Embark on a journey through the realm of cutting-edge networking technology, where connectivity meets innovation in a seamless blend of form and function. Explore the dynamic landscape of 2n IP solutions, where every component is meticulously crafted to redefine the standards of communication.
Discover the power of connectivity as we delve into the intricacies of next-generation networking. Unveil the hidden capabilities that lie beneath the surface, as we navigate through the myriad possibilities awaiting within the realm of 2n IP technology.
Empower your network with the latest advancements in IP infrastructure, where reliability, efficiency, and security converge to propel your operations to new heights. Join us as we unravel the tapestry of features and functionalities, painting a picture of unparalleled performance and versatility.
Exploring the Characteristics of 2n IP Verso Documentation
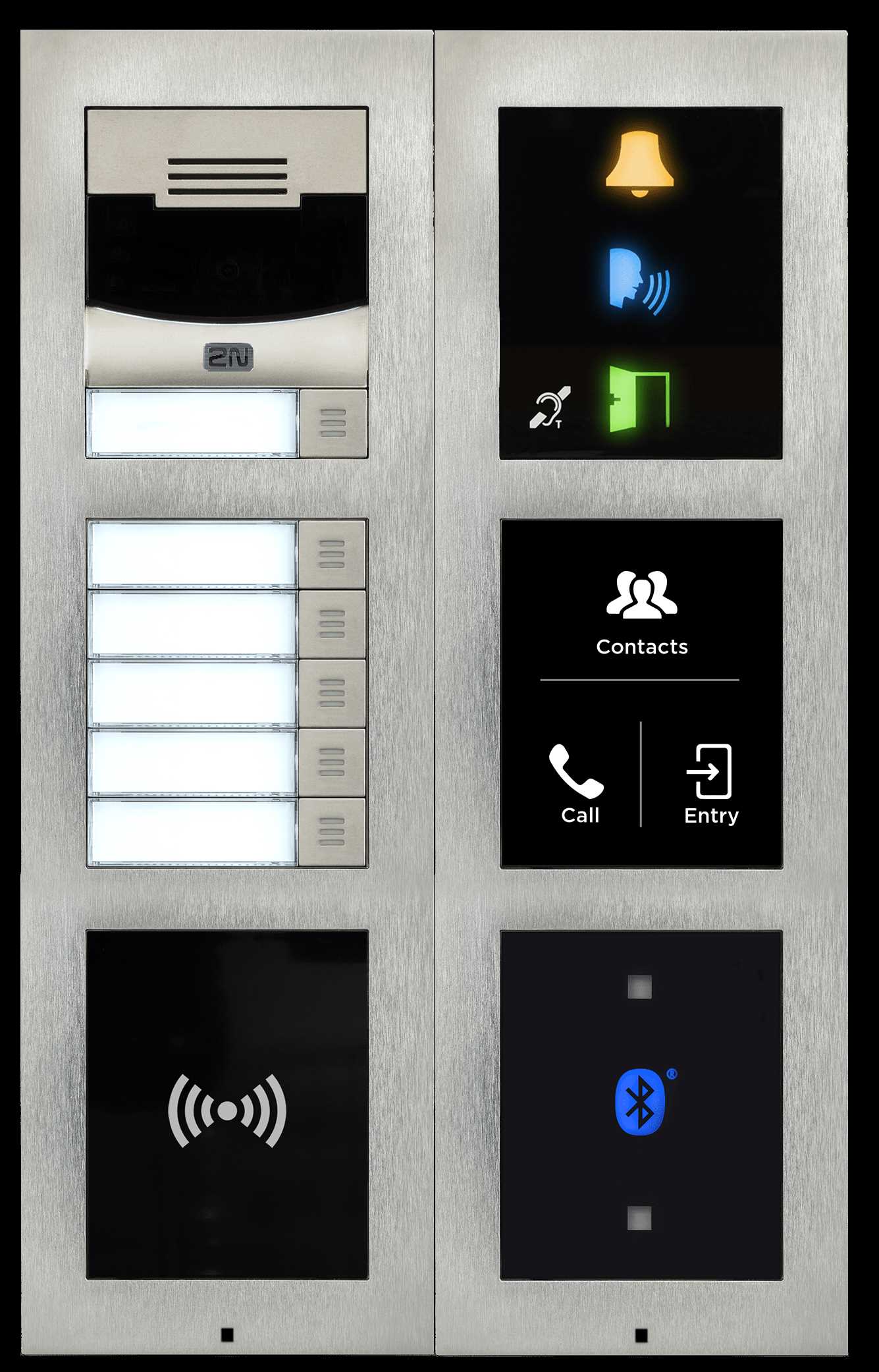
In this section, we delve into the myriad features and functionalities encapsulated within the documentation accompanying the 2n IP Verso system. From its comprehensive array of specifications to its detailed schematics, this exploration aims to provide a nuanced understanding of the capabilities embedded within.
- Comprehensive Specifications: Unveiling a wealth of technical details and performance metrics, the documentation furnishes users with a thorough overview of the device’s capabilities.
- Elaborate Configurations: Offering insights into various configurations and setups, the documentation serves as a guide for users to tailor the system according to their specific requirements.
- Integration Guidelines: Presenting integration methodologies and compatibility considerations, the documentation facilitates seamless integration of the 2n IP Verso into existing systems and networks.
- Advanced Functionality: Detailing advanced features and functionalities, the documentation empowers users to leverage the full potential of the 2n IP Verso, enhancing security and communication protocols.
- Installation and Maintenance Insights: Providing step-by-step installation guides and maintenance protocols, the documentation ensures a smooth deployment process and sustained operational efficiency.
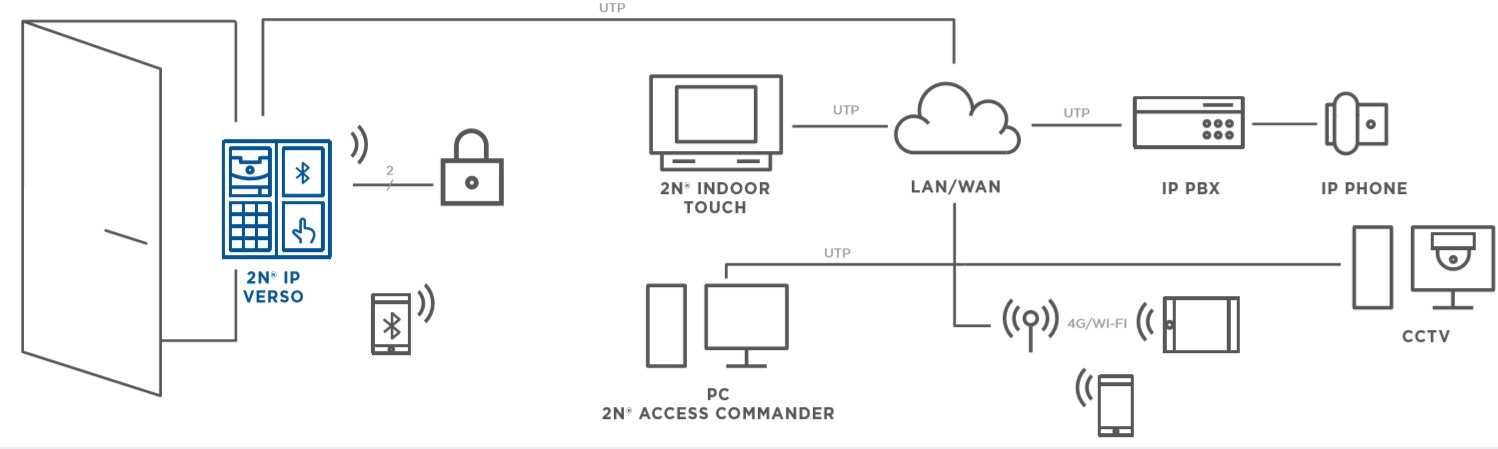
Understanding Connectivity Options

In the realm of network infrastructure, comprehending the myriad connectivity options is paramount. It’s not just about selecting the right cables and interfaces; it’s about forging pathways for seamless communication, ensuring interoperability, and optimizing data transmission.
Wired Solutions
- Ethernet: The ubiquitous standard for wired connections, Ethernet offers reliability and speed, facilitating high-bandwidth data transfer.
- Fiber Optics: Leveraging light signals through glass or plastic fibers, fiber optics enable rapid data transmission over long distances with minimal signal degradation.
Wireless Technologies

- Wi-Fi: A cornerstone of modern connectivity, Wi-Fi liberates devices from physical tethering, providing flexibility and mobility within a designated range.
- Bluetooth: Primarily used for short-range connections, Bluetooth is ideal for peripherals like keyboards, mice, and audio devices, offering convenience and simplicity.
Each option presents distinct advantages and considerations, influencing decisions in network architecture and device compatibility. Understanding these connectivity solutions empowers users to construct robust, efficient networks tailored to their specific needs.
Security Features and Protocols

In the realm of safeguarding sensitive information and ensuring the integrity of data transmission, our IP module boasts a robust array of security measures and protocols. This section delves into the protective mechanisms and communication frameworks implemented within the module.
- Data Encryption: Ensuring confidentiality, data encryption transforms information into an unreadable format, thwarting unauthorized access.
- Authentication Mechanisms: Authentication protocols validate the identities of users or devices seeking access, preventing unauthorized entry.
- Firewall Integration: Employing firewall technologies, the module fortifies against external threats by filtering network traffic based on predetermined security rules.
- Intrusion Detection Systems (IDS): Vigilant against malicious activities, IDS monitors network traffic for suspicious patterns, triggering alerts upon detection of potential breaches.
- Secure Boot: Initiating a trusted boot process, secure boot ensures that only authenticated software components are executed during startup, mitigating the risk of tampering or malware injection.
By amalgamating these security features and adhering to stringent protocols, our IP module guarantees a shielded environment for data exchange and operation, instilling confidence in the integrity and confidentiality of transmitted information.
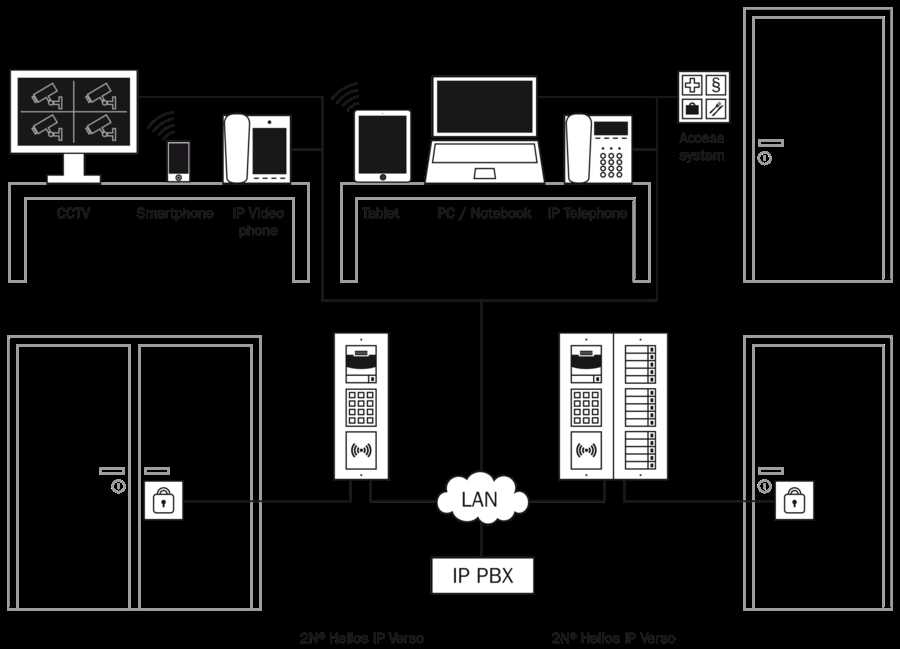
Customization and Integration Possibilities

Exploring the myriad of ways to tailor and seamlessly incorporate the 2n IP verso into existing infrastructures unveils a landscape rich with potential. This section delves into the diverse avenues for customization and integration, highlighting the adaptability and versatility of this technology. Whether seeking to harmonize with current systems or innovate new solutions, the 2n IP verso offers a spectrum of opportunities to enhance functionality and streamline operations.