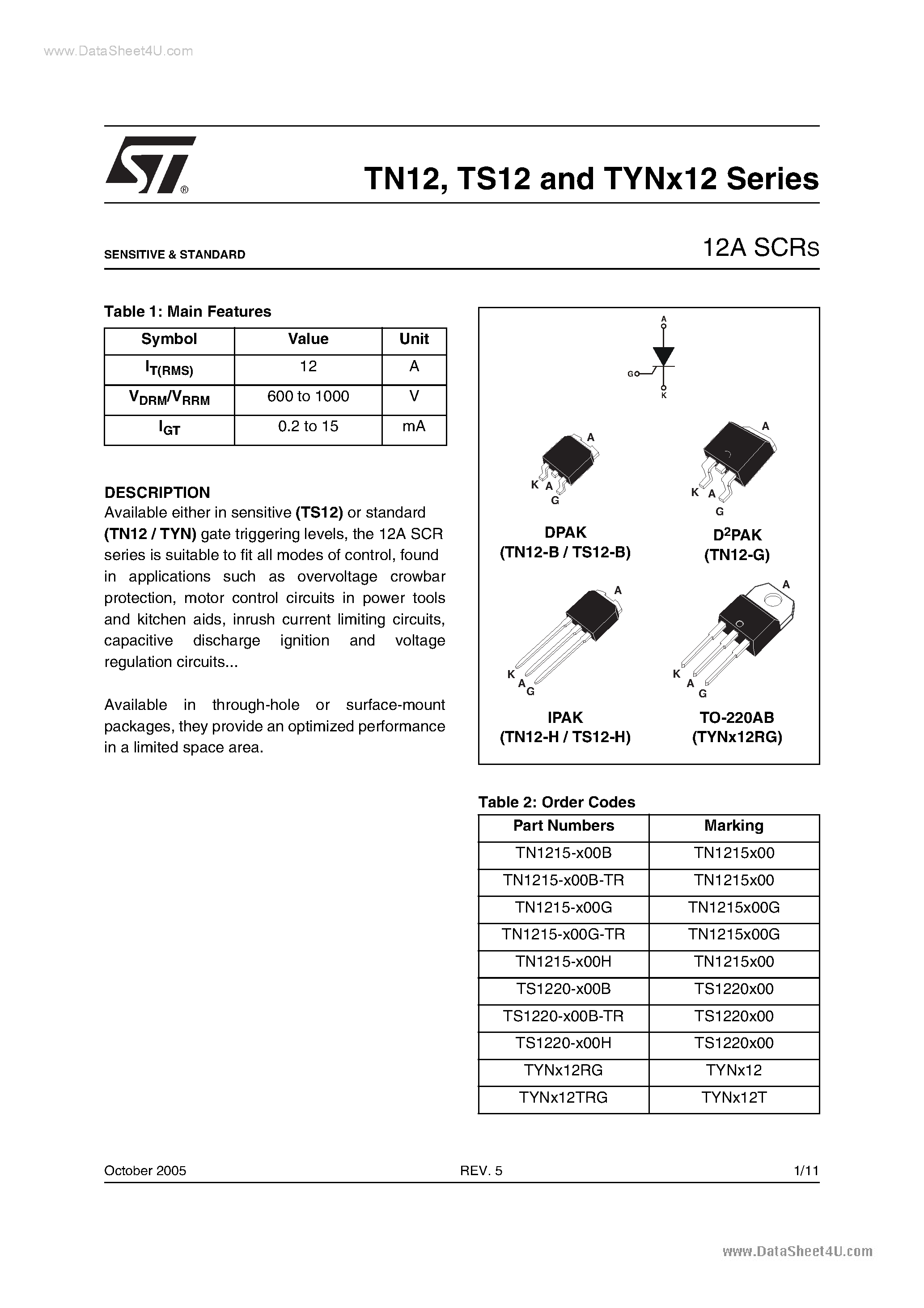
Shielding sensitive information is paramount in today’s digital landscape, where privacy breaches and cybersecurity threats loom large. In the pursuit of fortifying confidential data, a meticulous understanding of robust protective measures becomes indispensable. This discourse delves into an innovative solution designed to fortify your data assets and erect formidable barriers against potential vulnerabilities.
Within the realm of information security, the pursuit of enhanced safeguarding mechanisms takes precedence. As organizations navigate the labyrinth of digital transformation, they encounter a myriad of challenges, chief among them being the preservation of data integrity and confidentiality. In response to these imperatives, cutting-edge technologies emerge, promising unparalleled defensive capabilities against evolving threats.
Amidst this landscape, the quest for a standardized framework to guide data protection initiatives assumes significance. Beyond mere compliance requirements, such a framework serves as a compass, directing organizations towards comprehensive security strategies that transcend the boundaries of conventional approaches. It is within this context that the exploration of MVision Protect Standard unveils a tapestry of innovative methodologies tailored to safeguard your digital assets with precision and efficacy.
Mvision Protect Standard Datasheet Overview
In this section, we provide a comprehensive insight into the core components and functionalities encompassed within the documentation under review. Delving into the intricate framework of this dossier, we embark upon elucidating the fundamental features and operational dynamics, thereby offering a panoramic view of its overarching objectives and strategic significance.
| Section | Content |
|---|---|
| Introduction | Embark upon |
| Key Elements | Essential constituents |
| Functionalities | Operational dynamics |
| Significance | Strategic importance |
As we navigate through this dossier overview, emphasis is placed on illuminating the essence of its contents, without delving into specific terminologies. Through a meticulous exploration of its thematic underpinnings, readers are guided towards a profound understanding of the document’s relevance and implications within its respective domain.
Key Features and Benefits
In this section, we delve into the distinguishing characteristics and advantages offered by the Mvision Protect Standard Datasheet, elucidating its core functionalities and the positive impacts it brings to users.
Comprehensive Security Suite
Experience a robust array of security measures encompassing various layers of protection, ensuring holistic defense against diverse threats and vulnerabilities.
Streamlined User Interface
Enjoy an intuitive and user-friendly interface designed to enhance usability and facilitate seamless navigation, empowering users to efficiently manage their security protocols with ease.
Understanding Mvision Protect Standard Capabilities

In this section, we delve into the core functionalities inherent within Mvision Protect Standard, elucidating its diverse array of features and functionalities. Through a comprehensive exploration, we aim to provide a nuanced understanding of the capabilities encapsulated within this innovative solution.
The Essence of Mvision Protect Standard
At its essence, Mvision Protect Standard embodies a multifaceted approach towards safeguarding critical data assets and fortifying organizational resilience. It operates on a foundation of advanced methodologies and robust mechanisms, ensuring comprehensive protection across various digital domains.
Unveiling the Operational Dynamics
Within the operational framework of Mvision Protect Standard lie intricate algorithms and sophisticated protocols designed to detect, mitigate, and mitigate potential threats. Through a harmonious integration of proactive and reactive strategies, it orchestrates a seamless defense mechanism, thereby fostering a secure computing environment conducive to sustained productivity and growth.
Data Loss Prevention and Encryption
In the realm of safeguarding sensitive information and preserving the integrity of data, the principles of data loss prevention and encryption stand as paramount. This section delves into the methodologies and technologies employed to mitigate the risks associated with unauthorized access, inadvertent leaks, or malicious exploitation of confidential data. Through a combination of proactive measures and robust encryption techniques, organizations strive to fortify their digital assets against potential threats and breaches.
|
Data Loss Prevention Efforts aimed at preventing the unauthorized disclosure or leakage of sensitive information constitute the essence of data loss prevention strategies. By implementing a comprehensive framework encompassing policies, procedures, and technological solutions, organizations endeavor to proactively identify, monitor, and mitigate the risk of data breaches. This entails the deployment of advanced monitoring tools, access controls, and behavior analytics to detect and respond to anomalous activities that may indicate potential data exfiltration. |
Encryption Techniques Encryption serves as a cornerstone in the defense against data breaches by rendering intercepted information indecipherable to unauthorized parties. Through the utilization of cryptographic algorithms, plaintext data is transformed into ciphertext, thereby obscuring its meaning and ensuring confidentiality during transmission or storage. Modern encryption techniques encompass a variety of methodologies, including symmetric and asymmetric encryption, hashing, and digital signatures, each tailored to address specific security requirements and operational constraints. |
Threat Detection and Response
In the realm of safeguarding your digital assets, the prowess to discern and counteract potential dangers serves as an indispensable shield. Within this domain lies the quintessential essence of identifying looming hazards and swiftly orchestrating a strategic riposte. It encompasses a symphony of methods ranging from early warning signals to decisive countermeasures, all orchestrated to uphold the sanctity of your digital ecosystem.
Vigilance and Proactivity: In the ever-evolving landscape of digital security, remaining vigilant stands as the cornerstone of effective defense. Through the lens of proactive surveillance, anomalies are scrutinized with precision, enabling preemptive measures to be deployed before threats materialize into tangible risks.
Analytical Prowess: Beyond mere observation lies the analytical acumen to discern patterns amidst the noise. By harnessing the power of data analytics and machine learning, latent threats are unveiled, allowing for a proactive stance against potential breaches.
Response Orchestration: The efficacy of threat detection finds its zenith in the swift orchestration of response protocols. Through a seamless integration of automated triggers and human intervention, the response mechanism springs into action, mitigating threats with precision and alacrity.
Continuous Evolution: In the perpetual arms race against malicious actors, stagnation equates to vulnerability. Thus, the ethos of threat detection and response hinges upon a culture of perpetual evolution, wherein insights gleaned from past encounters pave the path for fortified defenses against future incursions.
Embracing the artistry of threat detection and response, one cultivates not merely a shield, but a bastion against the ever-prowling specter of digital peril.