
Discover the next generation of cutting-edge security technology, designed to fortify your digital infrastructure and safeguard your data against evolving threats. Dive into the intricate details of a formidable shield, meticulously engineered to uphold the integrity of your network and ensure uninterrupted operations.
Unravel the intricacies of a formidable sentinel, meticulously crafted to stand as a bastion against modern cyber adversaries. Delve into the depths of innovative defenses, meticulously engineered to preserve the sanctity of your digital realm amidst an ever-changing threat landscape.
Embark on a journey through the annals of digital protection, where every line of code serves as a fortress, and every algorithm a guardian of your virtual domain. Let us navigate through the labyrinth of advanced security paradigms, where resilience meets sophistication, and where trust is not just earned but fortified.
Understanding the Performance Metrics of Checkpoint 7000 Datasheet
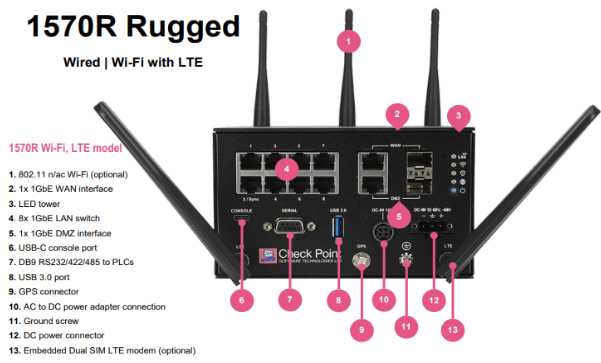
In delving into the intricacies of evaluating the prowess of the Checkpoint 7000, it becomes imperative to dissect its performance metrics comprehensively. This section aims to dissect and decipher the various indicators that illuminate the operational efficiency and capabilities of this cutting-edge apparatus.
Performance Parameters:
Embark on a journey through the labyrinth of performance parameters that underpin the operational fortitude of the system. From throughput and latency to packet processing capabilities, each facet unveils a unique facet of its operational prowess.
Throughput Unveiled:
Dive into the heart of throughput metrics to uncover the system’s ability to handle data transmission and reception with finesse. Through meticulous analysis of its throughput capacities across diverse scenarios, a nuanced understanding of its operational capabilities emerges.
Latency Exploration:
Embark on an exploration of latency, delving into the realm of response times and data transfer delays. Unravel the nuances of latency metrics to glean insights into the system’s responsiveness and efficiency under varying workloads.
Packet Processing Proficiency:
Examine the system’s packet processing prowess, deciphering its ability to handle and maneuver data packets with agility and precision. Uncover the intricacies of packet processing metrics to ascertain the system’s efficiency in managing network traffic.
Scalability Insights:
Peer into the realm of scalability to grasp the system’s capacity for expansion and growth. Through an analysis of scalability metrics, discern the system’s ability to adapt to evolving demands and accommodate burgeoning workloads with seamless efficacy.
By delving into these performance metrics with a discerning eye, a comprehensive understanding of the operational dynamics of the Checkpoint 7000 unfolds, paving the path for informed decision-making and optimized utilization.
Exploring Throughput, Latency, and Packet Processing Capabilities
In this section, we delve into the intricacies of network performance metrics, encompassing the efficiency and speed at which data traverses the network, the time it takes for data to travel from source to destination, and the ability of the system to handle and manipulate data packets.
Understanding Throughput

Throughput, often referred to as data transfer rate, signifies the volume of data that successfully passes through a network or system within a specified time frame. It encapsulates the system’s capacity for data transmission, reflecting its ability to sustain a consistent flow of information without congestion or bottlenecks. Throughput is a fundamental measure of network efficiency, influenced by various factors such as bandwidth, latency, and packet loss.
Examining Latency and Packet Processing
Latency, the time delay between the initiation of a data transfer and its completion, plays a critical role in determining the responsiveness and perceived speed of network operations. Low latency is essential for real-time applications and interactive communication, while high latency can introduce delays and hinder user experience.
Packet processing capabilities encompass the system’s ability to efficiently handle incoming and outgoing data packets, including tasks such as inspection, forwarding, and filtering. This capability directly impacts the network’s performance, security, and scalability, influencing factors like throughput, latency, and overall user experience.
Security Highlights in the Latest Product Overview

In this section, we delve into the robust security features showcased within the latest presentation of our cutting-edge technology. Explore the forefront of security advancements and discover the layers of protection integrated into our state-of-the-art solution.
| Advanced Threat Prevention | Unveil a comprehensive shield against evolving threats with advanced threat prevention mechanisms. |
| Intelligent Intrusion Detection | Experience real-time detection of unauthorized access attempts through intelligent intrusion detection systems. |
| Network Segmentation | Enhance security posture by implementing network segmentation strategies to isolate critical assets. |
| Encrypted Traffic Inspection | Ensure privacy without compromising security with robust encrypted traffic inspection capabilities. |
| Vulnerability Management | Stay ahead of potential vulnerabilities with proactive vulnerability management solutions. |
Embrace a holistic approach to security with a blend of proactive and reactive measures, designed to fortify your digital infrastructure against a myriad of cyber threats.
An In-depth Look into Threat Prevention, Encryption, and Access Control

Exploring the intricate dynamics of safeguarding digital environments entails a multifaceted approach encompassing three pivotal pillars: thwarting potential hazards, fortifying sensitive data through cryptographic measures, and orchestrating stringent mechanisms for regulating access. This segment delves into the nuanced interplay among threat mitigation strategies, encryption protocols, and access control mechanisms, elucidating their paramount significance in preserving the integrity and confidentiality of digital ecosystems.
Threat Prevention: Within the labyrinth of cyberspace, an array of pernicious threats lurk, incessantly probing vulnerabilities in the digital infrastructure. Effective threat prevention entails the deployment of proactive measures aimed at preempting and neutralizing potential hazards before they permeate the network perimeter. By discerning the modus operandi of contemporary threats and harnessing advanced detection algorithms, organizations can erect robust defenses to thwart intrusions and fortify their cyber fortress.
Encryption: In an era dominated by data proliferation, safeguarding sensitive information assumes paramount importance. Encryption, the bastion of data security, empowers organizations to obfuscate plaintext data into unintelligible ciphertext, impervious to unauthorized interception or exploitation. Through the judicious application of cryptographic algorithms, coupled with robust key management practices, organizations can erect formidable barriers to preserve the confidentiality and integrity of their digital assets.
Access Control: Governing the ingress and egress points of digital ecosystems necessitates a granular approach to access control. By delineating access privileges based on user roles, contextual attributes, and behavioral patterns, organizations can imbue their access control mechanisms with adaptive resilience. Through the orchestration of multifactor authentication protocols, role-based access controls, and continuous monitoring frameworks, organizations can fortify their defenses against unauthorized access attempts and uphold the sanctity of their digital domains.
Scalability and Deployment Options of Cutting-Edge 7000 Series Security Solutions
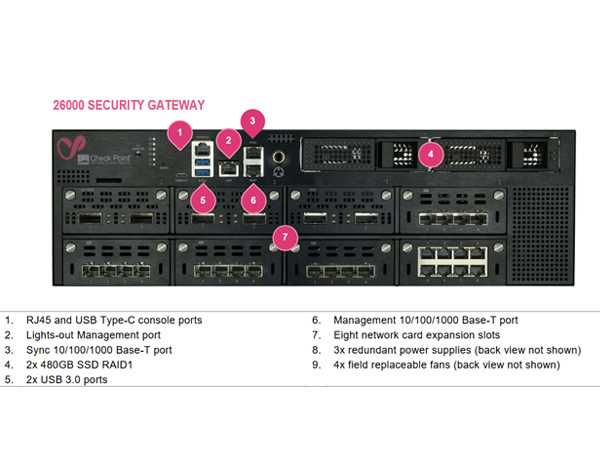
Empowering your network
Discover the seamless expansion potential and diverse deployment strategies inherent in the groundbreaking 7000 Series security solutions. Unveil the myriad ways these systems adapt and grow alongside your network’s evolving needs, providing unmatched flexibility and performance.
Exploring scalability
Dive into the realm of scalability as the 7000 Series effortlessly accommodates the burgeoning demands of modern networks. Witness how these solutions dynamically adjust to fluctuations in traffic volume and complexity, ensuring optimal operation even in the face of exponential growth.
Deployment versatility
Unleash the power of deployment versatility with the 7000 Series, offering a spectrum of options tailored to your organization’s unique infrastructure and operational requirements. From on-premises installations to cloud integration, explore the array of deployment models designed to suit diverse environments.
Optimizing performance
Unlock peak performance potential as the 7000 Series optimizes resource utilization and streamlines operational efficiency. Delve into the mechanisms driving enhanced throughput, low latency, and robust security, ensuring uncompromising protection without sacrificing speed or agility.
Future-proofing your security posture
Anticipate tomorrow’s challenges today with the future-proof design of the 7000 Series, engineered to evolve alongside emerging threats and technological advancements. Stay ahead of the curve as these solutions adapt, innovate, and redefine the boundaries of modern cybersecurity.