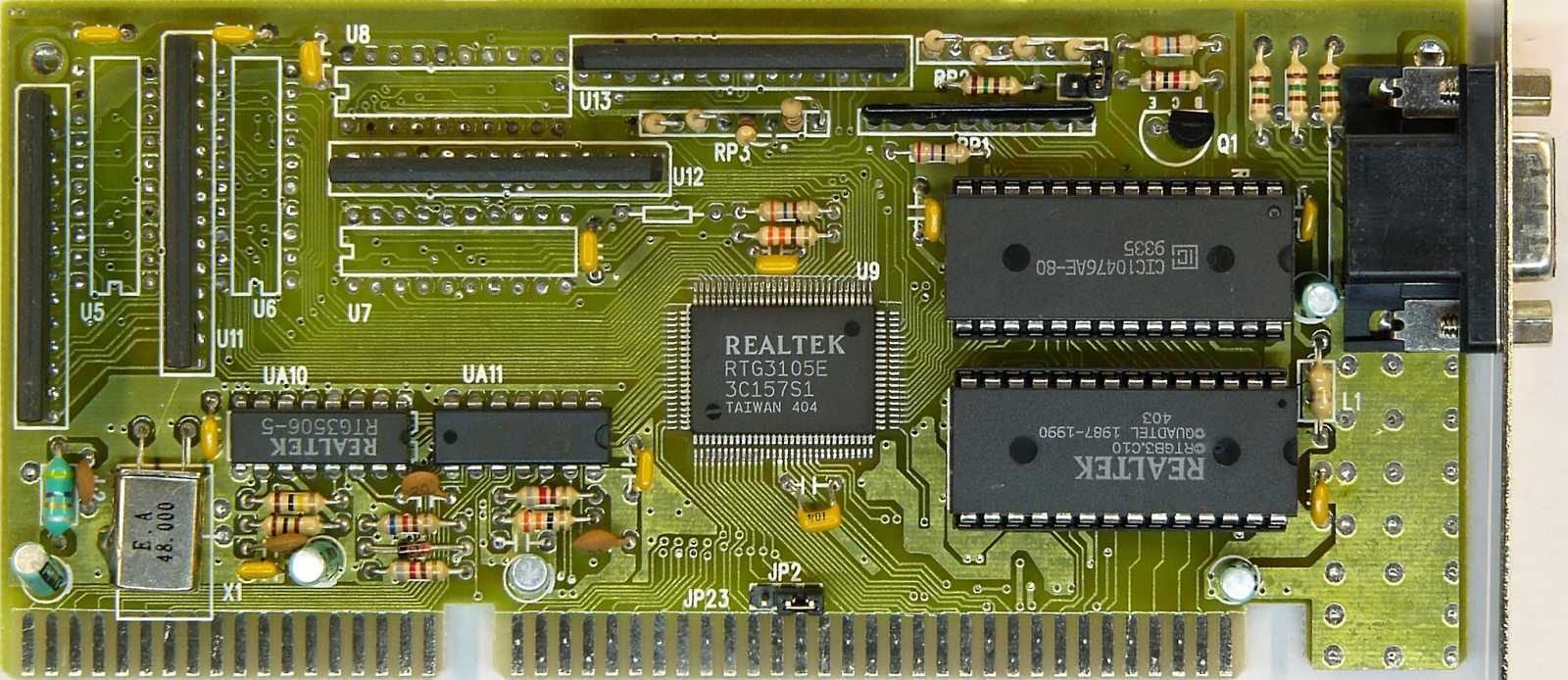
Embarking on a journey towards fortified security entails embracing a comprehensive approach to risk mitigation. By adopting a holistic perspective, organizations can navigate the labyrinth of potential vulnerabilities with acumen and foresight. This involves diligent scrutiny of operational landscapes, meticulous assessment of potential threats, and agile deployment of countermeasures.
2. Dynamic Threat Intelligence Integration
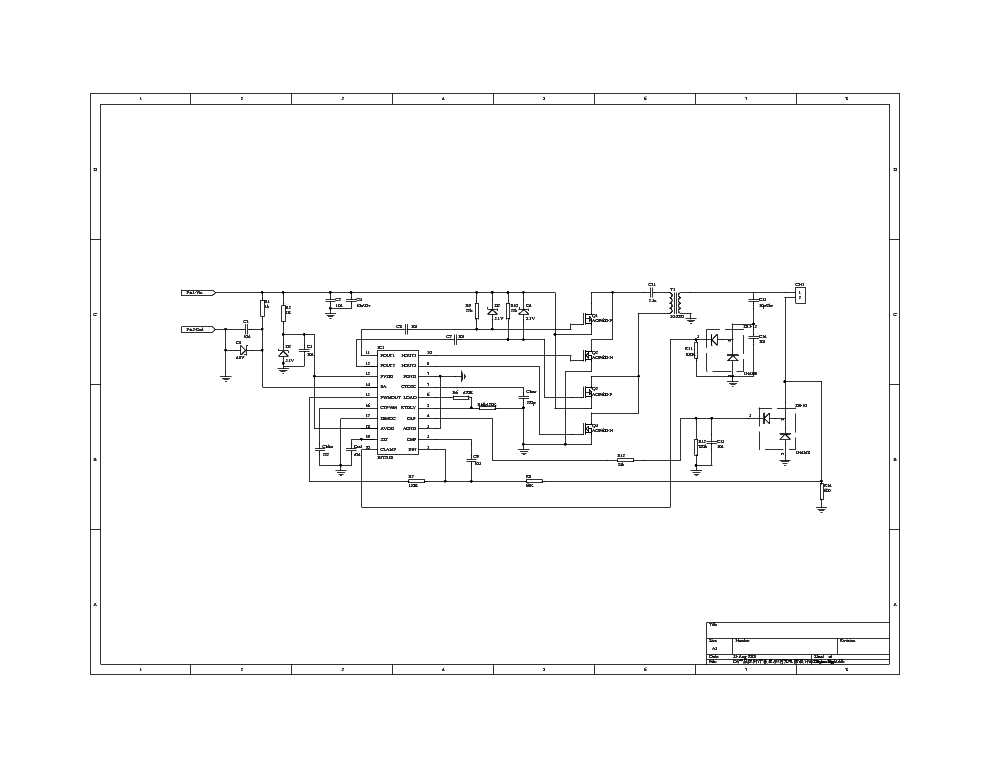
Empowering security frameworks with the infusion of dynamic threat intelligence serves as a linchpin in the quest for enhanced resilience. By integrating real-time threat insights, organizations can fortify their defenses against emergent risks and evolving attack vectors. This strategic amalgamation enables proactive identification and preemptive neutralization of looming threats, fostering a proactive security stance.
| Strategy | Description |
|---|---|
| Behavioral Analysis | Deploying advanced algorithms to discern anomalous behavioral patterns indicative of potential security breaches. |
| Vulnerability Scanning | Conducting regular scans to identify and remediate vulnerabilities within the digital infrastructure. |
| Access Control | Implementing stringent access control measures to restrict unauthorized entry and mitigate insider threats. |