
In the realm of digital infrastructure, there exists a pivotal nexus where seamless communication converges with precise control, empowering networks to transcend limitations and embrace boundless potential.
Embracing the evolution of modern connectivity architecture, this insightful exploration delves into the intricate framework that orchestrates wireless networks with finesse and efficiency, laying the groundwork for unparalleled performance and reliability.
Unlocking the capabilities inherent in sophisticated networking apparatus, this discourse navigates through the intricacies of a foundational document that elucidates the prowess and functionality encapsulated within the heart of contemporary connectivity systems.
Exploring the Core Features of 5520 Wireless Controller Documentation

In this section, we delve into the fundamental aspects encapsulated within the comprehensive documentation for the 5520 wireless controller. Highlighting its pivotal functionalities and intricate specifications, we navigate through the essence of this robust technological apparatus.
Unveiling Operational Capabilities

Embark on a journey to uncover the operational prowess embedded within the core framework of this cutting-edge controller. From its seamless integration mechanisms to its adept management functionalities, explore how it orchestrates the wireless landscape with finesse.
Deciphering Technical Attributes
Delve into the intricate tapestry of technical attributes that define the essence of the 5520 wireless controller documentation. From network optimization methodologies to security protocols, unravel the layers of sophistication underpinning its operational architecture.
Understanding the Architecture and Scalability

In this section, we delve into the fundamental framework and expansibility aspects of the system, exploring its intricate design and ability to grow and adapt. We’ll dissect the underlying structure, elucidating its core components and how they interconnect to facilitate seamless operations at varying scales.
The Blueprint: Deciphering the Framework
Before delving into the intricacies of scalability, it’s paramount to comprehend the architectural blueprint upon which the system is built. This entails unraveling the hierarchical arrangement of components, their functions, and the synergy between them. Through this lens, we gain insight into the system’s inherent flexibility and resilience, laying the groundwork for future expansion.
Scalability Unveiled: Navigating Growth Horizons
Scalability serves as the cornerstone of any robust system, dictating its ability to evolve alongside burgeoning demands. Here, we examine the scalability paradigms embedded within the architecture, assessing its capacity to accommodate increasing workloads without compromising performance or stability. Through a comprehensive analysis of scalability mechanisms, we uncover strategies for seamless expansion, empowering the system to thrive in dynamic environments.
| Aspect | Key Features |
|---|---|
| Modularity | Granular componentization facilitates modular upgrades and enhancements. |
| Elasticity | Dynamically adjusts resource allocation to meet fluctuating demands, ensuring optimal utilization. |
| Redundancy | Redundant pathways and failover mechanisms bolster resilience, mitigating potential points of failure. |
| Interoperability | Seamless integration with diverse environments and protocols fosters interoperability and future-proofing. |
Examining Security Protocols and Compliance

In this segment, we delve into the intricacies of safeguarding network integrity and ensuring adherence to regulatory standards. Our exploration navigates through the robust measures employed to fortify system defenses and uphold regulatory requirements, fostering a secure operational environment.
Understanding Security Protocols
Before delving into compliance frameworks, it’s imperative to grasp the foundation of security protocols. These protocols encompass a spectrum of methodologies and encryption standards designed to thwart unauthorized access, mitigate risks, and preserve data confidentiality. Through stringent authentication mechanisms and encryption algorithms, security protocols erect formidable barriers against potential threats.
Navigating Compliance Landscapes
Compliance stands as a cornerstone in contemporary network governance, dictating adherence to a myriad of regulatory mandates and industry standards. Navigating this intricate terrain necessitates a comprehensive understanding of regulatory frameworks such as GDPR, HIPAA, and PCI DSS. Compliance initiatives entail meticulous documentation, regular audits, and proactive measures to ensure alignment with evolving regulatory landscapes.
- Explore the intersection of security protocols and regulatory compliance.
- Unravel the nuances of encryption standards and authentication mechanisms.
- Navigate through regulatory frameworks such as GDPR, HIPAA, and PCI DSS.
- Examine the significance of proactive measures in maintaining compliance.
Unlocking Performance Enhancements and Management Capabilities
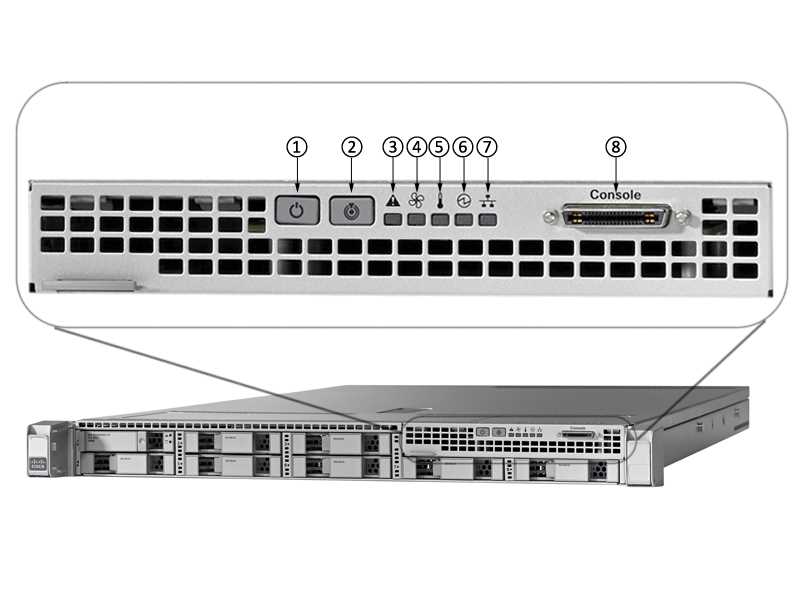
In this section, we delve into the myriad ways to elevate operational efficiency and streamline administrative tasks, fostering a seamless user experience and optimizing network functionalities. By harnessing innovative features and advanced functionalities, we empower administrators to unleash the full potential of their network infrastructure, driving productivity and facilitating dynamic management.
- Maximizing Operational Efficiency: Explore cutting-edge tools and techniques designed to augment network performance, ensuring swift data transmission and uninterrupted connectivity.
- Enhancing Scalability and Flexibility: Discover scalable solutions that adapt to evolving network demands, enabling seamless expansion and integration of additional resources without compromising performance.
- Streamlining Management Processes: Streamline administrative workflows through intuitive interfaces and automated processes, simplifying configuration, monitoring, and troubleshooting tasks for enhanced productivity.
- Optimizing Resource Allocation: Employ dynamic resource allocation strategies to allocate bandwidth and prioritize network traffic, optimizing utilization and ensuring optimal performance for critical applications.
- Enabling Secure Access and Compliance: Implement robust security protocols and compliance measures to safeguard sensitive data and mitigate potential threats, ensuring regulatory compliance and fostering a secure networking environment.
By leveraging these capabilities, organizations can unlock new levels of efficiency and agility, empowering them to adapt to evolving business requirements and stay ahead in today’s dynamic digital landscape.