Embark on a journey through the labyrinth of innovation as we delve into the intricacies of modern engineering marvels. Within the realm of electronic components lies a cornerstone of advancement, a nexus where precision meets potential. In this segment, we navigate the landscape of technological breakthroughs with a focus on the enigmatic Fg paradigms.
Unveiling the blueprint of cutting-edge functionality requires a keen eye for detail and a penchant for decoding the language of progress. In the tapestry of technical literature, one finds a treasure trove of insights, each term and specification a breadcrumb leading toward enlightenment. Among these, the Fg lexicon emerges, shrouded in the mystique of its capabilities and applications.
Prepare to traverse the corridors of ingenuity, where concepts meld into concrete realities and imagination fuels the engines of advancement. Through a lens of curiosity and inquiry, we navigate the Fg landscape, deciphering its essence and implications. Join us as we embark on an odyssey of discovery, charting the course of technological evolution through the enigmatic lens of Fg insights.
The Versatile Fg 100e: Exploring Key Features
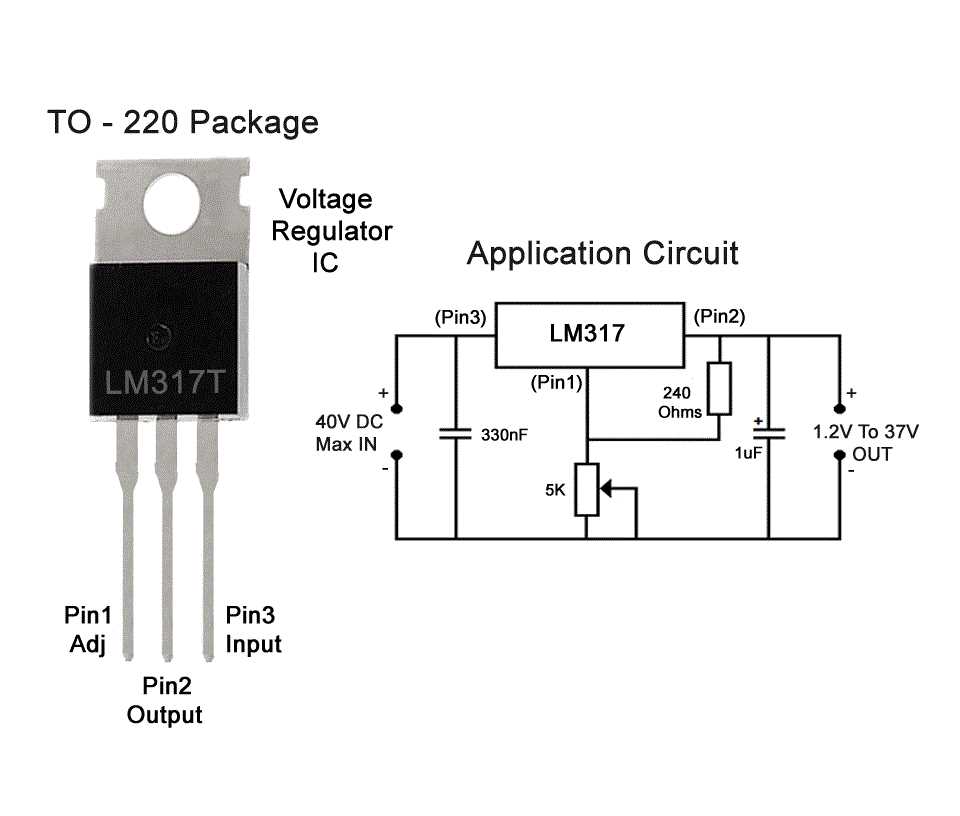
Delve into the multifaceted capabilities of the Fg 100e as we uncover its diverse range of functionalities and highlights. This section aims to illuminate the various attributes and performance aspects that make the Fg 100e a standout option for a myriad of applications.
- Flexibility: Discover how the Fg 100e adapts to a spectrum of tasks with its versatile design, catering to diverse industry needs.
- Functionality: Explore the array of features embedded within the Fg 100e, each contributing to its robust performance and usability across different scenarios.
- Performance: Uncover the prowess of the Fg 100e in delivering consistent and reliable results, ensuring optimal outcomes in various operational environments.
- Adaptability: Witness how the Fg 100e seamlessly integrates into existing systems, enhancing workflow efficiency and overall productivity.
- Versatility: Embrace the versatility of the Fg 100e as it tackles challenges across industries, from engineering to research, with ease and precision.
Through a comprehensive exploration of its key features, the Fg 100e emerges as not just a product, but a solution tailored to meet the dynamic demands of modern applications.
Performance Boost: Unraveling Speed and Efficiency
In the pursuit of enhancing operational capabilities and optimizing functionality, delving into the intricacies of performance acceleration is paramount. This section endeavors to dissect the mechanisms behind augmenting speed and efficacy without relying on specific references. By exploring various facets of enhancement strategies, this discourse aims to elucidate the means to elevate operational proficiency and resource utilization.
| Enhancement Techniques | Benefits |
|---|---|
| Optimization Algorithms | Enhanced computational efficiency, reduced processing overhead |
| Parallel Processing | Increased throughput, improved multitasking capabilities |
| Hardware Acceleration | Expedited task execution, minimized latency |
| Caching Mechanisms | Efficient data retrieval, reduced access time |
By meticulously dissecting these methodologies and their corresponding advantages, a comprehensive understanding of performance optimization emerges. Through strategic implementation and judicious utilization of these techniques, organizations can harness the full potential of their systems, fostering unparalleled efficiency and productivity.
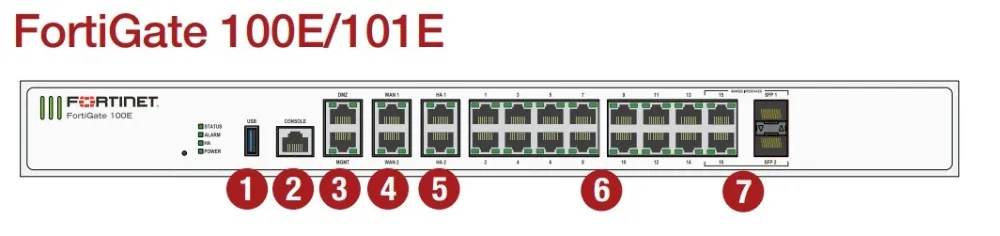
Enhanced Connectivity: Understanding Interface Options
In the realm of technological advancement, achieving optimal connectivity is paramount. As devices evolve and integrate into our daily lives, understanding the diverse array of interface options becomes essential. This section delves into the intricacies of interface possibilities, exploring the means by which devices communicate and interact.
Exploring Interface Diversity
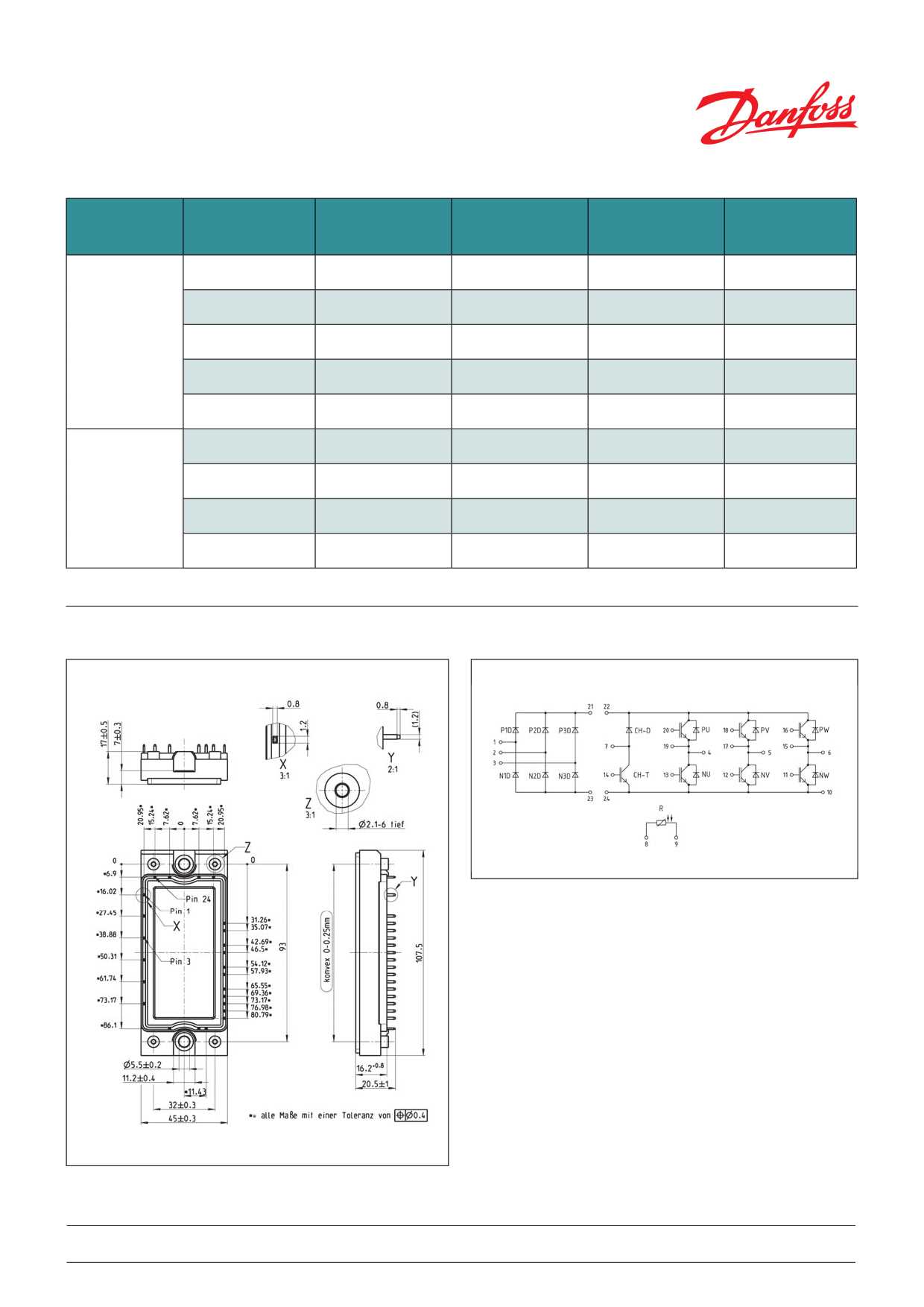
Interfaces serve as the conduits through which devices exchange information, facilitating seamless interaction. From traditional ports to wireless protocols, the landscape of connectivity options is vast and multifaceted. Each interface type offers distinct advantages and limitations, catering to diverse user needs and technological requirements.
Optimizing Communication Channels

Effective utilization of interface options entails strategic decision-making to optimize communication channels. Factors such as data transfer speed, compatibility, and reliability play pivotal roles in selecting the most suitable interface for a given application. By understanding the nuances of each option, users can harness the power of enhanced connectivity to propel technological innovation forward.
Advanced Security: Safeguarding Your Network
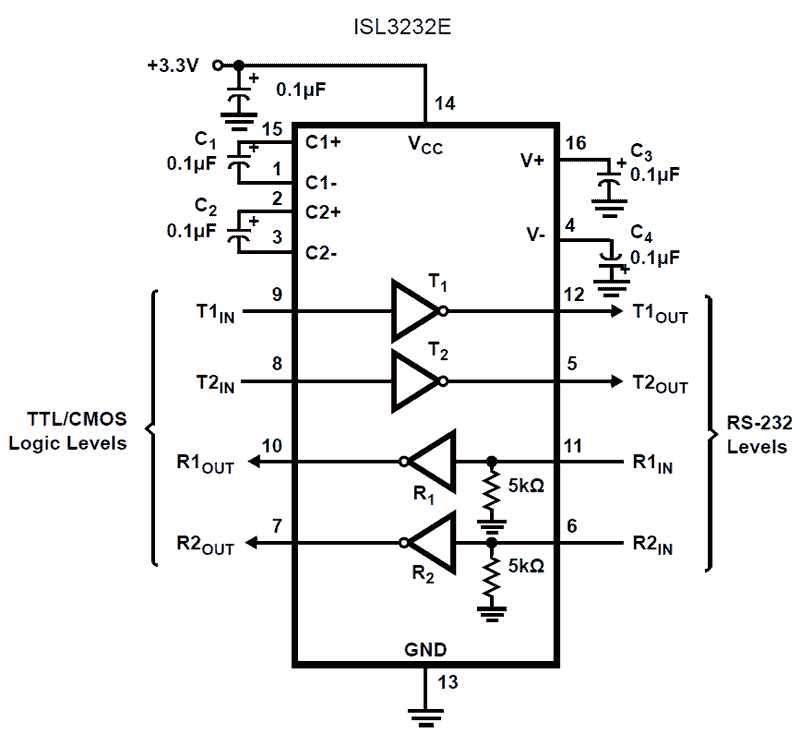
In the ever-evolving landscape of digital connectivity, ensuring the integrity and confidentiality of your network is paramount. This section delves into advanced security measures designed to fortify your network against emerging threats and vulnerabilities, bolstering its resilience in the face of adversarial challenges.
The Imperative of Vigilance
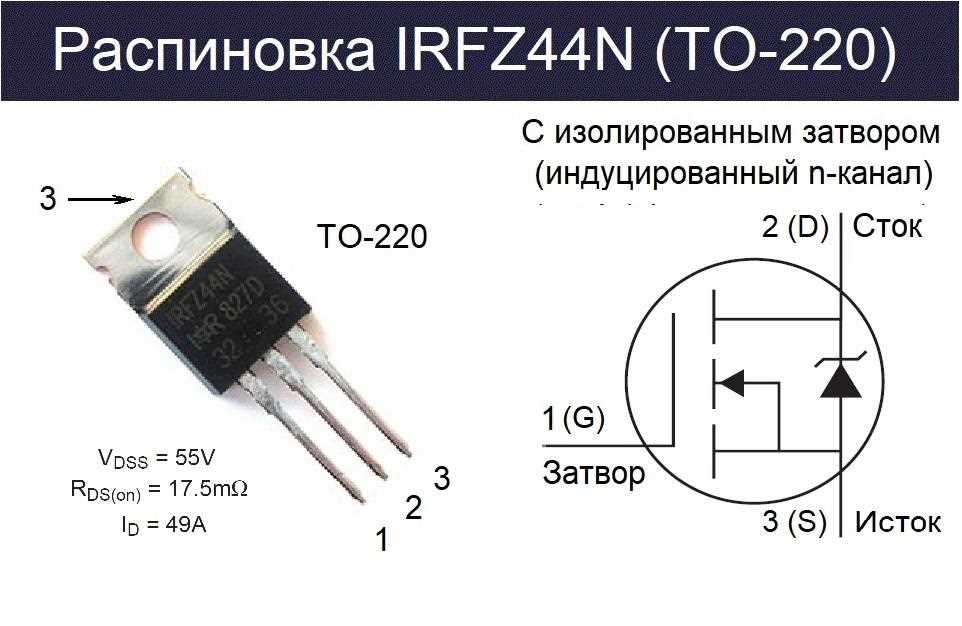
Effective network security demands a proactive stance, where preemptive measures are continuously implemented and refined to mitigate risks. Vigilance, therefore, becomes the cornerstone of safeguarding your network, necessitating constant monitoring, analysis, and adaptation to counteract evolving threats.
Strategic Layers of Defense

- Encryption Protocols: Implementing robust encryption protocols serves as a fundamental safeguard, shielding sensitive data from unauthorized access and interception.
- Firewall Configuration: Configuring firewalls with meticulous attention to detail establishes a barrier between your network and external entities, regulating incoming and outgoing traffic to thwart malicious intrusions.
- Multi-Factor Authentication: Embracing multi-factor authentication adds an additional layer of security, requiring users to authenticate their identity through multiple means, thereby fortifying access controls.
- Regular Audits and Assessments: Conducting regular audits and assessments enables the identification of vulnerabilities and gaps in security posture, facilitating proactive remediation and optimization.
- Threat Intelligence Integration: Integrating threat intelligence feeds empowers your network defenses with real-time insights into emerging threats and attack vectors, enabling swift and informed responses.
By incorporating these strategic layers of defense into your network architecture, you establish a resilient security framework capable of adapting to the dynamic threat landscape, safeguarding your digital assets and preserving the integrity of your operations.