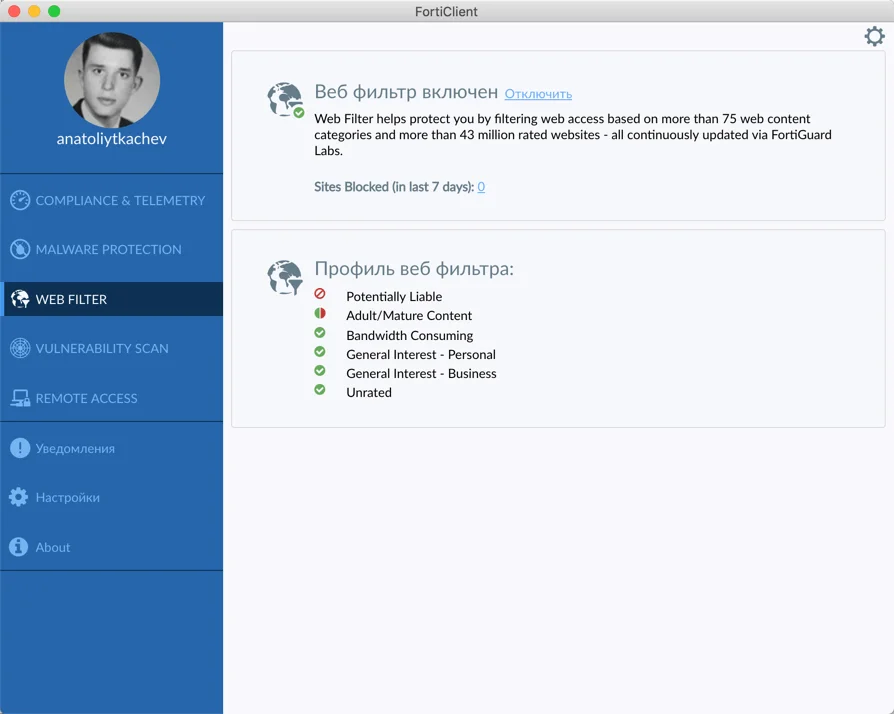
Explore the dynamic landscape of modern cybersecurity tools, where robust defenses and seamless user experiences converge. Dive into the realm of comprehensive security suites, where safeguarding digital assets merges with enhancing operational efficiency. Discover a versatile ally in the realm of network protection, seamlessly bridging the gap between threat detection and user accessibility.
Within this realm lies a powerful entity, a cornerstone of contemporary cybersecurity strategies. It stands as a bastion against digital threats, a sentinel guarding the virtual gates with unwavering vigilance. This entity, with its myriad features and functionalities, serves as a shield against the ever-evolving array of cyber adversaries.
Embark on a journey through the intricate web of network security with a companion forged in the fires of innovation. Experience the fusion of reliability and adaptability as you traverse the realms of threat mitigation and user empowerment. Together, let us uncover the essence of fortified defenses and seamless connectivity, encapsulated within the embodiment of technological prowess.
Understanding FortiClient Datasheets
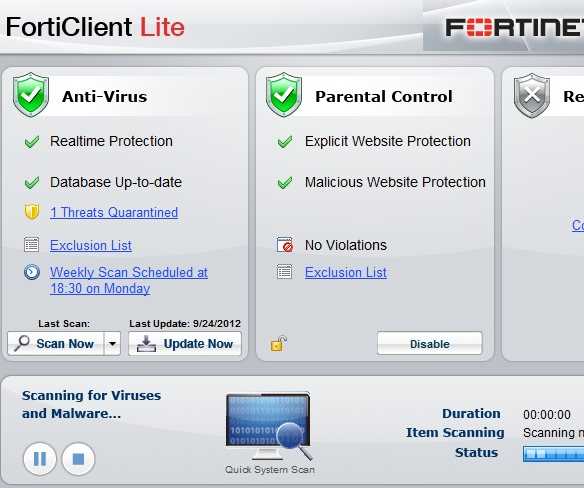
In the realm of cybersecurity solutions, comprehensive comprehension of product specifications is paramount. Within the realm of network security, FortiClient stands as a stalwart guardian, offering a myriad of features and functionalities tailored to fortify digital environments against threats. In this segment, we embark on a journey to delve into the intricacies of FortiClient datasheets, unraveling the wealth of information they encapsulate.
Deciphering Functionality
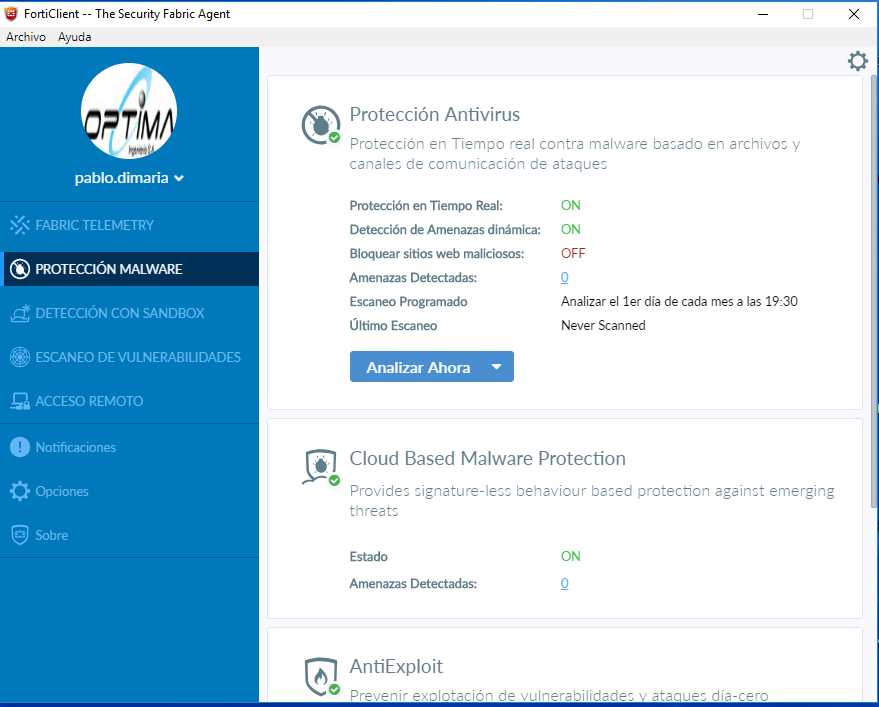
At the core of understanding FortiClient lies a meticulous examination of its capabilities. Synonymous with a blueprint, these datasheets delineate the array of tools and utilities inherent within FortiClient, each designed to bolster network defense. From threat detection mechanisms to endpoint management functionalities, every facet contributes to the holistic security posture.
Mapping Features to Requirements
Effectively harnessing FortiClient necessitates aligning its features with organizational security imperatives. Through perusal of the datasheets, stakeholders can discern how FortiClient addresses specific security challenges, thereby facilitating informed decision-making. Whether safeguarding against malware proliferation or enforcing compliance mandates, the datasheets serve as a compass guiding users towards optimal utilization.
| Feature | Description |
|---|---|
| Threat Detection | Identifies and mitigates a spectrum of cyber threats, including viruses, ransomware, and phishing attempts. |
| Endpoint Management | Facilitates centralized management of endpoint devices, enabling seamless enforcement of security policies. |
| VPN Integration | Integrates robust VPN functionalities, ensuring secure remote access to corporate networks. |
| Compliance Enforcement | Enforces regulatory compliance standards, such as GDPR and HIPAA, through granular policy enforcement. |
Deciphering Specifications of a Cybersecurity Solution
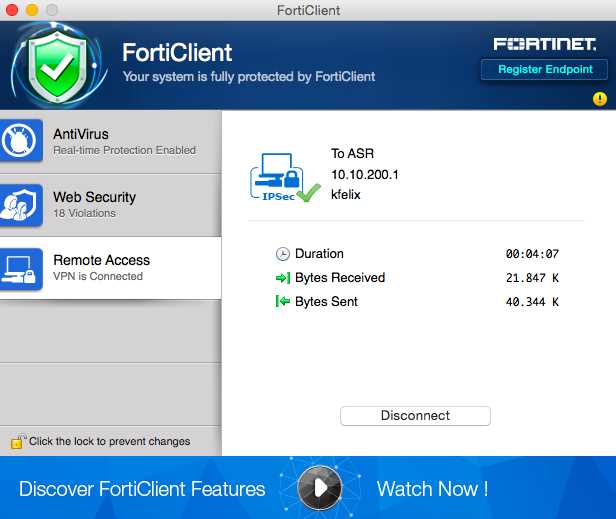
Understanding the intricate details and functionalities of a cybersecurity solution is paramount in today’s digital landscape. In this section, we embark on unraveling the specifications of a robust security tool, delving into its features, capabilities, and nuances.
Overview of Functionality

At the core of this security solution lies a myriad of features designed to fortify digital infrastructure against threats. Exploring its capabilities reveals a sophisticated arsenal tailored to address diverse cyber challenges.
- Security Protocols: Uncover the encryption algorithms and protocols employed to safeguard data transmission.
- Threat Detection Mechanisms: Explore the methods utilized for detecting and mitigating potential threats lurking in networks and endpoints.
- Endpoint Protection: Dive into the protective measures extended to individual devices, ensuring comprehensive security coverage.
Performance Metrics and Benchmarks
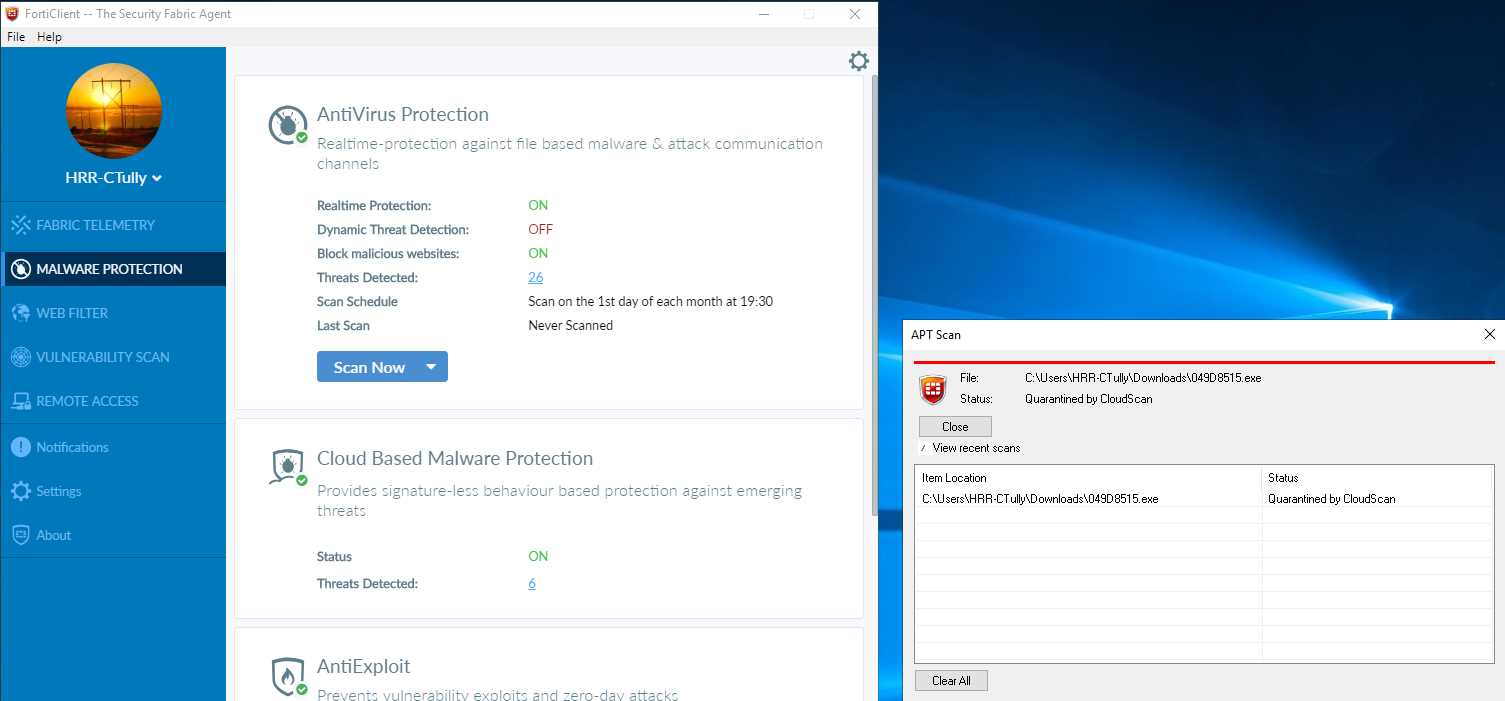
Assessing the efficacy of any cybersecurity solution necessitates a meticulous examination of its performance metrics and adherence to industry benchmarks. By scrutinizing these aspects, one gains insight into the solution’s efficacy and reliability in real-world scenarios.
- Throughput and Latency: Evaluate the solution’s ability to process data efficiently while minimizing latency, crucial for maintaining operational agility.
- Scalability: Analyze the solution’s scalability to accommodate evolving organizational needs and burgeoning digital ecosystems.
- Compliance Standards: Delve into its adherence to regulatory frameworks and industry standards, ensuring alignment with compliance mandates.
By deciphering the specifications of this cybersecurity solution, stakeholders can make informed decisions regarding its deployment and integration within their digital infrastructure.
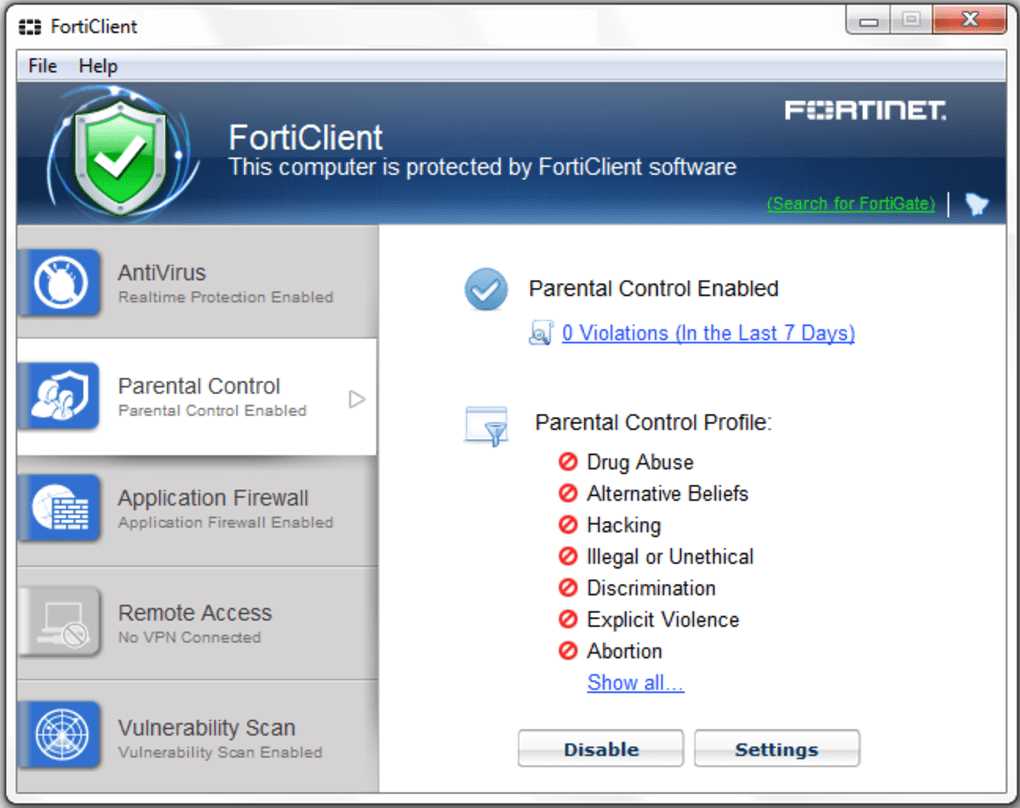
Key Features Highlighted in FortiClient Documentation
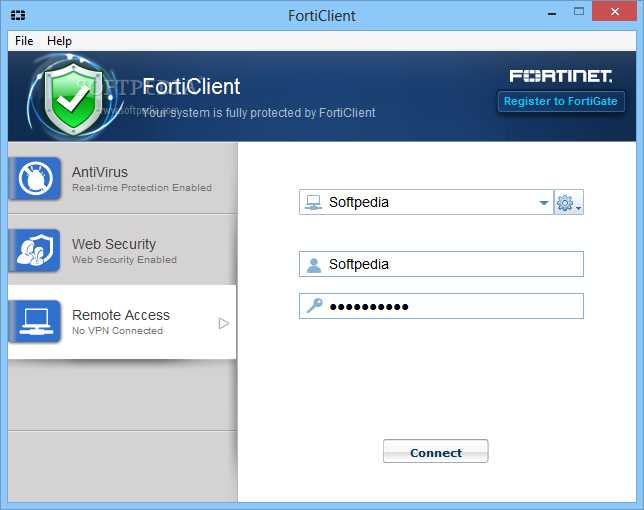
In this section, we will delve into the pivotal aspects showcased within the comprehensive documentation for FortiClient. It encapsulates the essence of FortiClient’s capabilities, providing users with an insightful overview of its functionalities and utilities. Let’s explore the fundamental attributes that set FortiClient apart, offering a glimpse into its diverse array of features.
1. Enhanced Security Measures: FortiClient embodies a robust suite of security protocols, bolstering protection against a myriad of cyber threats. Its arsenal encompasses advanced encryption techniques, intrusion detection systems, and proactive threat intelligence mechanisms, ensuring a fortified defense posture for users.
2. Seamless Integration and Compatibility: FortiClient seamlessly integrates with various network architectures and operating systems, fostering interoperability across heterogeneous environments. Whether deployed within enterprise networks or individual devices, FortiClient harmonizes effortlessly, optimizing efficiency and scalability.
3. Intuitive User Interface: FortiClient prides itself on an intuitive user interface, facilitating user interaction and navigation with unparalleled ease. From novice users to seasoned administrators, FortiClient offers a streamlined experience, enhancing productivity and user satisfaction.
4. Comprehensive Endpoint Management: FortiClient extends beyond conventional security paradigms, encompassing comprehensive endpoint management functionalities. It empowers administrators with granular control over endpoint devices, encompassing configuration management, software deployment, and remote troubleshooting.
5. Proactive Threat Prevention: FortiClient adopts a proactive approach towards threat prevention, preemptively mitigating emerging threats before they manifest into full-fledged breaches. Through dynamic threat intelligence and behavioral analysis, FortiClient augments threat detection capabilities, safeguarding against evolving cyber threats.
6. Centralized Management and Reporting: FortiClient streamlines administrative tasks through centralized management and reporting capabilities. Administrators gain real-time visibility into network activities, enabling informed decision-making and rapid incident response.
7. Scalability and Performance Optimization: FortiClient caters to diverse organizational needs, offering scalability and performance optimization features. Whether deployed within small-scale enterprises or multinational corporations, FortiClient adapts seamlessly, ensuring consistent performance and reliability.
8. Continuous Innovation and Updates: FortiClient remains at the forefront of cybersecurity innovation, perpetually evolving to counter emerging threats and challenges. With regular updates and feature enhancements, FortiClient exemplifies a commitment to excellence, safeguarding users against the ever-changing threat landscape.
By encapsulating these key features within its documentation, FortiClient empowers users with a holistic understanding of its capabilities, fostering confidence in its efficacy as a formidable cybersecurity solution.
Interpreting Technical Details for Seamless FortiClient Deployment
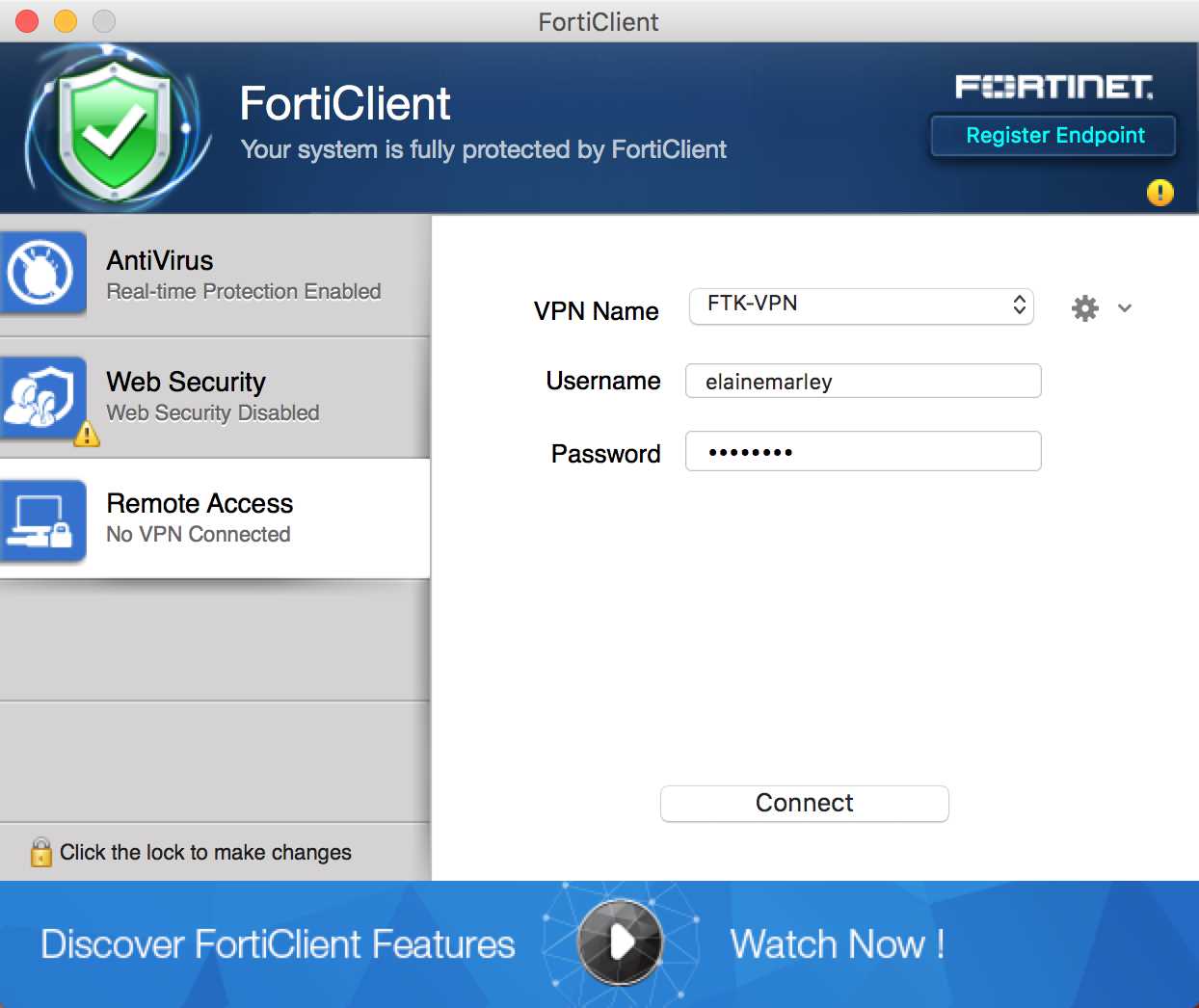
In this section, we delve into deciphering the intricate technical specifications essential for the successful integration and deployment of the FortiClient solution. Understanding the nuanced intricacies of these specifications lays the groundwork for a streamlined and efficient implementation process.
- System Requirements: Explore the prerequisites and compatibility criteria necessary for FortiClient deployment across diverse network infrastructures.
- Deployment Modes: Uncover the various deployment modes available with FortiClient, each tailored to suit specific network architectures and security postures.
- Configuration Options: Navigate through the plethora of configuration options offered by FortiClient, empowering administrators to customize settings according to organizational requirements.
- Security Protocols: Gain insights into the encryption standards and security protocols supported by FortiClient, ensuring robust protection of sensitive data during transit.
- Performance Metrics: Examine the performance metrics provided by FortiClient, facilitating the optimization of network resources and enhancing overall operational efficiency.
By comprehensively interpreting these technical details, stakeholders can make informed decisions regarding FortiClient deployment strategies, fostering a secure and resilient network environment.