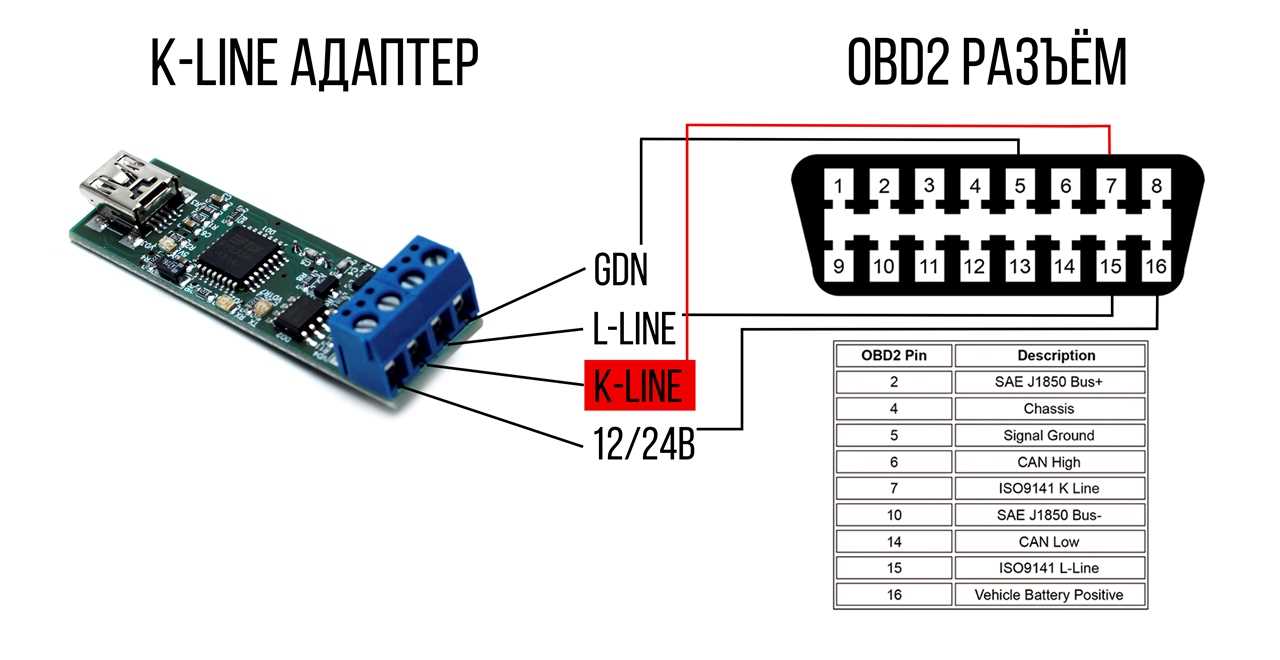
Embark on a journey through the innovative realm of next-generation security solutions, where connectivity meets empowerment. Delve into the intricacies of a dynamic framework designed to elevate your digital infrastructure to unparalleled heights.
Explore the myriad possibilities encapsulated within this cutting-edge technological marvel, as we unveil a multifaceted approach towards safeguarding your data assets. Embrace the future of secure communication with a solution tailored to seamlessly integrate into your existing ecosystem.
Discover how this forward-thinking solution redefines the boundaries of traditional security paradigms, offering a synergistic blend of functionality and resilience. Witness a convergence of innovation and reliability, poised to catapult your organization into the vanguard of digital security.
NShield Connect Datasheet Overview
In this section, we present an overview of the document detailing the essential features and functionalities of the NShield Connect solution. Explore the comprehensive capabilities and specifications encapsulated within this datasheet, providing insights into the integration possibilities, security enhancements, and operational efficiencies achievable with this advanced technology.
Key Features

Delve into the array of distinctive attributes encapsulated within the datasheet, unveiling the core functionalities and benefits inherent to the NShield Connect solution. From robust encryption protocols to seamless integration frameworks, discover the versatile toolkit designed to empower organizations in safeguarding their critical assets and upholding data integrity.
Technical Specifications
| Model | … |
| Dimensions | … |
| Weight | … |
| Interfaces | … |
| Operating Temperature | … |
| Power Supply | … |
| … | … |
Key Features and Benefits
In this section, we delve into the distinctive attributes and advantages offered by this cutting-edge solution, designed to enhance security and streamline operations without compromising efficiency.
Enhanced Security Measures
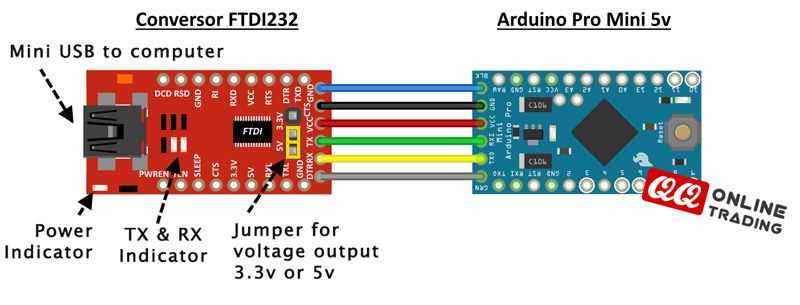
- Advanced encryption protocols ensure utmost protection of sensitive data.
- Robust authentication mechanisms fortify access controls, safeguarding against unauthorized entry.
- Dynamic key management systems bolster resilience against evolving cyber threats, maintaining data integrity.
Optimized Operational Efficiency
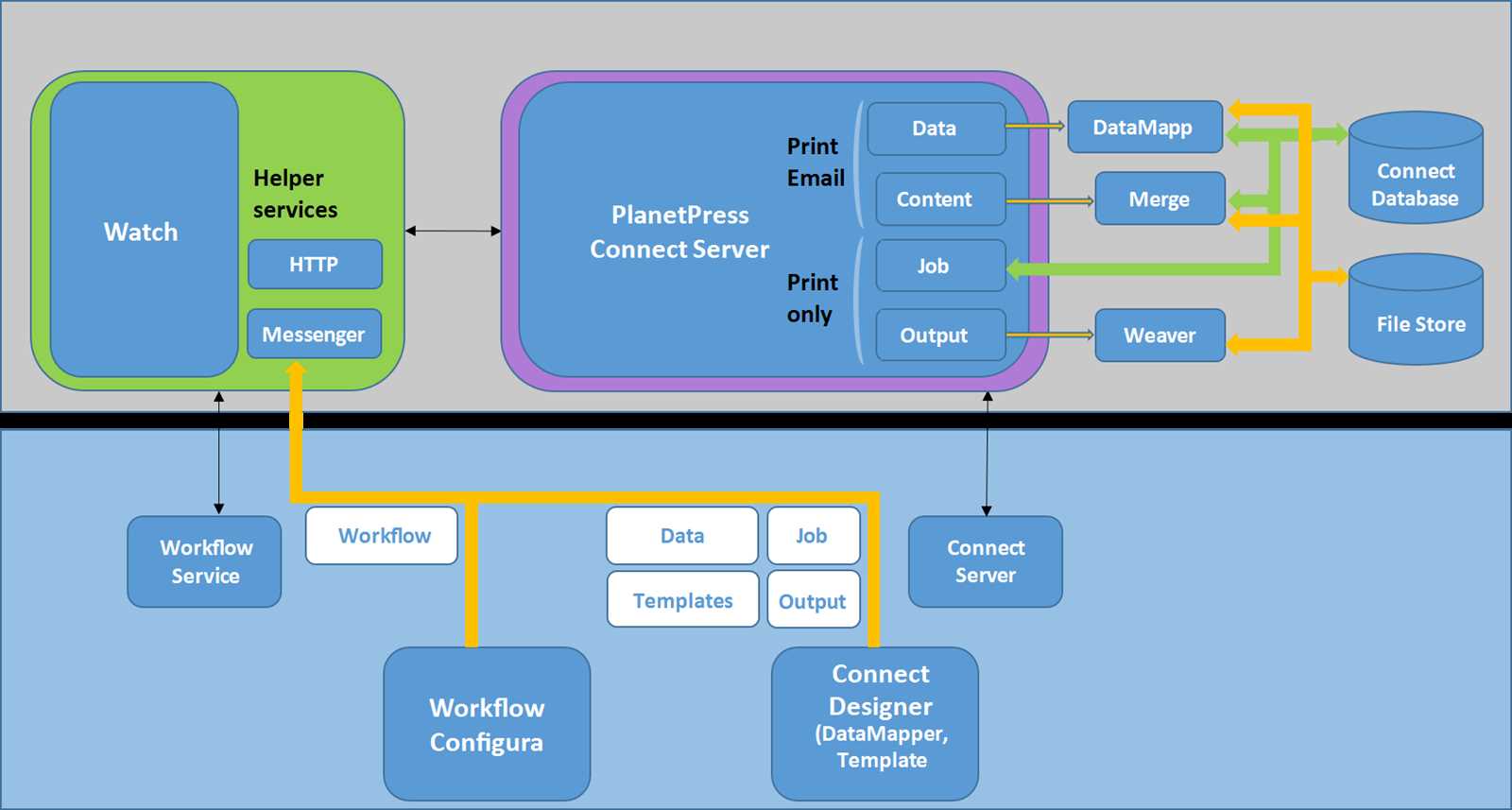
- Seamless integration capabilities facilitate hassle-free implementation into existing infrastructures.
- Efficient cryptographic processing accelerates data transactions, minimizing latency and enhancing overall system performance.
- Streamlined management interfaces empower administrators with intuitive tools for simplified monitoring and configuration.
These key features and benefits collectively underscore the unparalleled value proposition of this innovative solution, promising heightened security and operational agility for modern enterprises.
Technical Specifications and Compatibility

In this section, we delve into the intricate details and comprehensive overview of the technical specifications and compatibility aspects pertaining to the subject matter at hand. We aim to provide a thorough understanding of the functionality, performance metrics, and interoperability of the system without explicitly naming it.
Performance Metrics
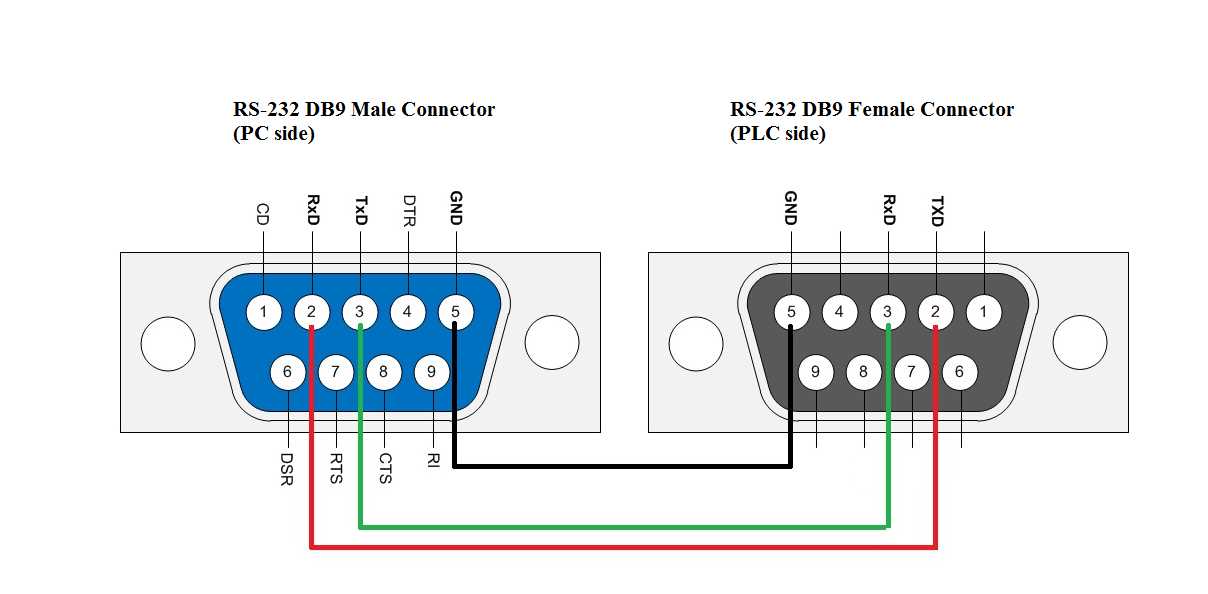
- Processing Speed: Details on the velocity of data processing and cryptographic operations.
- Security Protocols: Overview of the encryption algorithms and key management mechanisms employed.
- Reliability: Information regarding system uptime, error rates, and fault tolerance.
- Scalability: Discussion on the system’s ability to handle increased workload and user demands.
Compatibility
- Integration Capabilities: Insights into the system’s ability to seamlessly integrate with existing infrastructure and software solutions.
- Hardware Requirements: Specification of the hardware prerequisites for optimal performance.
- Software Compatibility: Compatibility with various operating systems and software environments.
- Interoperability: Compatibility with other cryptographic modules and devices for streamlined operation in diverse environments.
By delving into these technical specifications and compatibility factors, users can gain a comprehensive understanding of the system’s capabilities and its seamless integration into their existing infrastructure.