
In the realm of advanced cybersecurity technologies, there exists a formidable guardian, an embodiment of robust protection and unparalleled defense mechanisms. This guardian stands as a sentinel against the ever-evolving threats lurking in the digital landscape, ensuring the integrity and security of data flows within networks of all scales and complexities.
Embark on a journey into the realm of network fortification, where innovation meets necessity, and resilience intertwines with agility. Discover a solution engineered to safeguard against the myriad of cyber assailants, equipped with intricately woven layers of defense mechanisms designed to thwart intrusion attempts and mitigate risks.
Within this exploration lies an intricate blueprint, a testament to meticulous engineering and relentless dedication towards fortifying the digital infrastructure. Unveil the essence of this technological marvel, delving into its core functionalities and strategic capabilities that empower organizations to navigate the turbulent waters of cyberspace with confidence and assurance.
Join the quest to unravel the mysteries of this guardian of digital realms, as we navigate through the contours of its prowess and unveil the strategic advantages it bestows upon those who seek to fortify their networks against the adversarial forces that loom on the horizon.
The Power and Performance of Fortigate 2601f
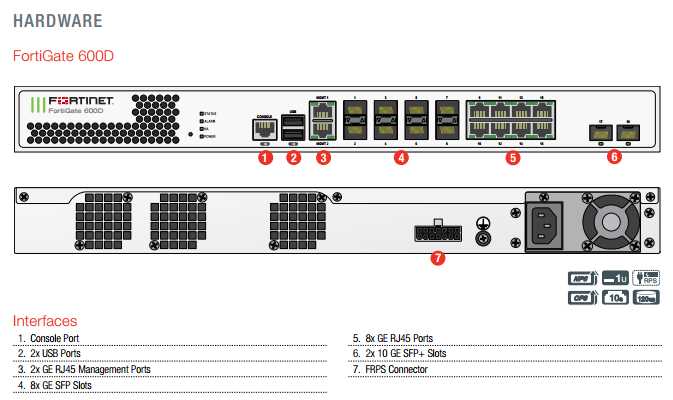
In this segment, we delve into the formidable capabilities and impressive operational prowess encapsulated within the latest iteration of Fortigate, denoted as 2601f. Our focus lies in dissecting the sheer efficiency, robust functionality, and the dynamic potentiality inherent within this cutting-edge network security appliance.
Embark on a journey through the technological marvel that is the Fortigate 2601f, as we explore its ability to seamlessly navigate the intricate labyrinth of modern digital landscapes, safeguarding networks with unparalleled precision and efficacy. Discover how this device epitomizes the convergence of power and agility, offering a symbiotic blend of advanced features meticulously crafted to address the evolving challenges of cybersecurity.
Unveil the sheer force of performance as the Fortigate 2601f emerges as a stalwart guardian, equipped with a repertoire of mechanisms to thwart even the most sophisticated cyber threats. Witness the intricate dance of computational prowess and strategic intelligence, harmonized within a singular entity to fortify networks against intrusions and vulnerabilities.
Experience the epitome of reliability as the Fortigate 2601f stands as a beacon of resilience amidst the tumultuous seas of digital warfare. Delve into its capacity to uphold the integrity of data flows, ensuring seamless operations while maintaining an unwavering commitment to security standards.
Embrace the future of network defense as we unravel the intricacies of the Fortigate 2601f, a testament to innovation and excellence in the realm of cybersecurity. Prepare to embark on a transformative journey, where power meets performance, and security transcends expectation.
Unlocking the Potential of Next-Generation Firewall Technology
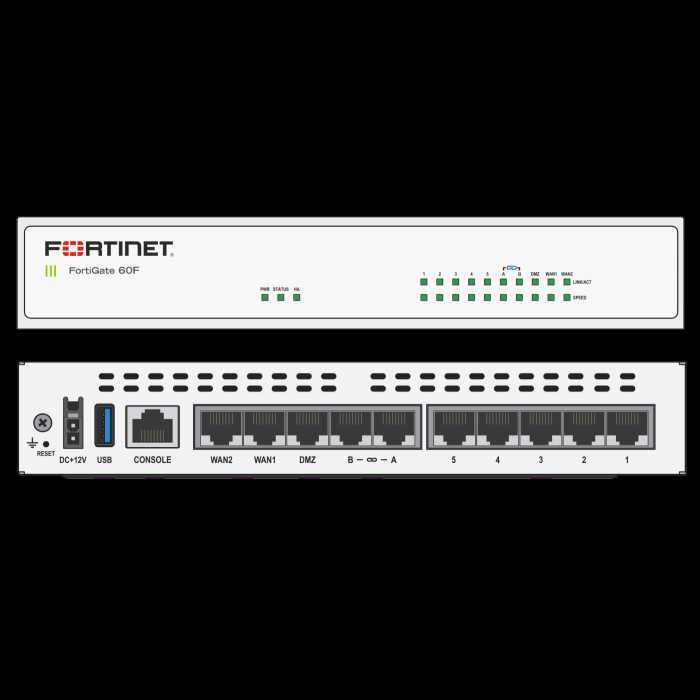
Embracing the cutting-edge capabilities inherent in modern firewall solutions heralds a new era of cyber defense. This section delves into the transformative power of advanced firewall technologies, propelling organizations towards fortified security and streamlined network management.
The Evolution of Cyber Threats
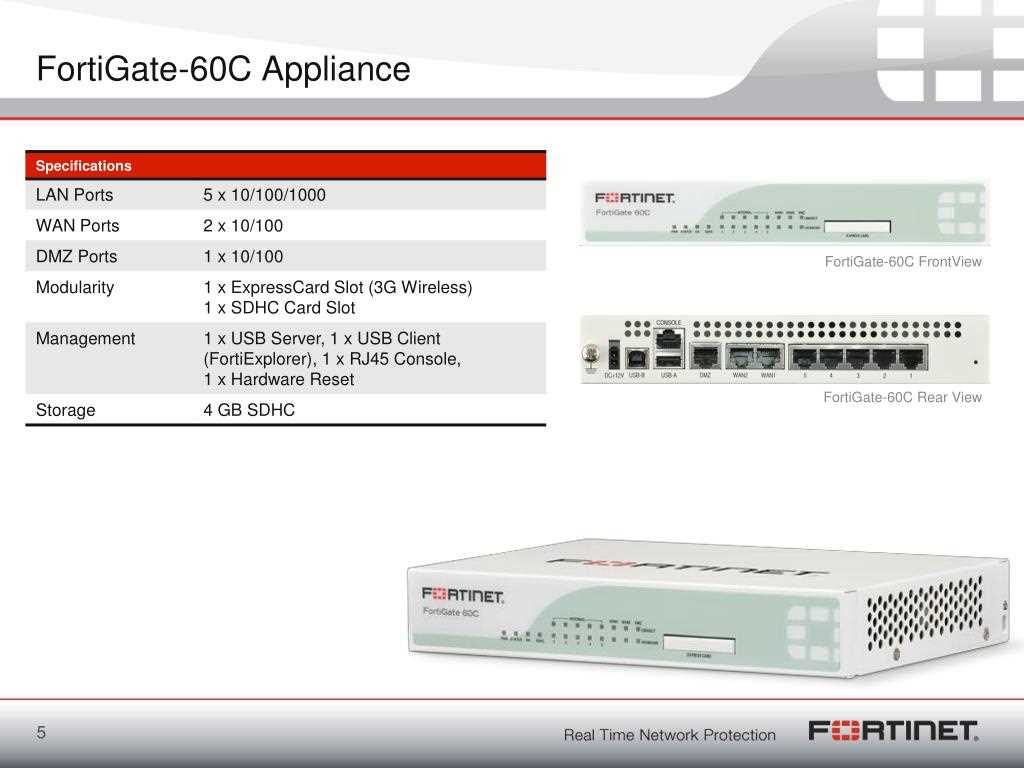
In today’s digital landscape, the panorama of cyber threats is as diverse as it is relentless. From sophisticated malware to targeted cyber-attacks, organizations face an ever-growing array of challenges to their digital assets and operations. Traditional security measures, while once effective, now struggle to keep pace with the evolving tactics of malicious actors.
Empowering Security Infrastructure
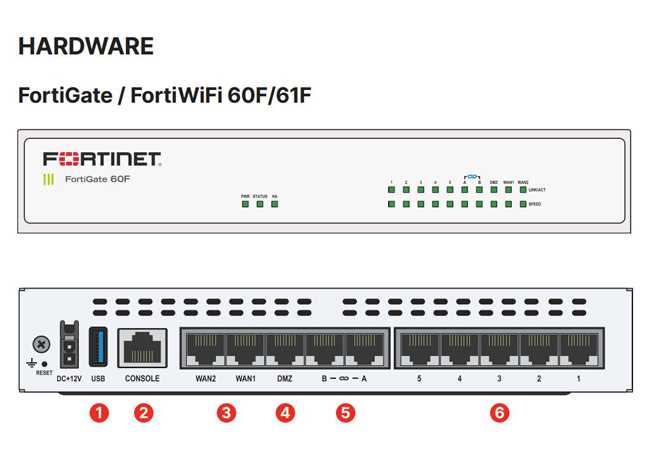
Next-generation firewall technology stands as a beacon of hope amidst this tumultuous cyber terrain. By amalgamating robust intrusion prevention systems, deep packet inspection, and advanced threat intelligence, these innovative solutions fortify networks against a spectrum of threats. They empower organizations to proactively detect and mitigate potential breaches, safeguarding critical data and preserving operational continuity.
Through the lens of next-generation firewall technology, organizations can transcend the limitations of conventional security paradigms. By harnessing the synergy of intelligent automation, real-time threat analysis, and adaptive security policies, they can forge a formidable defense against the ever-evolving threat landscape.
Securing Networks with Advanced Firewall Solutions
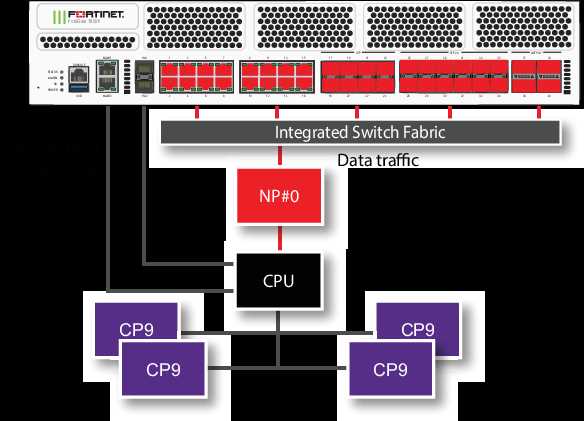
When it comes to safeguarding your network infrastructure, robust and reliable firewall solutions play a paramount role in ensuring comprehensive security. In this section, we delve into the strategies and features essential for fortifying your network against a myriad of cyber threats.
Enhanced Threat Detection and Prevention: A crucial aspect of network security lies in the ability to detect and thwart malicious activities effectively. With cutting-edge threat detection mechanisms, our firewall solution empowers you to identify and neutralize potential threats before they can exploit vulnerabilities within your network.
Dynamic Traffic Filtering: Ensuring the integrity of your network traffic is imperative in mitigating risks associated with unauthorized access and data breaches. Our firewall solution offers dynamic traffic filtering capabilities, allowing you to define granular policies to regulate the flow of data and enforce access controls with precision.
Advanced Encryption Protocols: In an era characterized by pervasive connectivity, safeguarding sensitive information transmitted across networks is paramount. Our firewall solution integrates advanced encryption protocols to ensure the confidentiality and integrity of data in transit, thwarting eavesdropping attempts and safeguarding against unauthorized interception.
Comprehensive Logging and Reporting: Maintaining visibility into network activities is essential for proactive threat management and compliance adherence. With comprehensive logging and reporting functionalities, our firewall solution enables you to monitor and analyze network traffic patterns, identify anomalies, and generate detailed reports for audit purposes.
Scalable and Flexible Deployment: Adaptability and scalability are indispensable traits in modern network security solutions. Our firewall solution offers flexible deployment options, catering to diverse organizational requirements and infrastructural architectures. Whether deployed as a standalone appliance or integrated into a comprehensive security framework, it ensures seamless interoperability and optimal performance.
Continuous Updates and Support: The threat landscape is constantly evolving, necessitating proactive measures to stay abreast of emerging security challenges. With regular updates and dedicated support services, our firewall solution ensures that your network remains resilient against evolving threats, providing peace of mind and enabling you to focus on core business objectives.
In conclusion, securing your network infrastructure requires a multifaceted approach encompassing proactive threat detection, stringent access controls, robust encryption, and comprehensive monitoring capabilities. Our advanced firewall solution offers a holistic framework for fortifying your network against a myriad of cyber threats, empowering you to safeguard your critical assets and uphold the integrity of your digital ecosystem.
Exploring Advanced Features and Capabilities for a Resilient Cybersecurity Arsenal

In this section, we delve into the intricacies of cutting-edge functionalities and the expansive potentialities inherent in modern cybersecurity solutions. Our exploration transcends the conventional boundaries, venturing into the realm of sophisticated tools and techniques aimed at fortifying digital fortresses against relentless cyber threats.
- Dynamic Threat Intelligence Integration: Seamlessly incorporating real-time threat intelligence feeds empowers your defense mechanism with up-to-the-minute insights into emerging cyber threats and trends, fostering proactive defense strategies.
- Behavioral Analytics: Leveraging advanced behavioral analytics algorithms enables the detection of anomalous activities and suspicious patterns, allowing for swift identification and mitigation of potential security breaches.
- Adaptive Access Control: Implementing adaptive access control mechanisms ensures granular control over user privileges and access rights, dynamically adjusting permissions based on contextual factors such as device posture, user behavior, and threat intelligence.
- Threat Hunting Capabilities: Equipping your cybersecurity arsenal with robust threat hunting capabilities empowers security teams to proactively seek out and neutralize latent threats lurking within the network, minimizing the dwell time of adversaries.
- Deception Technologies: Deploying sophisticated deception technologies introduces decoy assets and honey traps into the network environment, deceiving and deterring adversaries while providing valuable insights into their tactics, techniques, and procedures.
By embracing these advanced features and capabilities, organizations can construct a resilient cybersecurity infrastructure capable of effectively mitigating a diverse array of cyber threats, safeguarding critical assets, and preserving operational continuity in the face of adversity.
Enhancing Connectivity with Advanced Network Solutions

In the realm of modern networking, optimizing connectivity stands as a pivotal pillar for seamless operations. This section delves into the strategies and solutions that empower businesses to fortify their network infrastructure, ensuring robust and reliable connections.
At the core of bolstering connectivity lies the implementation of cutting-edge technologies designed to streamline data transmission and enhance network performance. By leveraging innovative solutions, organizations can foster a dynamic environment where communication flows effortlessly and productivity thrives.
Furthermore, the quest for enhanced connectivity entails a comprehensive approach that encompasses both hardware and software elements. From optimizing routing protocols to deploying intelligent traffic management systems, every facet plays a crucial role in creating a cohesive network ecosystem.
Moreover, in an era marked by the proliferation of digital interactions, the demand for secure and scalable connectivity solutions has never been more pronounced. Through the adoption of advanced encryption protocols and stringent access controls, businesses can safeguard their data while facilitating seamless connectivity across diverse environments.
Ultimately, the pursuit of enhanced connectivity with next-generation network solutions transcends mere technological advancement. It embodies a commitment to empowering organizations with the agility and resilience needed to navigate the complexities of the digital landscape.