Embark on a journey to explore the intricacies and capabilities of a cutting-edge network security solution, a technological marvel that promises to redefine your digital fortification strategy. Delve into the depths of a comprehensive document detailing the features and functionalities of a versatile guardian for your data highways. This discourse serves as a guide, offering insights into the prowess of a stalwart protector, ensuring the integrity and resilience of your network infrastructure.
Discover the inner workings of this formidable shield, meticulously crafted to thwart the myriad threats lurking in the digital realm. Within these pages lie the blueprints of innovation, elucidating the mechanisms that empower your network to withstand the onslaught of cyber adversaries. Unravel the mysteries of a solution engineered to fortify your digital perimeter, safeguarding against breaches and vulnerabilities with unparalleled efficacy.
Unveil the dimensions of security, where robustness meets sophistication, encapsulated in a comprehensive compendium that elucidates the prowess of your guardian in the realm of network defense. Traverse through the realms of functionality and performance, as each facet is meticulously outlined, offering a panoramic view of the capabilities that underpin your digital fortress. Prepare to embark on a voyage of discovery, where each specification unveils a new layer of resilience and protection, empowering you to navigate the complexities of the digital landscape with confidence.
Understanding Fortigate 60F: A Comprehensive Overview

Embark on a journey of comprehension through the intricate workings and features of this advanced network security solution. Delve into the depths of its capabilities, exploring its robust functionalities and innovative design. Discover how the Fortigate 60F stands as a stalwart guardian against modern digital threats, offering unparalleled defense mechanisms and seamless integration.
Within the realm of network security, the Fortigate 60F emerges as a beacon of reliability and sophistication. Its array of features encompasses a broad spectrum of defensive mechanisms, meticulously crafted to safeguard networks from diverse cyber threats. As we navigate through its components and functionalities, a nuanced understanding of its inner workings will unfold, revealing the essence of its effectiveness.
- Explore the foundational architecture that forms the backbone of the Fortigate 60F, laying the groundwork for its formidable defense mechanisms.
- Uncover the intricacies of its threat detection capabilities, ranging from signature-based detection to advanced behavioral analytics, ensuring comprehensive protection against evolving threats.
- Delve into the realm of secure connectivity, where the Fortigate 60F excels in facilitating seamless communication while maintaining stringent security protocols.
- Ascertain the significance of its intuitive management interface, simplifying administrative tasks and empowering users with unparalleled control over their network security infrastructure.
- Examine the scalability and flexibility inherent in the Fortigate 60F, adapting seamlessly to the evolving needs of organizations and networks of varying sizes.
By dissecting the core components and functionalities of the Fortigate 60F, we gain a holistic understanding of its role in fortifying network defenses. Through this comprehensive overview, we embark on a journey to decipher the essence of its efficacy and resilience in the face of modern cyber threats.
Exploring the Key Features and Capabilities
In this section, we delve into the essential attributes and functionalities of the system, unveiling its core strengths and diverse capabilities. Let’s embark on a journey to uncover the myriad facets that distinguish this solution, offering a comprehensive understanding of its potential.
Beginning with its foundational elements, we examine the fundamental pillars that underpin its operation. From robust security protocols to advanced networking capabilities, each aspect contributes to a holistic framework designed to fortify digital environments.
Moreover, we explore the innovative features engineered to enhance operational efficiency and streamline management processes. These include intuitive interfaces, dynamic analytics tools, and adaptive mechanisms that adapt to evolving threats and organizational needs.
Beyond conventional functions, this system boasts a repertoire of specialized tools tailored to address specific challenges and industry requirements. From compliance frameworks to tailored threat intelligence, it empowers users with tailored solutions for varied contexts.
Lastly, we delve into the scalability and flexibility inherent in its design, facilitating seamless integration with existing infrastructures and accommodating future growth. This adaptability ensures longevity and resilience in the face of dynamic landscapes and evolving demands.
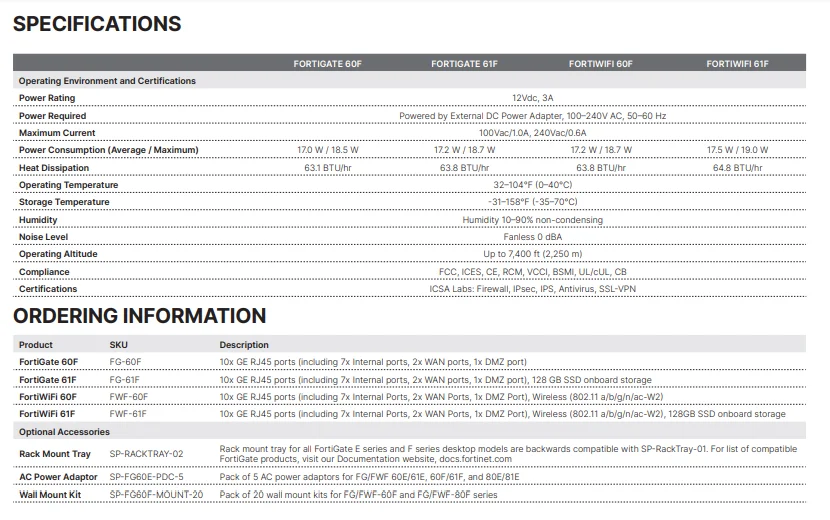
Deciphering the Technical Specifications of the Fortigate 60F

In this segment, we delve into the intricate details underlying the technological prowess of the Fortigate 60F, shedding light on its capabilities and functionalities. We navigate through the labyrinth of technical specifications, offering clarity and understanding without relying on the jargon commonly associated with such documentation.
Performance Metrics Unveiled

- Throughput metrics
- Processing speeds
- Efficiency benchmarks
Embark on a journey through the performance metrics of the device, uncovering its ability to handle diverse workloads seamlessly. Explore the intricacies of throughput, processing speeds, and efficiency benchmarks, gaining insight into its operational capabilities.
Connectivity and Networking Capabilities Explored

- Networking interfaces
- Protocol support
- Security protocols
Delve into the realm of connectivity and networking, where the device showcases its prowess in facilitating seamless communication and robust security protocols. Discover the array of networking interfaces, delve into the supported protocols, and unravel the layers of security measures embedded within.
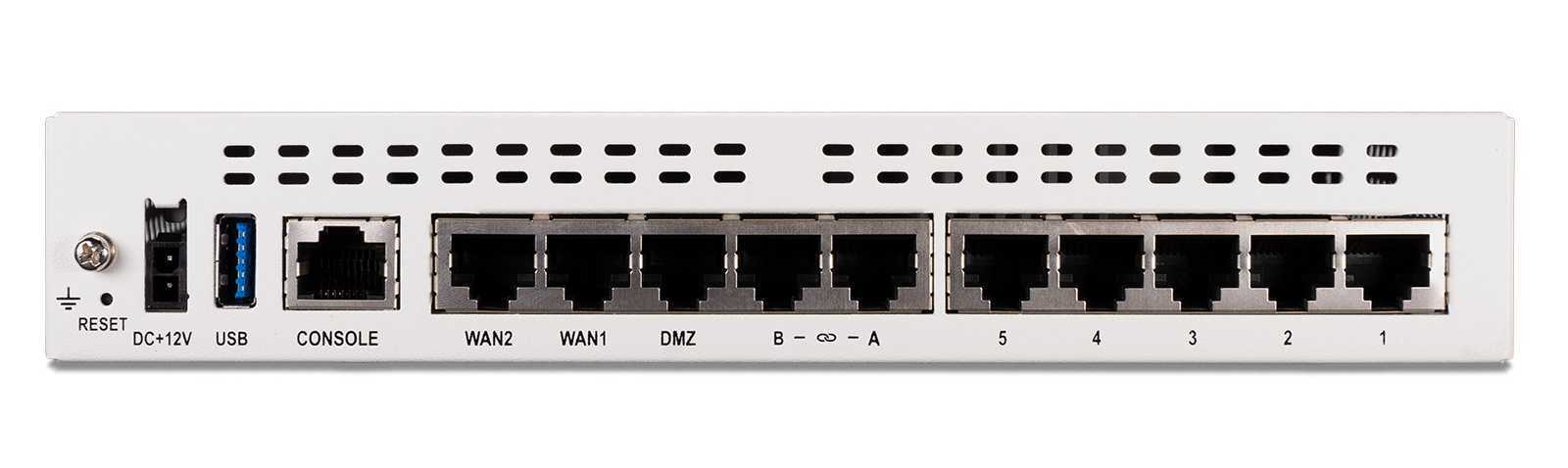
Hardware and Software Components Unveiled

In this section, we delve into the intricate architecture of the device, exploring its internal mechanisms and operational framework. Through an examination of both its physical and virtual elements, we uncover the foundational building blocks that empower its functionality and performance.
Hardware Overview

At the heart of this system lies a sophisticated array of tangible components, meticulously engineered to seamlessly integrate and execute tasks with precision. From the robust processing units to the intricate circuitry, each element plays a pivotal role in driving the device’s capabilities forward.
- The Central Processing Unit (CPU): Serving as the brain of the operation, the CPU orchestrates intricate computations and commands, facilitating swift decision-making and response times.
- Memory Modules: These vital components store and retrieve data at remarkable speeds, ensuring seamless access to critical information for efficient operation.
- Networking Interfaces: Facilitating seamless connectivity, the networking interfaces enable data transmission and reception, fostering communication between various components within the system and beyond.
- Storage Units: Housing essential software components and configuration data, the storage units provide a repository for system resources, enabling persistent access to crucial information.
Software Infrastructure
Beyond its physical composition, the device boasts a sophisticated software ecosystem, comprising intricately crafted algorithms and protocols designed to optimize performance and enhance security. Through a combination of proprietary software solutions and industry-standard protocols, the device ensures robust defense mechanisms and efficient resource utilization.
- Operating System: The underlying operating system provides a stable foundation for executing tasks and managing system resources, ensuring seamless operation and reliability.
- Security Protocols: Leveraging advanced encryption algorithms and authentication mechanisms, the device fortifies network defenses, safeguarding against potential threats and vulnerabilities.
- Management Interfaces: Intuitive management interfaces empower administrators to configure, monitor, and troubleshoot the device effortlessly, enhancing operational efficiency and responsiveness.
- Application Layer Services: Through a suite of application layer services, the device facilitates seamless integration with existing infrastructures and workflows, enabling streamlined communication and data exchange.
By unraveling the intricate interplay between its hardware and software components, this section illuminates the inner workings of the device, offering insights into its operational prowess and adaptability.
Enhancing Network Security with Fortigate 60F: Practical Insights
Discover how to bolster your network’s security infrastructure through advanced strategies and practical techniques with the Fortigate 60F. In this section, we delve into actionable insights to fortify your digital perimeter, safeguard sensitive data, and mitigate emerging cyber threats. Explore innovative approaches to network defense, optimize security configurations, and stay ahead of potential vulnerabilities.
- Implementing Robust Firewall Policies: Learn how to craft tailored firewall policies to regulate inbound and outbound traffic effectively, ensuring comprehensive protection against unauthorized access and malicious activities.
- Strengthening Intrusion Prevention Systems (IPS): Explore methods to enhance IPS capabilities, including signature-based detection, anomaly-based detection, and protocol analysis, to proactively identify and block potential intrusions.
- Securing Remote Access: Discover best practices for securing remote access to your network infrastructure, including VPN configuration, multi-factor authentication (MFA), and endpoint security measures, to safeguard against external threats.
- Optimizing Threat Intelligence Integration: Leverage threat intelligence feeds and integrate them seamlessly into your security infrastructure to enhance threat detection, response, and mitigation capabilities, empowering proactive defense against evolving threats.
- Ensuring Secure Web Gateway: Explore techniques to establish a secure web gateway using URL filtering, content inspection, and application control, enabling granular control over web traffic and preventing access to malicious websites and content.
By applying these practical insights and leveraging the capabilities of the Fortigate 60F, you can elevate your network security posture, mitigate risks, and foster a resilient defense against today’s dynamic threat landscape.