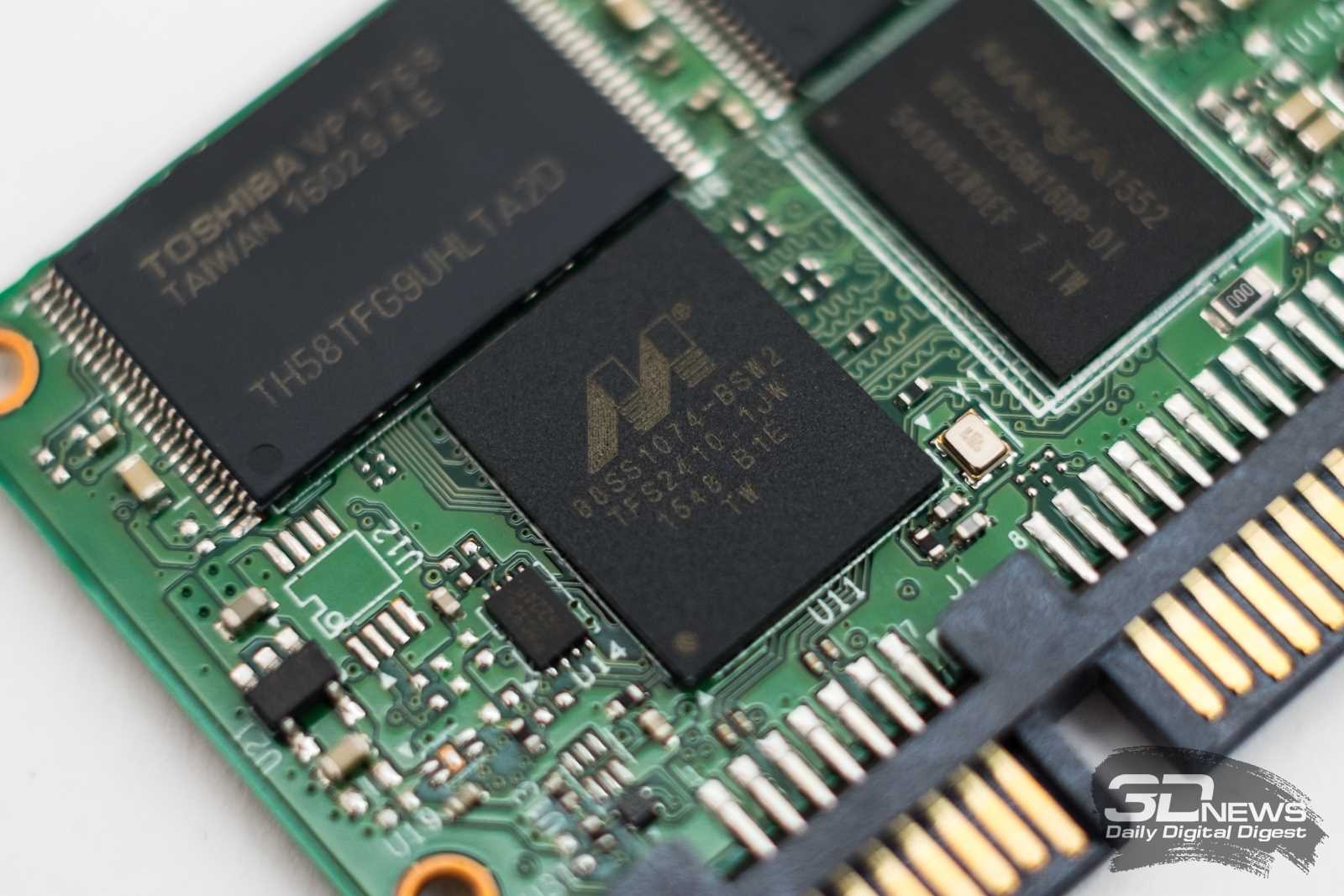
Unlocking the potential of contemporary innovation necessitates a comprehensive understanding of pivotal components driving modern devices. Delving into the intricacies of pivotal hardware, we embark on a journey to explore the heart of groundbreaking technology, where performance meets precision.
At the nexus of innovation lies a cornerstone element, orchestrating seamless functionality and optimal performance. Within the realm of technological advancement, unveiling the essence of this foundational component promises insights into the dynamic landscape of modern electronics.
Embarking on this intellectual voyage, we navigate through the realms of electronic architecture, dissecting the essence of its core. Through meticulous examination and insightful analysis, we illuminate the essence of this fundamental building block, deciphering its role in shaping the future of digital evolution.
Understanding the Key Components of the 88ss1074 Documentation
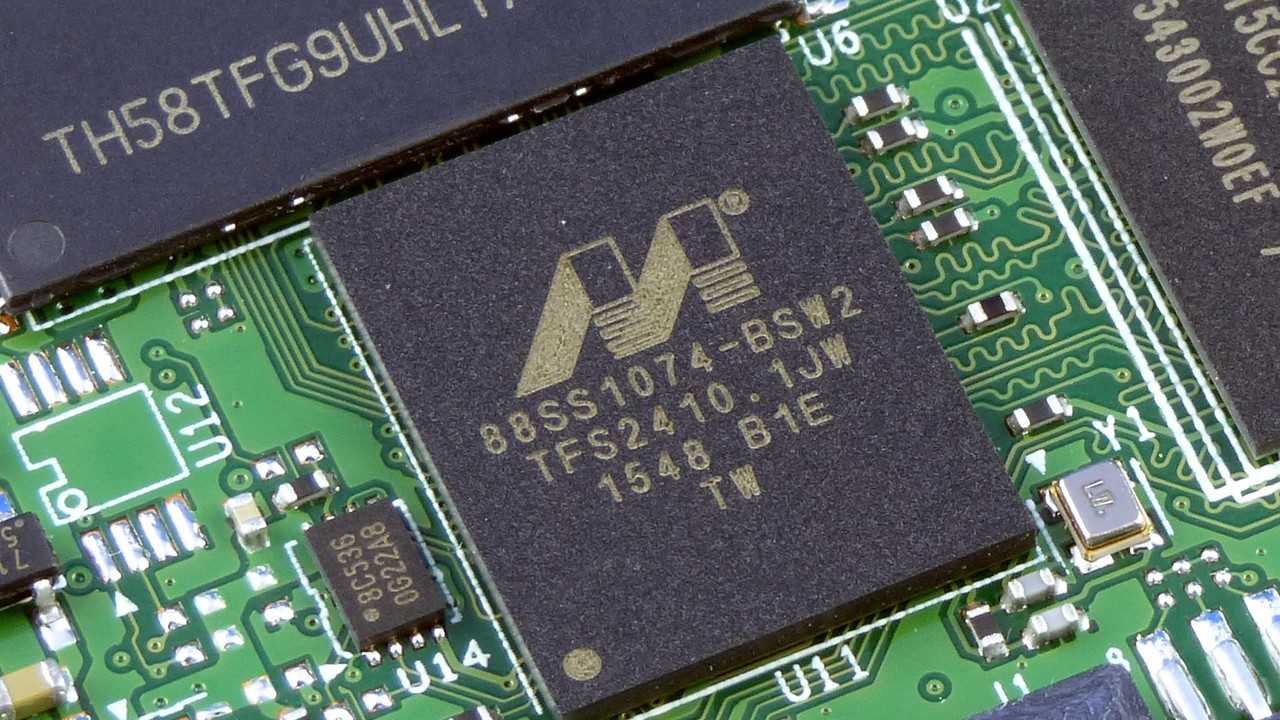
Delving into the intricacies of any hardware often begins with deciphering its documentation, a map revealing the architecture’s essential elements. In the case of the 88ss1074, an in-depth comprehension of its technical blueprint is indispensable for efficient integration and optimization.
Core Functional Blocks

At the heart of the documentation lie core functional blocks, each representing a vital aspect of the 88ss1074’s operation. Understanding these blocks is akin to unraveling the machinery’s inner workings, shedding light on its fundamental processes and interactions.
Signal Path Analysis

Examining the signal path within the documentation offers a glimpse into the flow of data and control signals, akin to understanding the neural pathways of a complex system. This analysis unveils the intricate dance of information, highlighting critical junctions and pathways crucial for seamless operation.
Exploring the Architecture and Functionality
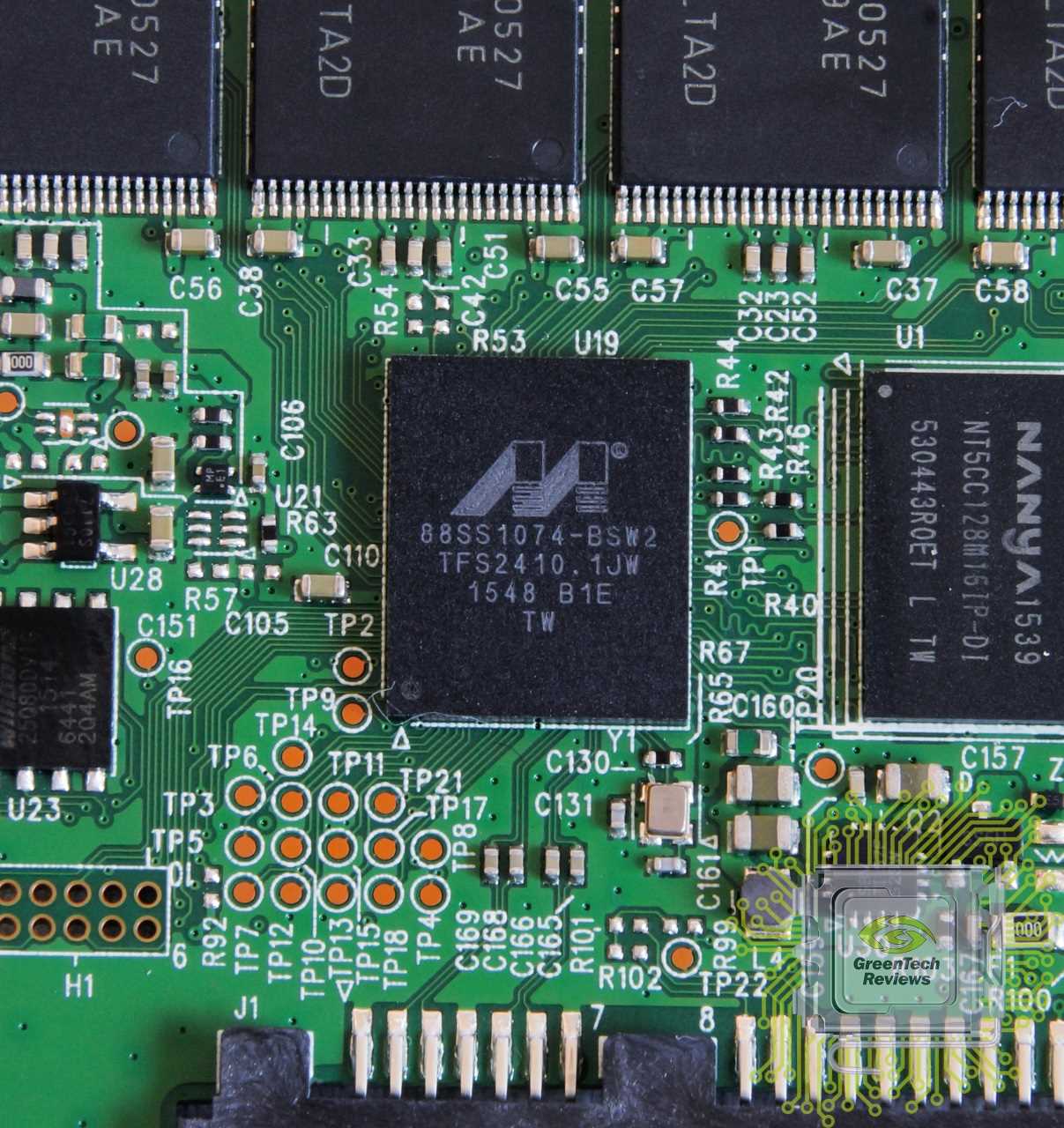
In this section, we delve into the intricate design and operational mechanisms of a cutting-edge semiconductor device, aiming to uncover its underlying structure and operational intricacies. Our exploration will traverse through the core components and operational modalities, shedding light on the intricate interplay of various elements that define its functionality.
- Core Structure Analysis
- Functional Framework Overview
- Operational Mechanisms Deconstruction
- Integration Insights
- Performance Metrics Evaluation
Embarking on this journey, we aim to provide a comprehensive understanding of the architecture and functionality of this innovative semiconductor component, enabling a deeper appreciation of its role and potential applications in contemporary technological landscapes.
Optimizing Performance: Tips and Tricks for Implementation of the 88ss1074 Chip

In this section, we delve into strategies and techniques aimed at enhancing the efficiency and effectiveness of your utilization of the cutting-edge 88ss1074 microcontroller. By implementing these insights, you can maximize the potential of your device, ensuring optimal performance and streamlined functionality.
Firstly, let’s explore methods for fine-tuning operational parameters to achieve peak efficiency. Adjusting configurations such as input/output rates, memory allocation, and task prioritization can significantly enhance the responsiveness and throughput of your system.
| Technique | Description |
|---|---|
| Algorithmic Optimization | Refining algorithms to minimize computational overhead and improve execution speed. |
| Resource Management | Optimizing resource utilization through efficient allocation and deallocation strategies. |
| Cache Utilization | Maximizing cache utilization to reduce memory latency and enhance data retrieval speed. |
| Power Management | Implementing power-saving techniques to prolong battery life and minimize energy consumption. |
Furthermore, adopting advanced debugging and profiling tools can facilitate comprehensive analysis of system performance, allowing for targeted optimizations and troubleshooting of potential bottlenecks.
Additionally, leveraging hardware acceleration features and integrating specialized co-processors can offload computational tasks from the main processor, thereby augmenting overall system performance while conserving valuable resources.
By incorporating these strategies into your implementation of the 88ss1074 chip, you can unlock its full potential and achieve superior performance across various applications and use cases.
Maximizing Efficiency and Reliability

In the pursuit of optimal performance and dependability, it’s imperative to explore strategies that enhance both efficiency and reliability in electronic systems. By employing methodologies aimed at streamlining operations and bolstering robustness, organizations can fortify their technology infrastructure to meet the demands of modern applications.
- Implementing streamlined processes and protocols can significantly enhance operational efficiency, ensuring smoother workflows and reduced downtimes.
- Adopting advanced reliability engineering techniques allows for the identification and mitigation of potential failure points, thereby enhancing the overall dependability of systems.
- Regular maintenance and proactive monitoring play pivotal roles in sustaining efficiency levels and preempting potential disruptions, thus bolstering system reliability.
- Investing in comprehensive training programs for personnel enables them to effectively utilize resources, minimizing inefficiencies and maximizing system uptime.
- Integration of cutting-edge diagnostic tools and predictive analytics facilitates early detection of anomalies, enabling timely interventions to prevent performance degradation.
By fostering a culture of continuous improvement and prioritizing investments in efficiency and reliability, organizations can lay a solid foundation for sustained success in the dynamic landscape of electronic systems.
Security Considerations in 88ss1074 Implementation Documentation
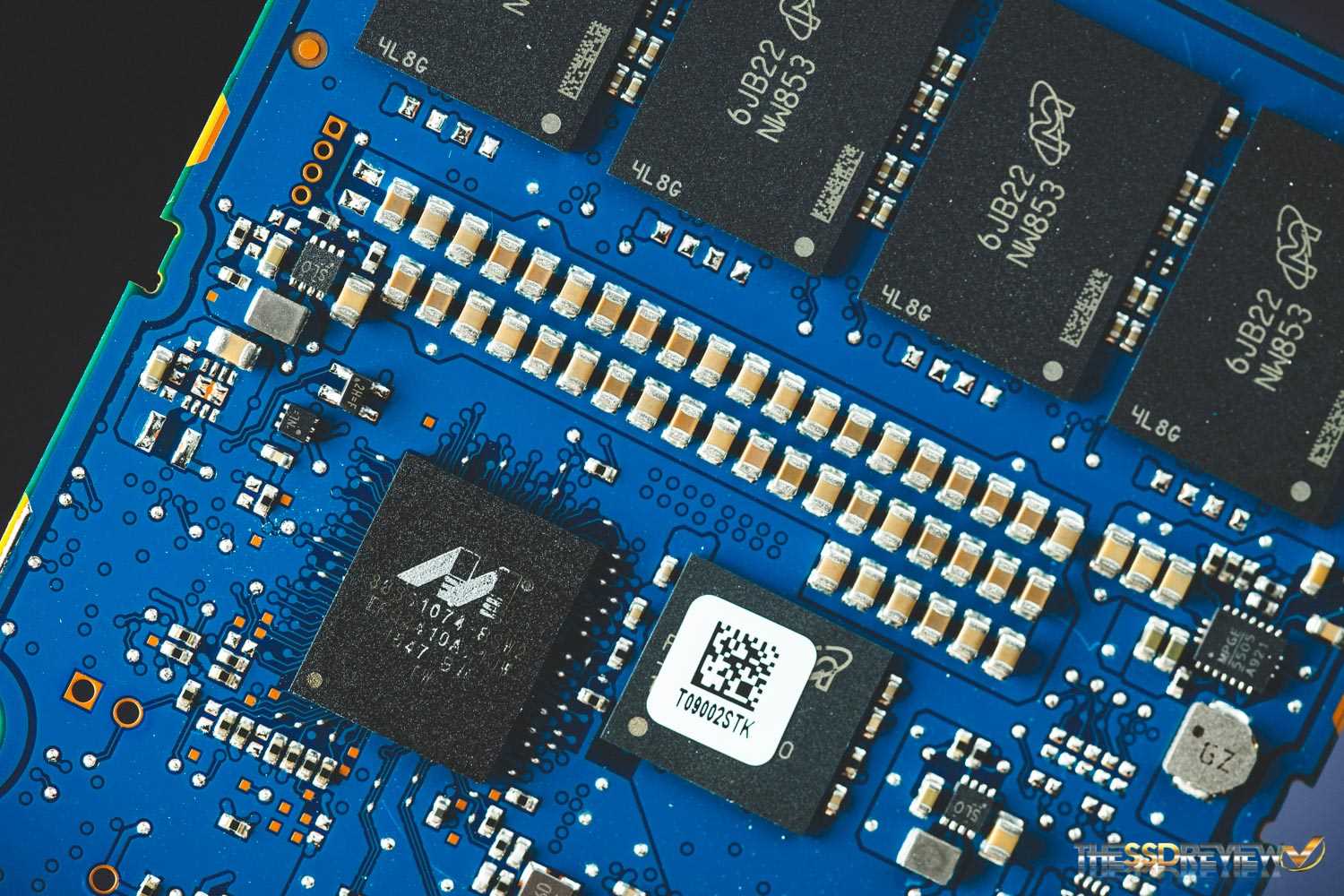
Exploring the intricacies of safeguarding sensitive information within the framework of 88ss1074 integration necessitates a meticulous examination of potential vulnerabilities and protective measures. This section delves into the essential aspects of fortifying data integrity and confidentiality without compromising system efficiency.
Encryption Protocols

One pivotal aspect revolves around the adoption of robust encryption protocols to obfuscate critical data during transmission and storage. Implementing industry-standard cryptographic algorithms fortifies the system against unauthorized access attempts and data breaches. Furthermore, integrating multifactor authentication mechanisms adds an additional layer of security, bolstering the overall resilience against potential threats.
Access Control Mechanisms

Another vital consideration pertains to the implementation of stringent access control mechanisms to regulate user privileges and limit unauthorized access to sensitive resources. By delineating access rights based on user roles and implementing granular permissions, organizations can mitigate the risk of unauthorized data manipulation or extraction. Employing robust authentication mechanisms, such as biometric verification or token-based authentication, enhances the overall security posture of the system.
| Aspect | Strategy |
|---|---|
| Encryption Protocols | Implement industry-standard cryptographic algorithms |
| Access Control Mechanisms | Enforce stringent access control policies and granular permissions |